Algorithms, Free Full-Text
Por um escritor misterioso
Last updated 15 março 2025
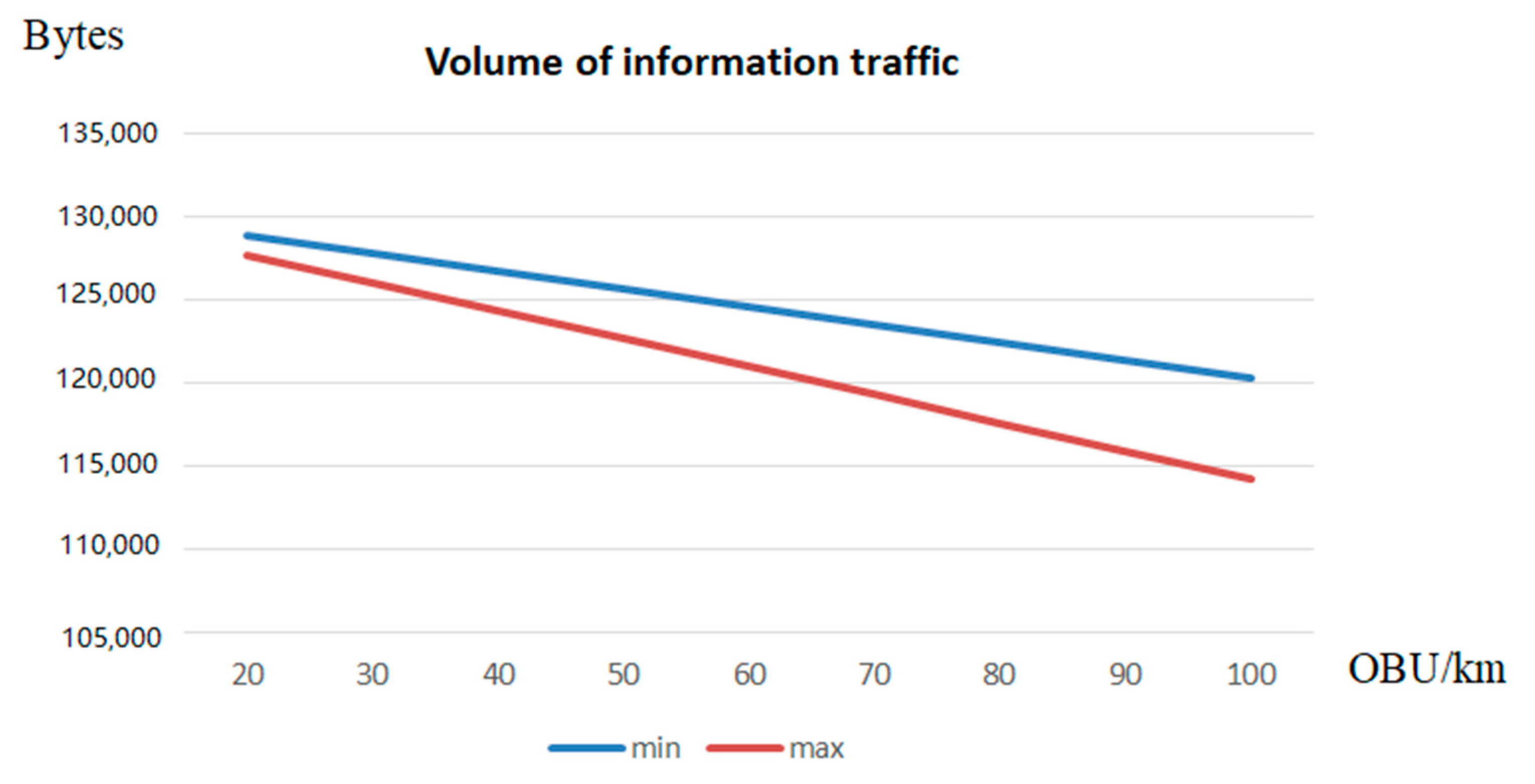
Authentication protocols are expanding their application scope in wireless information systems, among which are low-orbit satellite communication systems (LOSCS) for the OneWeb space Internet, automatic object identification systems using RFID, the Internet of Things, intelligent transportation systems (ITS), Vehicular Ad Hoc Network (VANET). This is due to the fact that authentication protocols effectively resist a number of attacks on wireless data transmission channels in these systems. The main disadvantage of most authentication protocols is the use of symmetric and asymmetric encryption systems to ensure high cryptographic strength. As a result, there is a problem in delivering keys to the sides of the prover and the verifier. At the same time, compromising of keys will lead to a decrease in the level of protection of the transmitted data. Zero-knowledge authentication protocols (ZKAP) are able to eliminate this disadvantage. However, most of these protocols use multiple rounds to authenticate the prover. Therefore, ZKAP, which has minimal time costs, is developed in the article. A scheme for adapting protocol parameters has been developed in this protocol to increase its efficiency. Reductions in the level of confidentiality allow us to reduce the time spent on the execution of the authentication protocol. This increases the volume of information traffic. At the same time, an increase in the confidentiality of the protocol entails an increase in the time needed for authentication of the prover, which reduces the volume of information traffic. The FPGA Artix-7 xc7a12ticsg325-1L was used to estimate the time spent implementing the adaptive ZKAP protocol. Testing was performed for 32- and 64-bit adaptive authentication protocols.

Screening for extranodal extension in HPV-associated oropharyngeal

Algorithms full tutorial

Centrum Wiskunde & Informatica: Local improvement algorithms for a
An Overview of QuickSort Algorithm, by Harshil Patel

Free Algorithms Book

Missing Letters, Intermediate Algorithm Scripting

SOLUTION: Design and analysis of algorithms handwritten notes pdf

ACLS algorithm overview

Industrial Algorithms
Learn About Algorithms and Data Structures in this Free 6-hour Course

Algorithms, Part I
Recomendado para você
-
 Roblox Project New World Codes (September 2021)15 março 2025
Roblox Project New World Codes (September 2021)15 março 2025 -
 Codes, Project New world Wiki15 março 2025
Codes, Project New world Wiki15 março 2025 -
 NEW CODES* PROJECT NEW WORLD ROBLOX15 março 2025
NEW CODES* PROJECT NEW WORLD ROBLOX15 março 2025 -
![Haze Piece Codes [Dragon] (December 2023) - Pro Game Guides](https://progameguides.com/wp-content/uploads/2022/12/roblox-project-new-world-code-help.jpg?w=1024&resize=1200%2C675) Haze Piece Codes [Dragon] (December 2023) - Pro Game Guides15 março 2025
Haze Piece Codes [Dragon] (December 2023) - Pro Game Guides15 março 2025 -
 Will Rogers World Airport - Wikipedia15 março 2025
Will Rogers World Airport - Wikipedia15 março 2025 -
 Gretchen Whitmer announces nearly 300 new jobs in Grand Blanc Township15 março 2025
Gretchen Whitmer announces nearly 300 new jobs in Grand Blanc Township15 março 2025 -
 Top 10 Trending Metaverse Projects of The Week - NFT News Pro15 março 2025
Top 10 Trending Metaverse Projects of The Week - NFT News Pro15 março 2025 -
Combined Experimental and Mechanoelastic Modeling Studies on the Low-Spin Stabilized Mixed Crystals of 3D Oxalate-Based Coordination Materials15 março 2025
-
 FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)15 março 2025
FUTURE CODES!! *NEW* ROBLOX PROJECT NEW WORLD CODES 2023! (135K CODE)15 março 2025 -
 ALL NEW *FREE SPINS* CODES in PROJECT NEW WORLD CODES! (Roblox Project New World Codes)15 março 2025
ALL NEW *FREE SPINS* CODES in PROJECT NEW WORLD CODES! (Roblox Project New World Codes)15 março 2025
você pode gostar
-
 Review: GTA 5 faz história e vira um dos melhores games - BITS Caverna - Por Oficina dos Bits15 março 2025
Review: GTA 5 faz história e vira um dos melhores games - BITS Caverna - Por Oficina dos Bits15 março 2025 -
 Full The Lord of the Rings: Gollum Gameplay Walkthrough Leaks Online - Insider Gaming15 março 2025
Full The Lord of the Rings: Gollum Gameplay Walkthrough Leaks Online - Insider Gaming15 março 2025 -
Camiseta Camisa Dragon Ball Super Goku SSJ Blue15 março 2025
-
 My girlfriend rarely gets to come visit me, and doesnt have good Wi-Fi to play online games at her school. She has been watching me play Skyrim a lot so I did15 março 2025
My girlfriend rarely gets to come visit me, and doesnt have good Wi-Fi to play online games at her school. She has been watching me play Skyrim a lot so I did15 março 2025 -
Brookhaven 🏡RP [Free Admin] [UPD!] - Roblox15 março 2025
-
 Manchester City x Dortmund: onde assistir, horário e escalações do jogo pela Champions League - Lance!15 março 2025
Manchester City x Dortmund: onde assistir, horário e escalações do jogo pela Champions League - Lance!15 março 2025 -
 Banned r EDP goes viral on TikTok with new account after Super Bowl - Dexerto15 março 2025
Banned r EDP goes viral on TikTok with new account after Super Bowl - Dexerto15 março 2025 -
 Mustang Arms .357 Magnum, Deus Ex Wiki15 março 2025
Mustang Arms .357 Magnum, Deus Ex Wiki15 março 2025 -
 10 Secret Facts Of Avengers: Endgame You Should Know15 março 2025
10 Secret Facts Of Avengers: Endgame You Should Know15 março 2025 -
Wolfenstein: The New Order - PlayStation 4, PlayStation 415 março 2025


![Brookhaven 🏡RP [Free Admin] [UPD!] - Roblox](https://tr.rbxcdn.com/0416d7b6162502313460fc7660c63ad5/500/280/Image/Jpeg)
