Cryptojacking: Understanding and defending against cloud compute
Por um escritor misterioso
Last updated 22 abril 2025

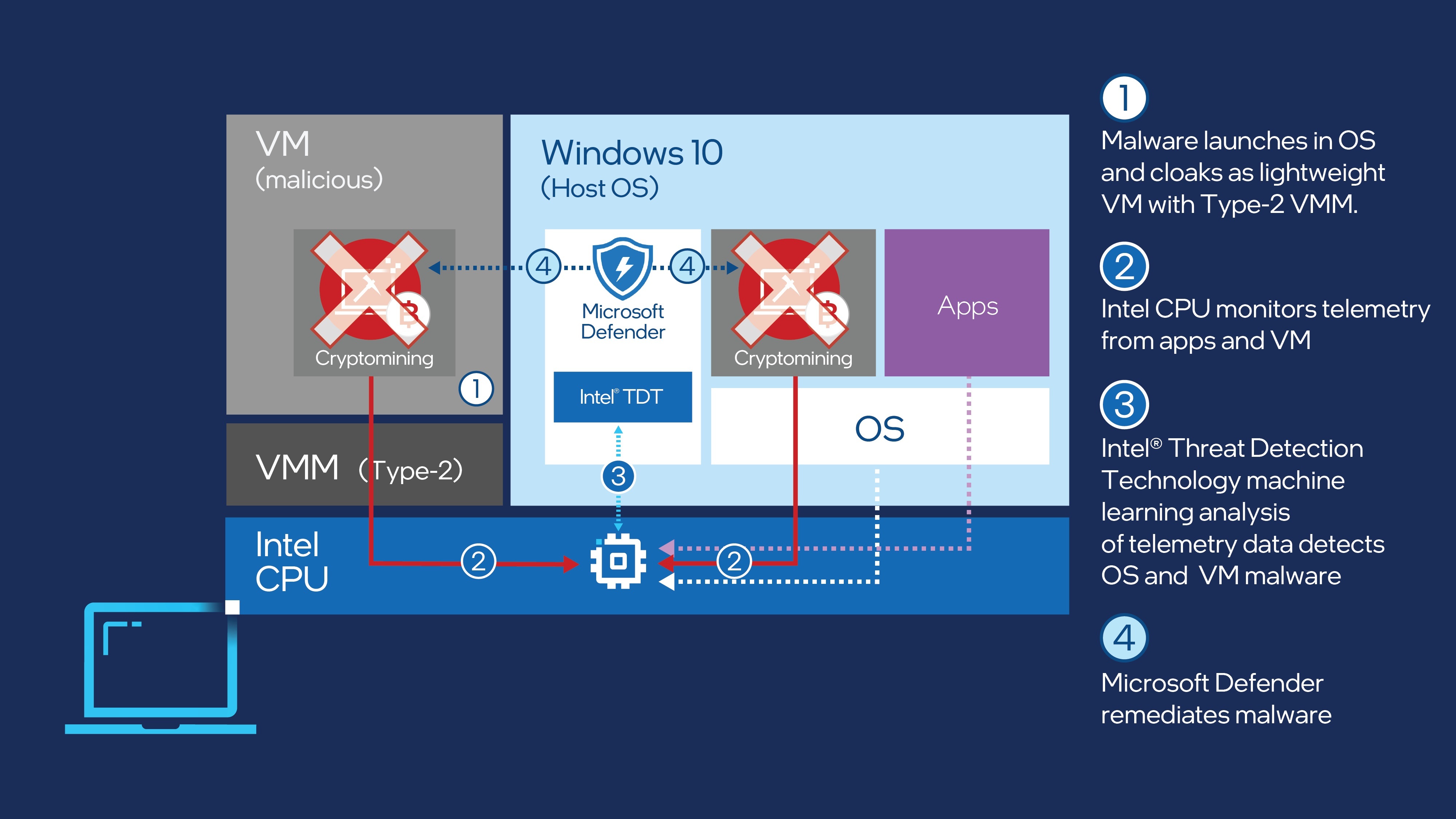
Intel Collaborates with Microsoft against Cryptojacking
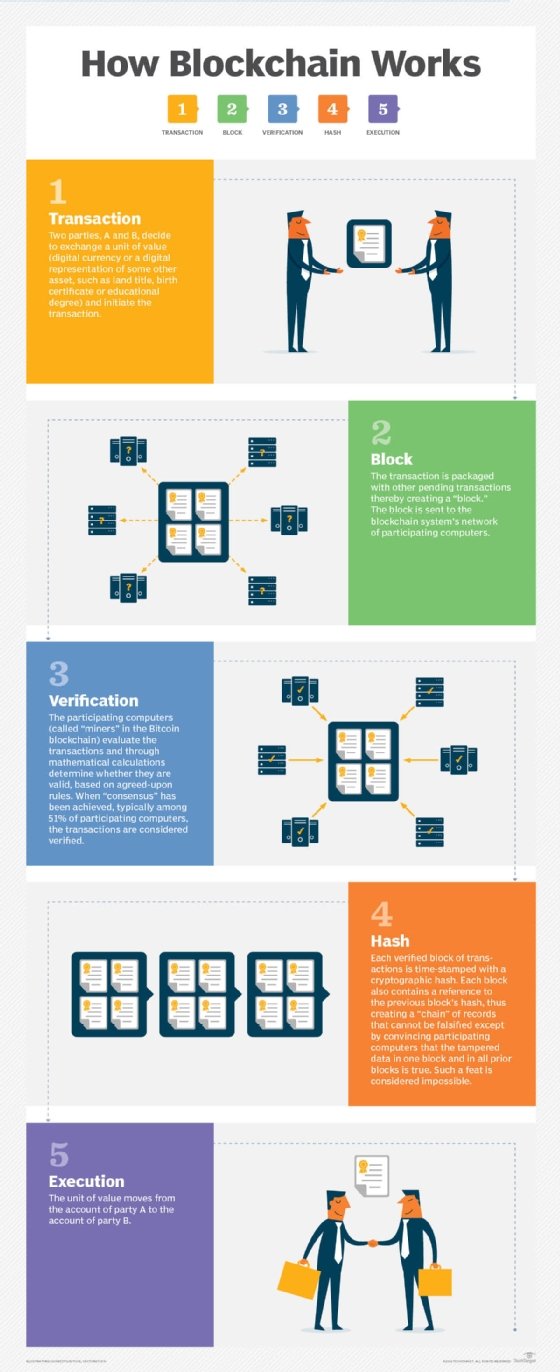
What is Cryptojacking? Detection and Preventions Techniques

How to Protect Yourself from Cryptojacking
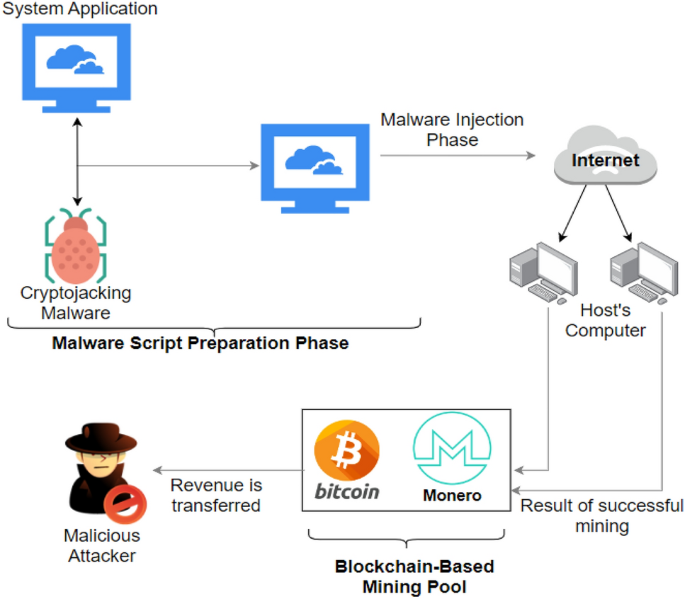
A deep learning approach for host-based cryptojacking malware
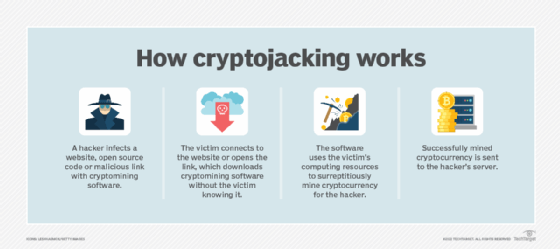
What is Cryptojacking? Detection and Preventions Techniques

Intel Collaborates with Microsoft against Cryptojacking

Cryptojacking - 5 Ways To Prevent Attacks
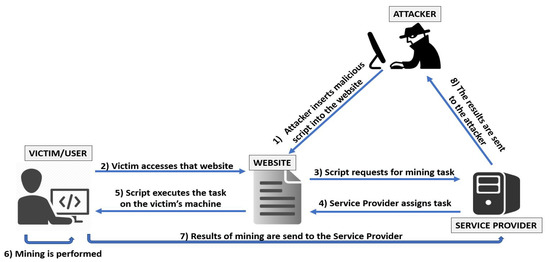
Applied Sciences, Free Full-Text
Cryptojacking - 5 Ways To Prevent Attacks

Defend Against Cloud Malware: Types, Prevention, and Training
Recomendado para você
-
 Sudden Attack22 abril 2025
Sudden Attack22 abril 2025 -
 Russia Expands Its War on Ukraine — to Global Food Supplies22 abril 2025
Russia Expands Its War on Ukraine — to Global Food Supplies22 abril 2025 -
 SUDDEN ATTACK 202322 abril 2025
SUDDEN ATTACK 202322 abril 2025 -
 Sudden attack 2023 i922 abril 2025
Sudden attack 2023 i922 abril 2025 -
 Why the tunnels under Gaza pose a major problem for Israel's22 abril 2025
Why the tunnels under Gaza pose a major problem for Israel's22 abril 2025 -
 Wild otter attack leads to woman being airlifted to hospital, 222 abril 2025
Wild otter attack leads to woman being airlifted to hospital, 222 abril 2025 -
 7 Reasons Global Attacks Will Rise Significantly in 202322 abril 2025
7 Reasons Global Attacks Will Rise Significantly in 202322 abril 2025 -
.png) Global Chess League: Schedule and unique scoring system announced22 abril 2025
Global Chess League: Schedule and unique scoring system announced22 abril 2025 -
 Oct. 10: First plane with 'advanced' US ammo lands at airbase22 abril 2025
Oct. 10: First plane with 'advanced' US ammo lands at airbase22 abril 2025 -
 Disney Has Box Office Failures With Indiana Jones, Elemental, Ant-Man22 abril 2025
Disney Has Box Office Failures With Indiana Jones, Elemental, Ant-Man22 abril 2025
você pode gostar
-
 Esperança Reeditada22 abril 2025
Esperança Reeditada22 abril 2025 -
 Universos complejos: Multiverso y Metaverso – Entreletras22 abril 2025
Universos complejos: Multiverso y Metaverso – Entreletras22 abril 2025 -
 Fullmetal Alchemist: Brotherhood - Volume 4: Folge 25-32 : Movies & TV22 abril 2025
Fullmetal Alchemist: Brotherhood - Volume 4: Folge 25-32 : Movies & TV22 abril 2025 -
 Bola de Basquete Penalty Fun T1 Xxiii22 abril 2025
Bola de Basquete Penalty Fun T1 Xxiii22 abril 2025 -
juegos de ps4 gratis de 2|Pesquisa do TikTok22 abril 2025
-
![RT] Man this manga deserve more attendtion to it, people usualy](https://i.redd.it/z5z2131dg4h31.jpg) RT] Man this manga deserve more attendtion to it, people usualy22 abril 2025
RT] Man this manga deserve more attendtion to it, people usualy22 abril 2025 -
WhatsApp Messenger - Apps en Google Play22 abril 2025
-
 Mapa Portugal Regiões22 abril 2025
Mapa Portugal Regiões22 abril 2025 -
 TV Anime Absolute Duo ED Theme Believe x Believe / Apple Tea Flavor / 222 abril 2025
TV Anime Absolute Duo ED Theme Believe x Believe / Apple Tea Flavor / 222 abril 2025 -
 Descubra a sua personalidade no jogo: que tipo de jogador é? - Blog de esportes e jogos de computador22 abril 2025
Descubra a sua personalidade no jogo: que tipo de jogador é? - Blog de esportes e jogos de computador22 abril 2025
