How Do MAC Spoofing Attacks Work?
Por um escritor misterioso
Last updated 08 novembro 2024

In this blog, we will go into the complexities of MAC spoofing, analyzing its repercussions and emphasizing the importance of having strong security policies in place.
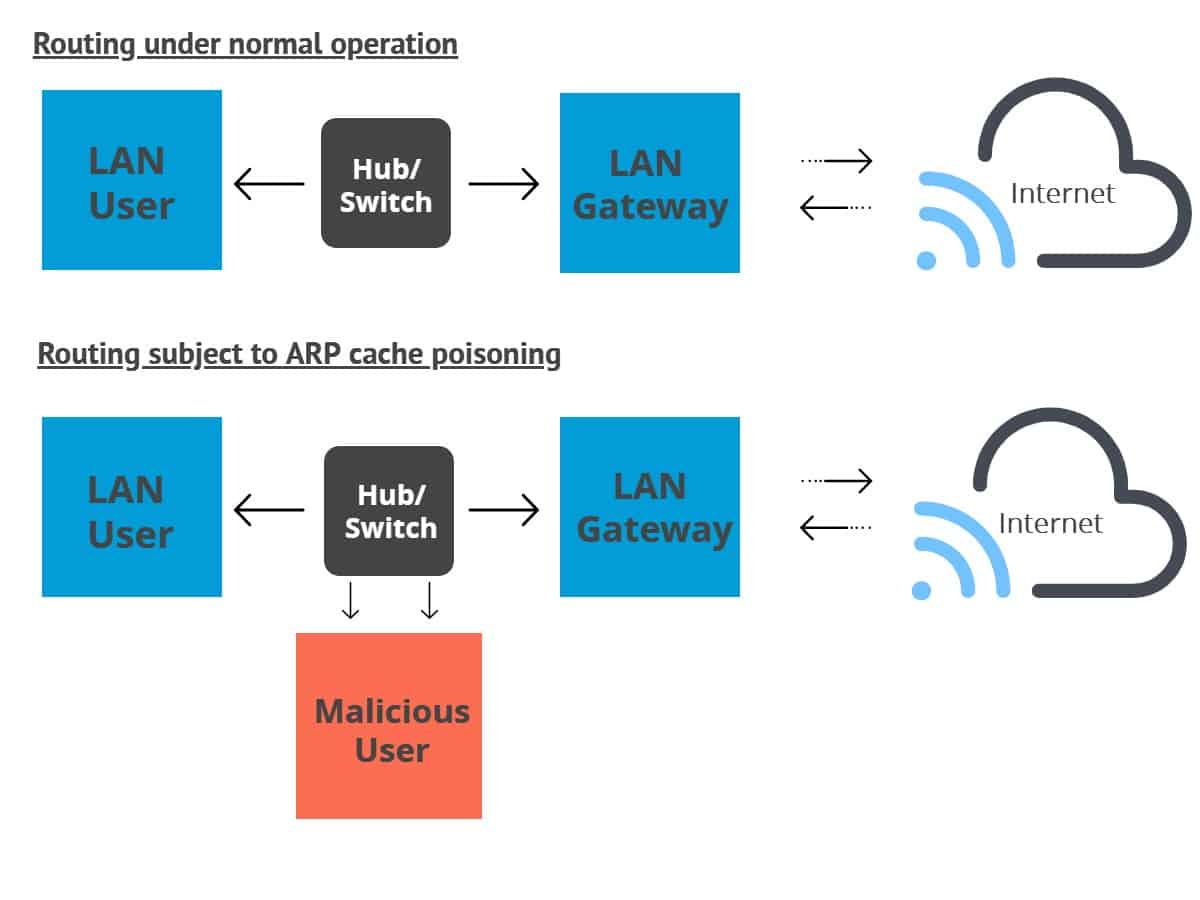
ARP poisoning/spoofing: How to detect & prevent it

What is Address Resolution Protocol (ARP)?
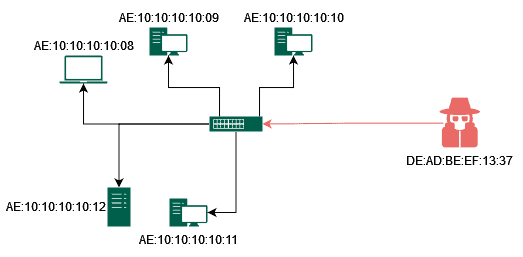
How MAC Flooding and Cloning Attacks Work?
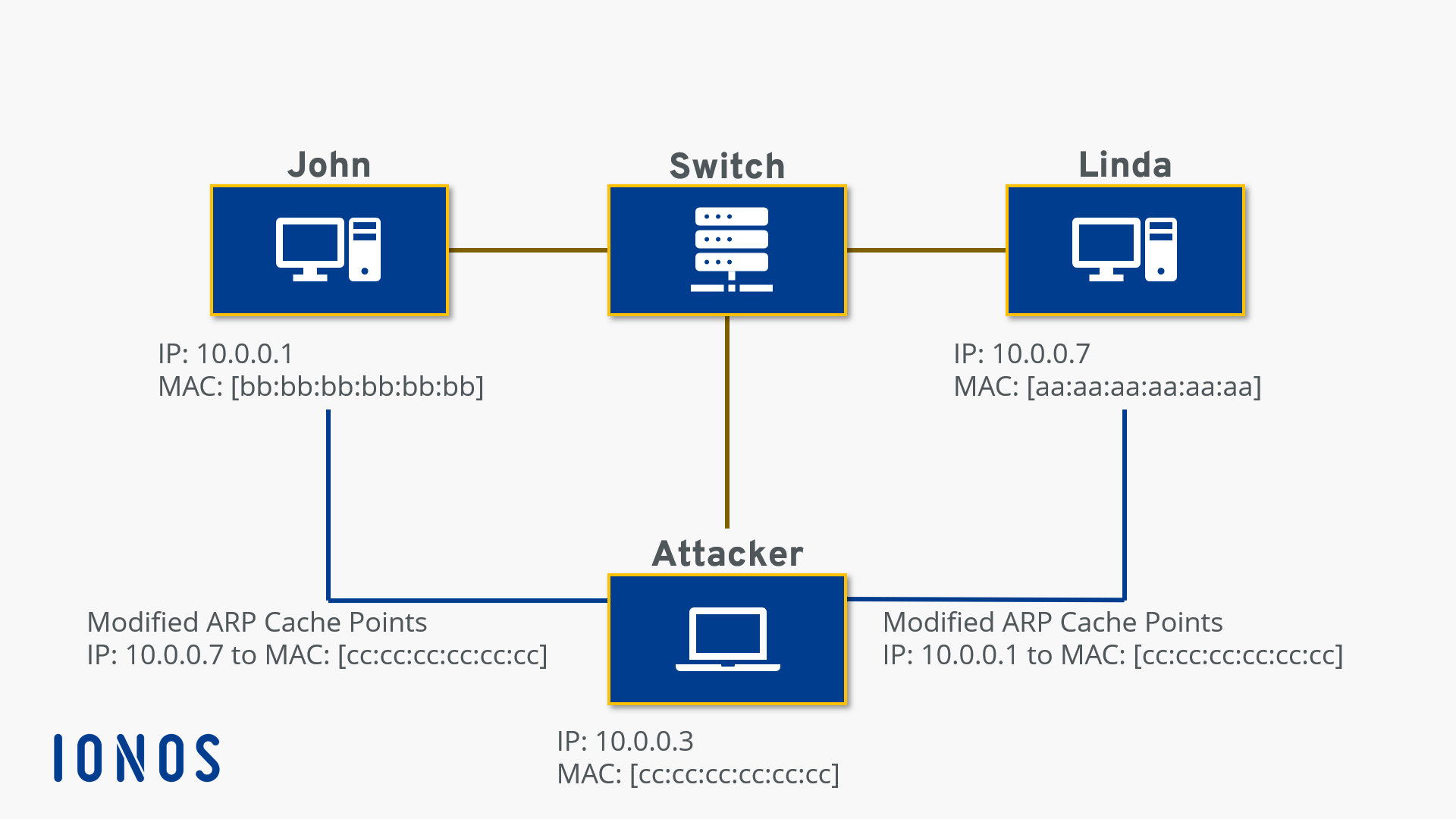
What is ARP Spoofing and how does it work? - IONOS CA
MAC ATTACK: How to Spoof your MAC Address - Electronics For You

How Man-in-the-Middle Attacks work

What is Spoofing?, Examples & Prevention
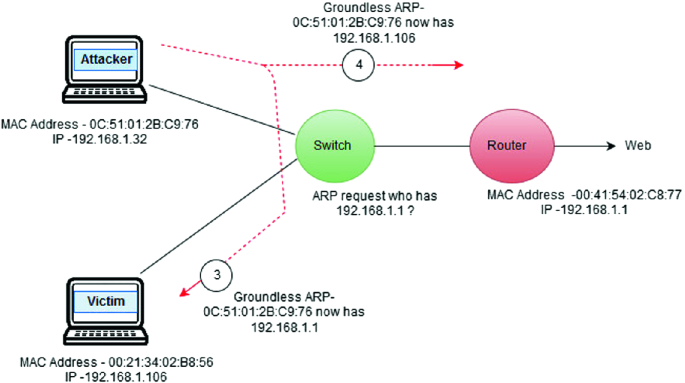
Reliable Monitoring Security System to Prevent MAC Spoofing in Ubiquitous Wireless Network

SSID and MAC address spoofing attack
Recomendado para você
-
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!08 novembro 2024
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!08 novembro 2024 -
 YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub08 novembro 2024
YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub08 novembro 2024 -
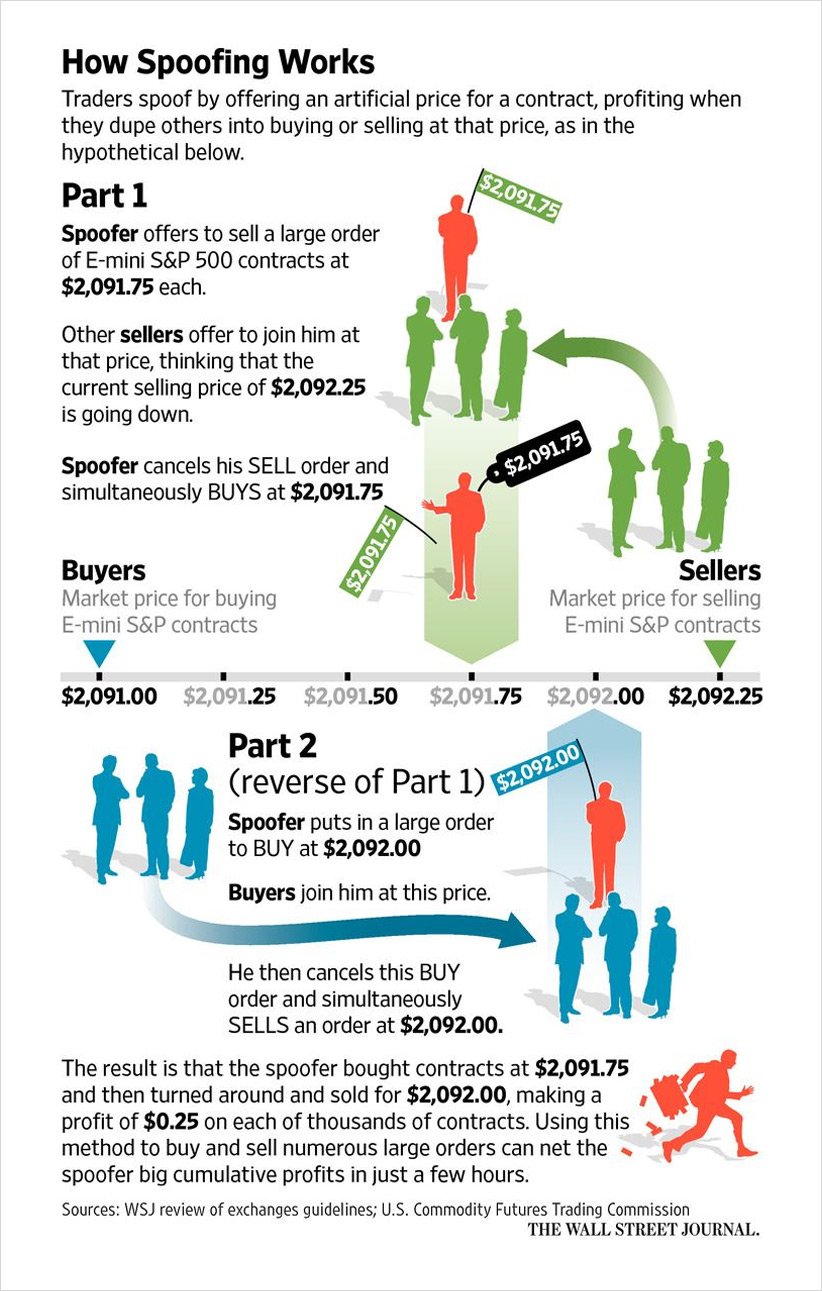 Explaining and Exploring Spoofing - Deribit Insights08 novembro 2024
Explaining and Exploring Spoofing - Deribit Insights08 novembro 2024 -
 Interfacing with CAST Navigation GNSS/INS Simulation Solutions08 novembro 2024
Interfacing with CAST Navigation GNSS/INS Simulation Solutions08 novembro 2024 -
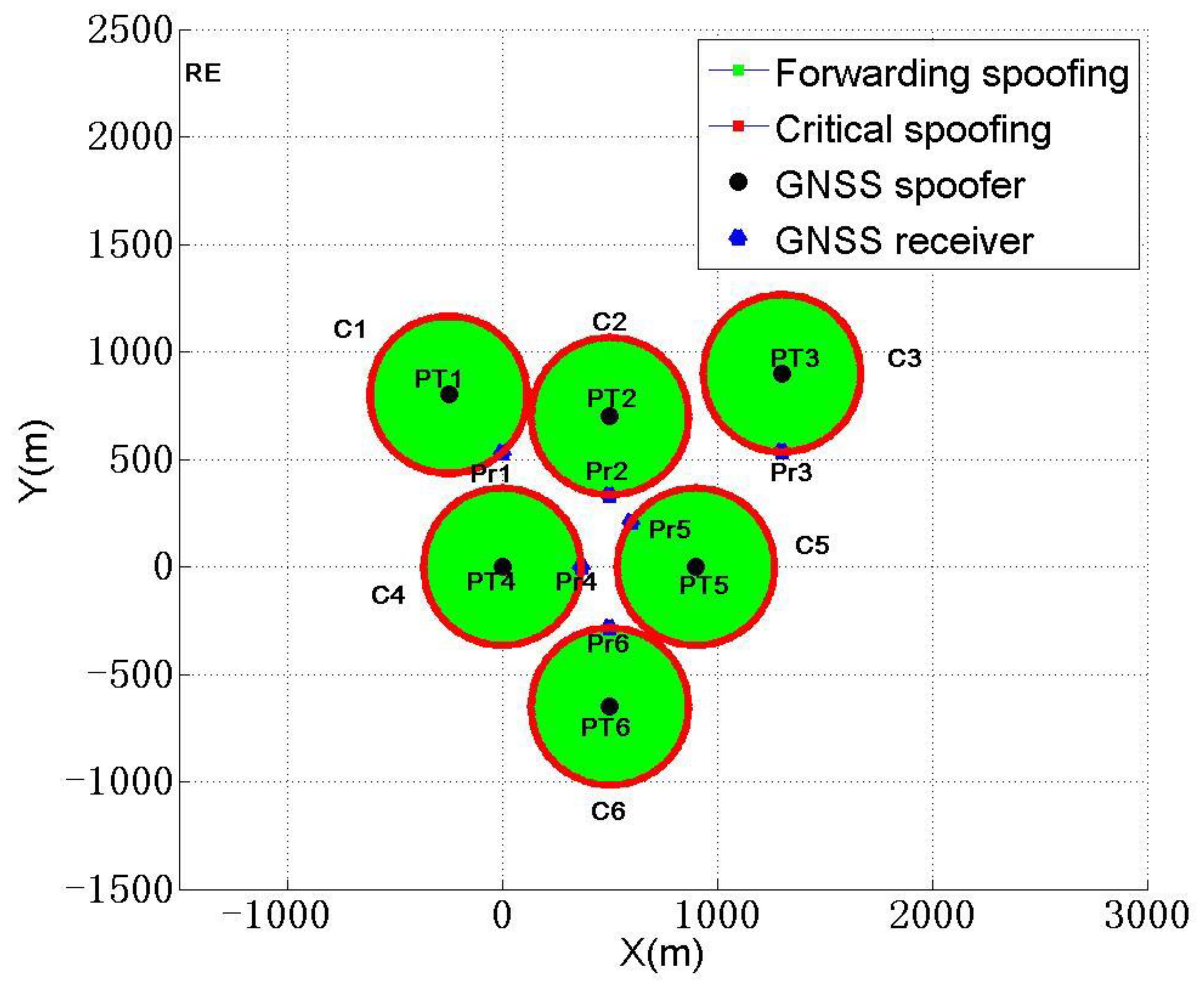 Sensors, Free Full-Text08 novembro 2024
Sensors, Free Full-Text08 novembro 2024 -
Location Guard08 novembro 2024
-
RoDAR the Equaliser08 novembro 2024
-
 Device Fingerprinting - SEON Docs08 novembro 2024
Device Fingerprinting - SEON Docs08 novembro 2024 -
 Precision Digital Webinars08 novembro 2024
Precision Digital Webinars08 novembro 2024 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation08 novembro 2024
Protecting GPS From Spoofers Is Critical to the Future of Navigation08 novembro 2024
você pode gostar
-
 How to Watch Clash of the Titans (1981) outside USA on Max08 novembro 2024
How to Watch Clash of the Titans (1981) outside USA on Max08 novembro 2024 -
Como desenhar o Goku rápido e fácil! . . . . #dragonball #dragonballz08 novembro 2024
-
 Sonic Colors: Rise of the Wisps animated short series launched08 novembro 2024
Sonic Colors: Rise of the Wisps animated short series launched08 novembro 2024 -
 Pokemon GO Shadow Mewtwo raid guide (May 2023): Best counters08 novembro 2024
Pokemon GO Shadow Mewtwo raid guide (May 2023): Best counters08 novembro 2024 -
 The Queen's Gambit - Wallpaper - The Queen's Gambit Wallpaper (43678348) - Fanpop08 novembro 2024
The Queen's Gambit - Wallpaper - The Queen's Gambit Wallpaper (43678348) - Fanpop08 novembro 2024 -
Dr. Stone temporada 2 - Ver todos los episodios online08 novembro 2024
-
 Red Cat cute funny character in doodle cartoon style. Ginger08 novembro 2024
Red Cat cute funny character in doodle cartoon style. Ginger08 novembro 2024 -
.png) gaara naruto08 novembro 2024
gaara naruto08 novembro 2024 -
 Baixe Gênio Quiz 10 no PC08 novembro 2024
Baixe Gênio Quiz 10 no PC08 novembro 2024 -
 ・DioN・ on X: / X08 novembro 2024
・DioN・ on X: / X08 novembro 2024


