Malware analysis Malicious
Por um escritor misterioso
Last updated 26 março 2025
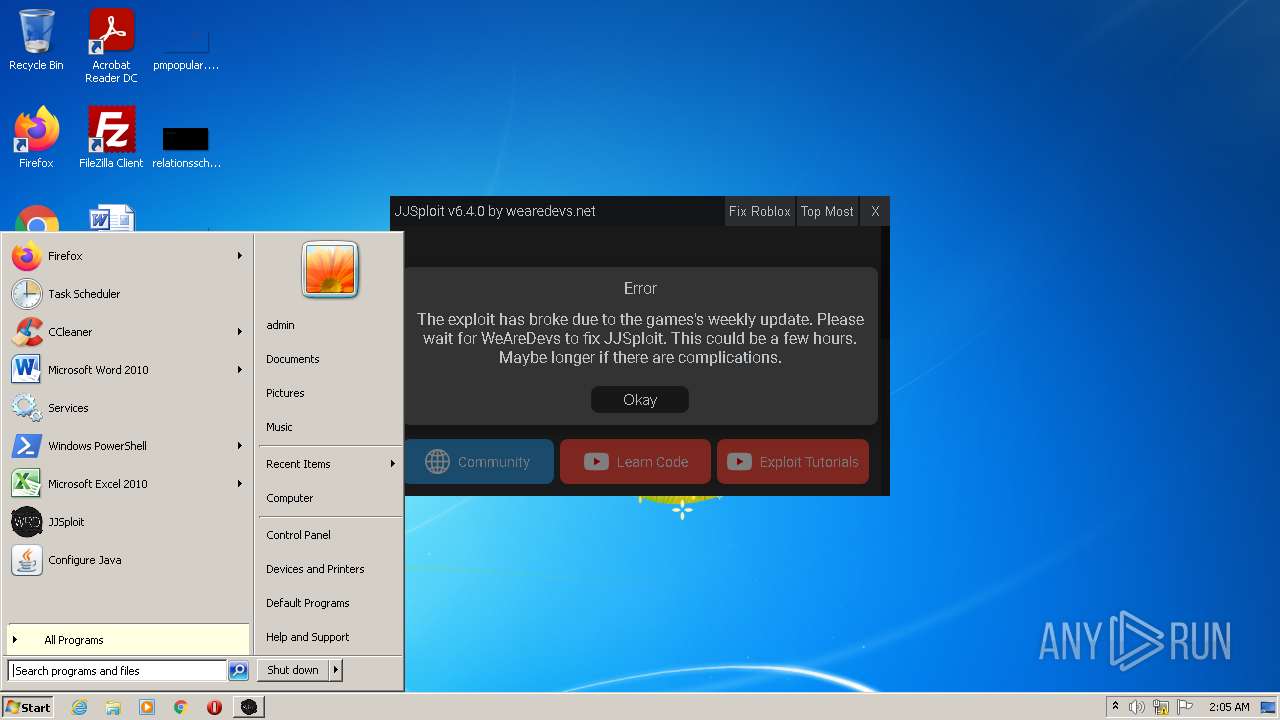

Figure .: Pros and Cons of Malware Analysis Methods

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

Intro to Malware Analysis: What It Is & How It Works - InfoSec Insights

Introduction to Malware Analysis - PatchTheNet

PROUD-MAL: static analysis-based progressive framework for deep unsupervised malware classification of windows portable executable

Practical Malware Analysis: Book review

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Malware Analysis 101: Handling Malicious Software Safely (Lab)

ReversingLabs Malware Lab: Detect, classify, analyze, and respond to malicious files - Help Net Security

Malware Analyst's Cookbook and DVD: Tools and Techniques for Fighting Malicious Code

11 Best Malware Analysis Tools and Their Features
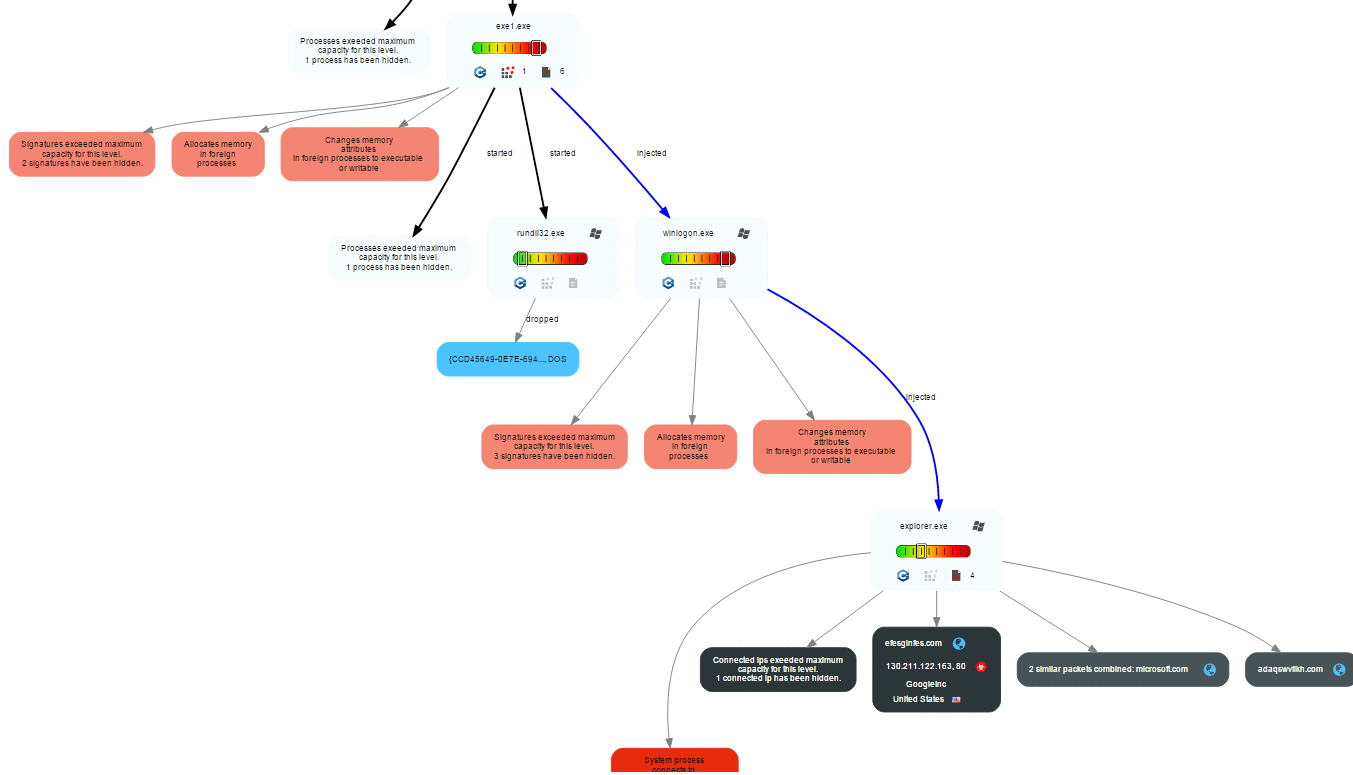
Deep Malware Analysis - Behavior Graph 2.0

Malware Analysis: Steps & Examples - CrowdStrike
Recomendado para você
-
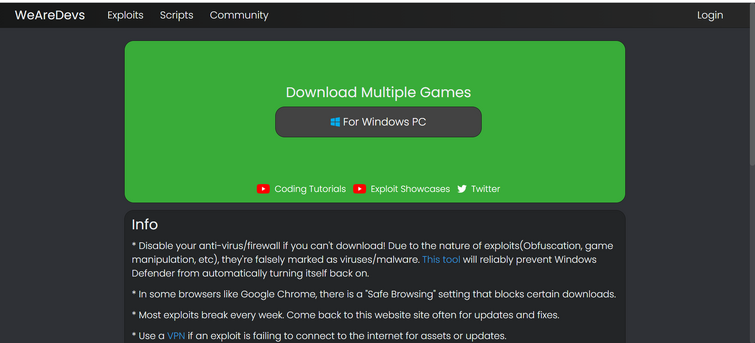
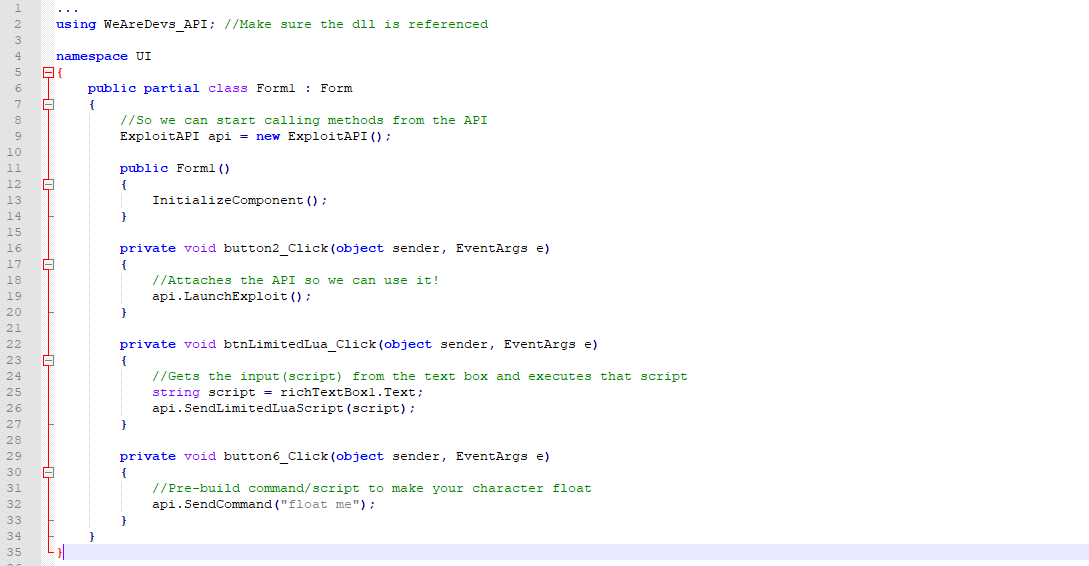 Exploit API C# Documentation & Download - WeAreDevs26 março 2025
Exploit API C# Documentation & Download - WeAreDevs26 março 2025 -
wearedevs.net Competitors - Top Sites Like wearedevs.net26 março 2025
-
GitHub - Windows81/Roblox-Script-Executor-CLI: Command-line interface that uses the WeAreDevs API et al. to run scripts on the Roblox client.26 março 2025
-
2023 Delta exploits for #videos26 março 2025
-
 Roblox Aimbot Script with JJSploit Lua Executor26 março 2025
Roblox Aimbot Script with JJSploit Lua Executor26 março 2025 -
if you kill afk farmers I'm going to beat you /j26 março 2025
-
 Malware analysis Malicious activity26 março 2025
Malware analysis Malicious activity26 março 2025 -
 Malware analysis Malicious activity26 março 2025
Malware analysis Malicious activity26 março 2025 -
roblox #fyo #hack #script #jjsploit #wearedevs Like and Comment26 março 2025
-
 GitHub - Professor-Puddle/Roblox-Executor: An awesome Roblox26 março 2025
GitHub - Professor-Puddle/Roblox-Executor: An awesome Roblox26 março 2025
você pode gostar
-
 Livro gambito da dama em Promoção na Americanas26 março 2025
Livro gambito da dama em Promoção na Americanas26 março 2025 -
![AmiAmi [Character & Hobby Shop] Honor of Kings Mermaid Doria 1/7 Complete Figure(Pre-order)](https://img.amiami.com/images/product/main/234/FIGURE-162449.jpg) AmiAmi [Character & Hobby Shop] Honor of Kings Mermaid Doria 1/7 Complete Figure(Pre-order)26 março 2025
AmiAmi [Character & Hobby Shop] Honor of Kings Mermaid Doria 1/7 Complete Figure(Pre-order)26 março 2025 -
 NBA Divulga Calendário de Jogos em Orlando para a Temporada 201726 março 2025
NBA Divulga Calendário de Jogos em Orlando para a Temporada 201726 março 2025 -
 Xbox Series X vs Xbox Series S: which Xbox console is right for you? - Mirror Online26 março 2025
Xbox Series X vs Xbox Series S: which Xbox console is right for you? - Mirror Online26 março 2025 -
 Does anyone want me to Edit their OC? : r/GachaClub26 março 2025
Does anyone want me to Edit their OC? : r/GachaClub26 março 2025 -
 Lost Ark: game é adiado na hora do lançamento!26 março 2025
Lost Ark: game é adiado na hora do lançamento!26 março 2025 -
 Movie, Crossover, Luca Paguro, Alberto Scorfano, Giulia Marcovaldo, Luca (Movie), HD wallpaper26 março 2025
Movie, Crossover, Luca Paguro, Alberto Scorfano, Giulia Marcovaldo, Luca (Movie), HD wallpaper26 março 2025 -
 Assistir Kage no Jitsuryokusha ni Naritakute! 2nd Season ep 3 - Anitube26 março 2025
Assistir Kage no Jitsuryokusha ni Naritakute! 2nd Season ep 3 - Anitube26 março 2025 -
Jogo de Cartas: Uno, Pokémon, Naruto e Mais - Ri Happy26 março 2025
-
 RugbyCast #58 em ritmo de finais de Copa do Mundo, Super 12 e BR XV! – Confederação Brasileira de Rugby26 março 2025
RugbyCast #58 em ritmo de finais de Copa do Mundo, Super 12 e BR XV! – Confederação Brasileira de Rugby26 março 2025