Malware analysis Malicious activity
Por um escritor misterioso
Last updated 10 fevereiro 2025
10 Best Antivirus Software in 2023: Windows, Android, iOS, Mac

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1

Nextron Systems - We Detect Hackers
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
Malware analysis tt.7z Malicious activity

Routers Roasting on an Open Firewall: the KV-botnet Investigation

StopRansomware: Rhysida Ransomware

Malware Analysis: Steps & Examples - CrowdStrike

What to Include in a Malware Analysis Report

Playbook of the Week: Malware Investigation and Response - Palo
Recomendado para você
-
 Solved abs 4 pdf free.pd' (SECURED) Adobe Acrobat Pro DC10 fevereiro 2025
Solved abs 4 pdf free.pd' (SECURED) Adobe Acrobat Pro DC10 fevereiro 2025 -
 William Dalrymple on X: @halleyji Have a look at this and see what you think- Nana: The “Original” Goddess on the Lion - / X10 fevereiro 2025
William Dalrymple on X: @halleyji Have a look at this and see what you think- Nana: The “Original” Goddess on the Lion - / X10 fevereiro 2025 -
global-english-2-learner-pdfcoffee.com : Free Download, Borrow, and Streaming : Internet Archive10 fevereiro 2025
-
 is pdf coffee safe|TikTok Search10 fevereiro 2025
is pdf coffee safe|TikTok Search10 fevereiro 2025 -
 Coffee Warms the Soul Svg/png/dxf/eps/pdf Coffee Svg Coffee10 fevereiro 2025
Coffee Warms the Soul Svg/png/dxf/eps/pdf Coffee Svg Coffee10 fevereiro 2025 -
 STEM ENTRANCE EXAM REVIEWER PART II, JHS MATH TOPICS10 fevereiro 2025
STEM ENTRANCE EXAM REVIEWER PART II, JHS MATH TOPICS10 fevereiro 2025 -
 Pdfcoffee - Livro - Bioprocess Engineering Shuler Kargi Solution Manual As recognized, adventure as - Studocu10 fevereiro 2025
Pdfcoffee - Livro - Bioprocess Engineering Shuler Kargi Solution Manual As recognized, adventure as - Studocu10 fevereiro 2025 -
 Printable Mug Cozy Template Cup Cozy Printable PDF Coffee - Sweden10 fevereiro 2025
Printable Mug Cozy Template Cup Cozy Printable PDF Coffee - Sweden10 fevereiro 2025 -
 Why is it hiding this? ? BX wil Sutona memes That is the link to download the10 fevereiro 2025
Why is it hiding this? ? BX wil Sutona memes That is the link to download the10 fevereiro 2025 -
 nurse svg printable files – Creativedesignmaker10 fevereiro 2025
nurse svg printable files – Creativedesignmaker10 fevereiro 2025
você pode gostar
-
 Move the Block APK for Android Download10 fevereiro 2025
Move the Block APK for Android Download10 fevereiro 2025 -
𝐒𝐲𝐦𝐩𝐭𝐨𝐦𝐬 𝐨𝐟 𝐔𝐫𝐢𝐧𝐚𝐫𝐲 𝐬𝐭𝐨𝐧𝐞, infection10 fevereiro 2025
-
/filters:quality(70)/n49shopv2_zanline/images/produtos/jogo-de-matemtica-roleta-da-multiplicao-educativo-pedaggico-mdf-zanline-1307010929-1.jpg) Jogo de Matemática Roleta da Multiplicação Educativo Pedagógico MDF Zanline10 fevereiro 2025
Jogo de Matemática Roleta da Multiplicação Educativo Pedagógico MDF Zanline10 fevereiro 2025 -
 Silhouette of cat icon Stock Vector by ©PPVector 12940460410 fevereiro 2025
Silhouette of cat icon Stock Vector by ©PPVector 12940460410 fevereiro 2025 -
 Tradução Trouble - Twice10 fevereiro 2025
Tradução Trouble - Twice10 fevereiro 2025 -
 LOKIS NA TORRE DOS RS Roblox - Torre r Brasil10 fevereiro 2025
LOKIS NA TORRE DOS RS Roblox - Torre r Brasil10 fevereiro 2025 -
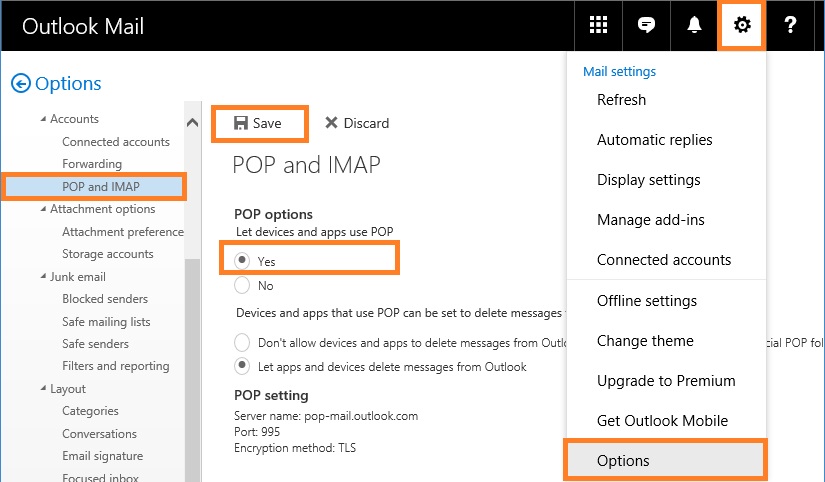 Windows Mail Restore Tool for Windows 10, 8.1 and 7 - Configure Windows Mail with Hotmail (Live, Outlook.com)10 fevereiro 2025
Windows Mail Restore Tool for Windows 10, 8.1 and 7 - Configure Windows Mail with Hotmail (Live, Outlook.com)10 fevereiro 2025 -
 Nutrient Survival10 fevereiro 2025
Nutrient Survival10 fevereiro 2025 -
 Star Wars Galaxies - Wikipedia10 fevereiro 2025
Star Wars Galaxies - Wikipedia10 fevereiro 2025 -
 4013 T - Mandíbula com Todos os Dentes - Harte Instrumentos Cirúrgicos10 fevereiro 2025
4013 T - Mandíbula com Todos os Dentes - Harte Instrumentos Cirúrgicos10 fevereiro 2025
