Ransomware: Build Your Own Ransomware, Part 1
Por um escritor misterioso
Last updated 23 abril 2025

Welcome back, my aspiring cyberwarriors! Ransomware is rapidly becoming the most important form of malware afflicting our digital systems. Companies across the globe are being hit with various forms of malware including the new variant, Snake, designed specifically for SCADA/ICS systems. The Colonial Pipeline in the US was shutdown for nearly a week before paying a $5 million ransom, demonstrating the danger of this ransomware to industrial systems and a nation
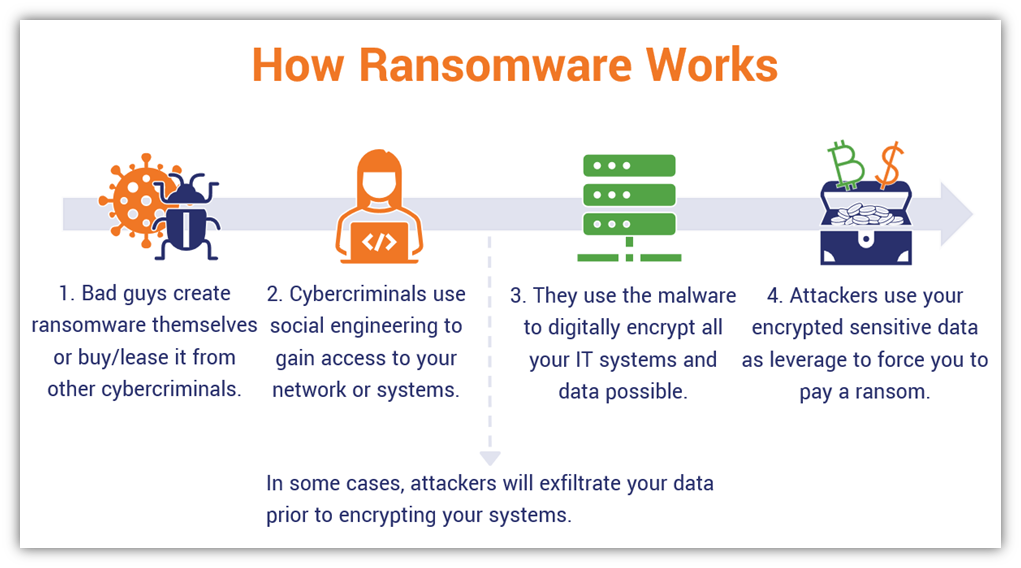
What Is Ransomware & How Does Ransomware Work? - Hashed Out by The SSL Store™

Resilient Zero Trust Defense: Ivanti's Ransomware Solution 1

Blueprint for Ransomware Defense
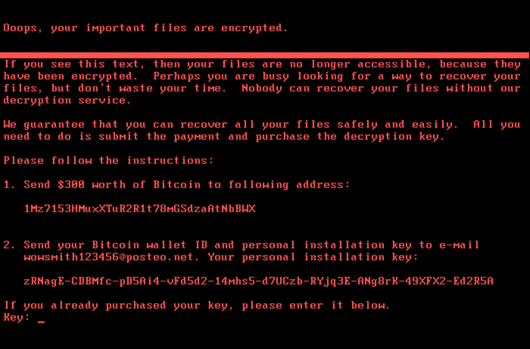
NotPetya Ransomware Attack [Technical Analysis]
OccupytheWeb on X: Ransomware: Build Your Own Ransomware, Part 1 # ransomware #colonialpipeline #snake #CyberWarrior / X
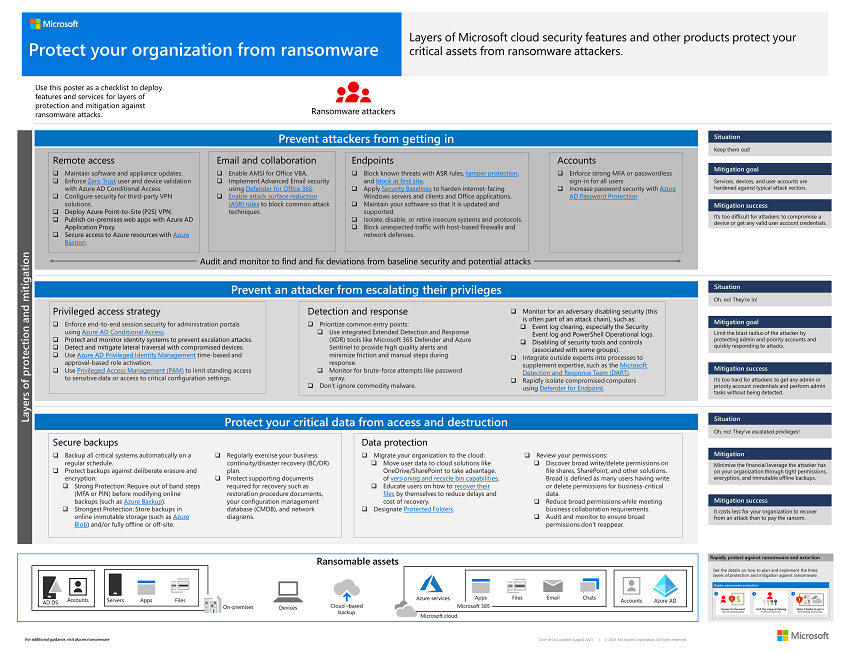
Human-operated ransomware

A guide to combatting human-operated ransomware: Part 1

Make Your Own Ransomware, (Part 1)
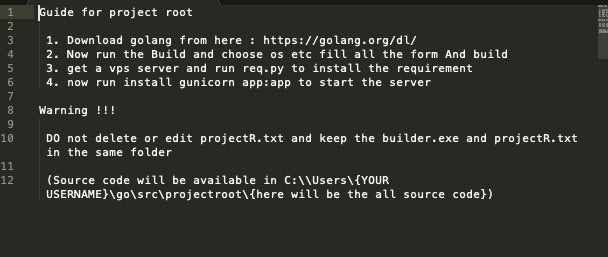
Build Your Own Ransomware (Project Root) Behind Enemy Lines Part 2 - SentinelOne
Build Your Own Ransomware (Project Root) Behind Enemy Lines Part 2 - SentinelOne

7 Steps to Help Prevent & Limit the Impact of Ransomware
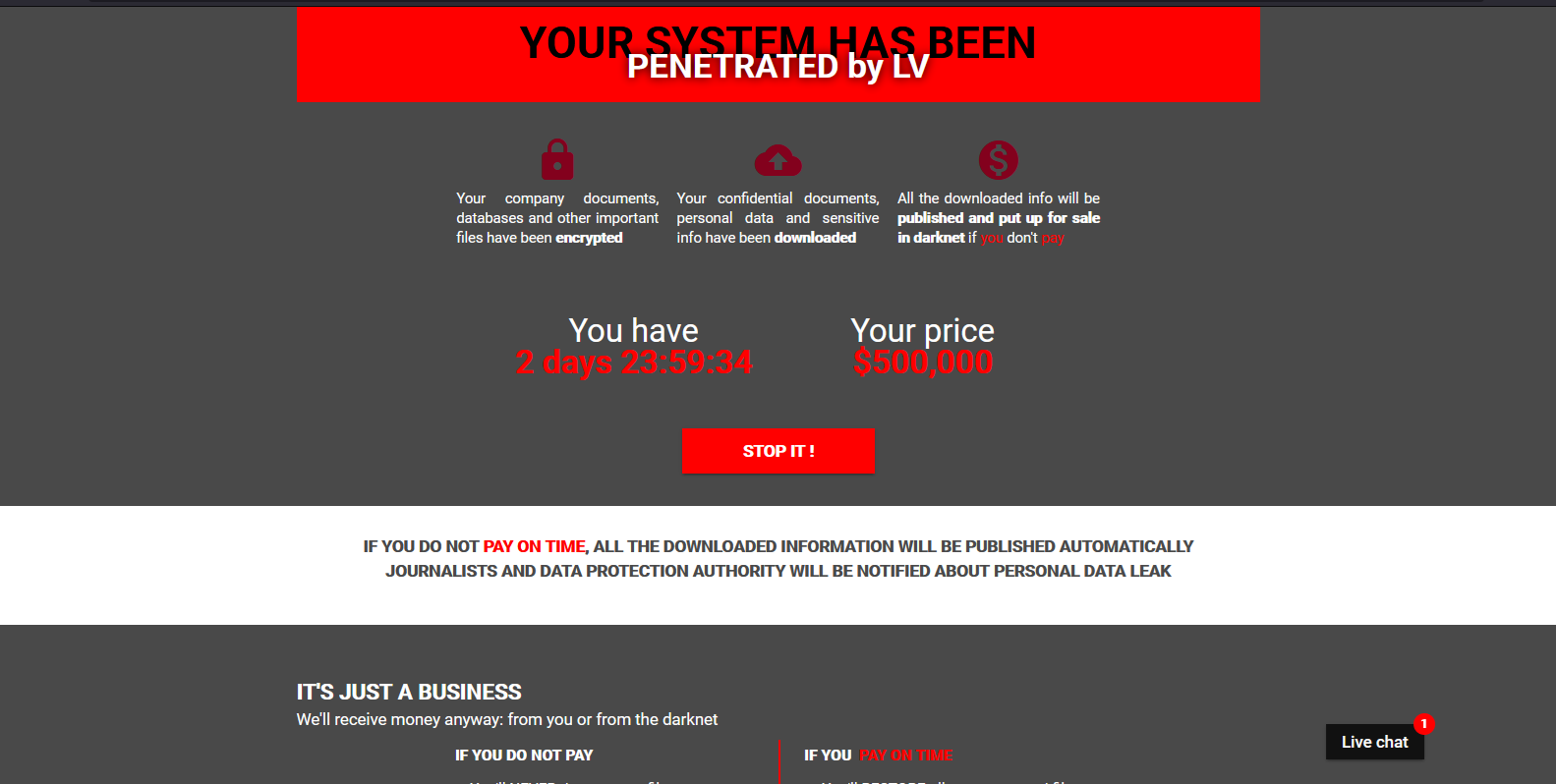
LV Ransomware Exploits ProxyShell in Attack on a Jordan-based Company
Recomendado para você
-
 Get Google Snake Game Menu Mod - (July, 2022) - FREE23 abril 2025
Get Google Snake Game Menu Mod - (July, 2022) - FREE23 abril 2025 -
GitHub - DarkSnakeGang/GoogleSnakeDeleteStuffMod23 abril 2025
-
 Build a snake game23 abril 2025
Build a snake game23 abril 2025 -
game-solver · GitHub Topics · GitHub23 abril 2025
-
GitHub - sumy7/gitsnackhub: A browser extension for Chrome that you can play snack game on Github contribution chart.23 abril 2025
-
 Games on GitHub · GitHub23 abril 2025
Games on GitHub · GitHub23 abril 2025 -
Shubham Shreshth - Backend Developer Intern - Zeta23 abril 2025
-
Why don't employers seem to care about my GitHub stars or contributions? Doesn't 4 years of working on my own count? - Quora23 abril 2025
-
GitHub - Hack-way/A-Snake-Game: The Snake Game is a classic arcade game where the player controls a snake that moves around the game board, eating food and growing longer. The goal is to23 abril 2025
-
 GitHub - DarkSnakeGang/GoogleSnakeLevelEditor: Level Editor Mod23 abril 2025
GitHub - DarkSnakeGang/GoogleSnakeLevelEditor: Level Editor Mod23 abril 2025
você pode gostar
-
 Karnataka 2nd PUC Result 2022 Declared LIVE: 61.88% Pass, Simran Rao Gets Rank 1, Science Best-Performing Stream - News1823 abril 2025
Karnataka 2nd PUC Result 2022 Declared LIVE: 61.88% Pass, Simran Rao Gets Rank 1, Science Best-Performing Stream - News1823 abril 2025 -
 Mieruko-chan, DECA-DENCE, Majo no Tabitabi e outros 5 animes ganham dublagem pela Crunchyroll - IntoxiAnime23 abril 2025
Mieruko-chan, DECA-DENCE, Majo no Tabitabi e outros 5 animes ganham dublagem pela Crunchyroll - IntoxiAnime23 abril 2025 -
 Epic Games launches Fortnite on the Google Play Store and they're23 abril 2025
Epic Games launches Fortnite on the Google Play Store and they're23 abril 2025 -
 Mini Moto Cross Trilha 49cc BZ Fire Amarela Partida a Corda23 abril 2025
Mini Moto Cross Trilha 49cc BZ Fire Amarela Partida a Corda23 abril 2025 -
 How To Play Roblox WITHOUT Downloading It (New July 2023)23 abril 2025
How To Play Roblox WITHOUT Downloading It (New July 2023)23 abril 2025 -
 Apple Watch Series 8 GPS+Cellular 45mm Aço Inoxidável Prateado com Bracelete desportiva Branca23 abril 2025
Apple Watch Series 8 GPS+Cellular 45mm Aço Inoxidável Prateado com Bracelete desportiva Branca23 abril 2025 -
 animes fire.net23 abril 2025
animes fire.net23 abril 2025 -
 adesivo sacolinha corrida carros personalizado23 abril 2025
adesivo sacolinha corrida carros personalizado23 abril 2025 -
 Bahia x Fluminense: onde assistir, horário do jogo, prováveis escalações e mais23 abril 2025
Bahia x Fluminense: onde assistir, horário do jogo, prováveis escalações e mais23 abril 2025 -
 São Paulo x Corinthians: onde assistir, escalações e horário do jogo pelo Brasileirão23 abril 2025
São Paulo x Corinthians: onde assistir, escalações e horário do jogo pelo Brasileirão23 abril 2025