SILKLOADER: How Hackers Evade Detection
Por um escritor misterioso
Last updated 19 março 2025

As the cyber threat landscape continues to evolve, hackers are employing increasingly sophisticated techniques to evade detection. One such example is the SILKLOADER malware, which has recently gained attention for its stealth capabilities.

Exaramel Malware Links Industroyer ICS malware and NotPetya wiper

Chinese hackers use new custom backdoor to evade detection

hacking news, Breaking Cybersecurity News

Companies on alert after apparent hack of cloud-based security camera service

Risky Biz News: Google wants to reduce lifespan of TLS certificates from one year to just 90 days
Risky Biz News: Google wants to reduce lifespan of TLS certificates from one year to just 90 days

OSINTer - Article List

Telerik exploitation. Cloud storage re-up attacks. Phishing tackle. Cyber developments in Russia's hybrid war.

How Hackers Are “Blending In” to Evade Detection

Endpoint Protection - Symantec Enterprise

Chinese State-Sponsored Hackers Evade Common Cybersecurity Tools
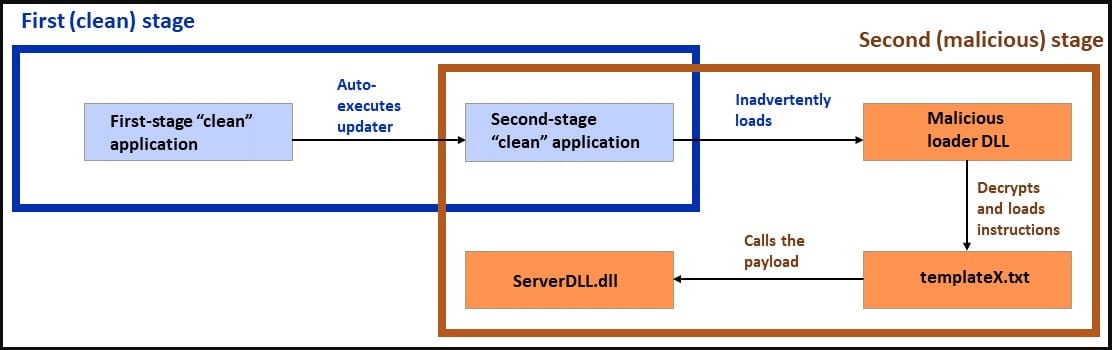
Hackers start using double DLL sideloading to evade detection

Evading AV with Veil-Evasion
Recomendado para você
-
 ⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD19 março 2025
⚡️EVADE Script Pastebin 2022 AUTO FARM ⚡️ AUTO XP CASH ESP GOD19 março 2025 -
 Evade Script/GUI Review19 março 2025
Evade Script/GUI Review19 março 2025 -
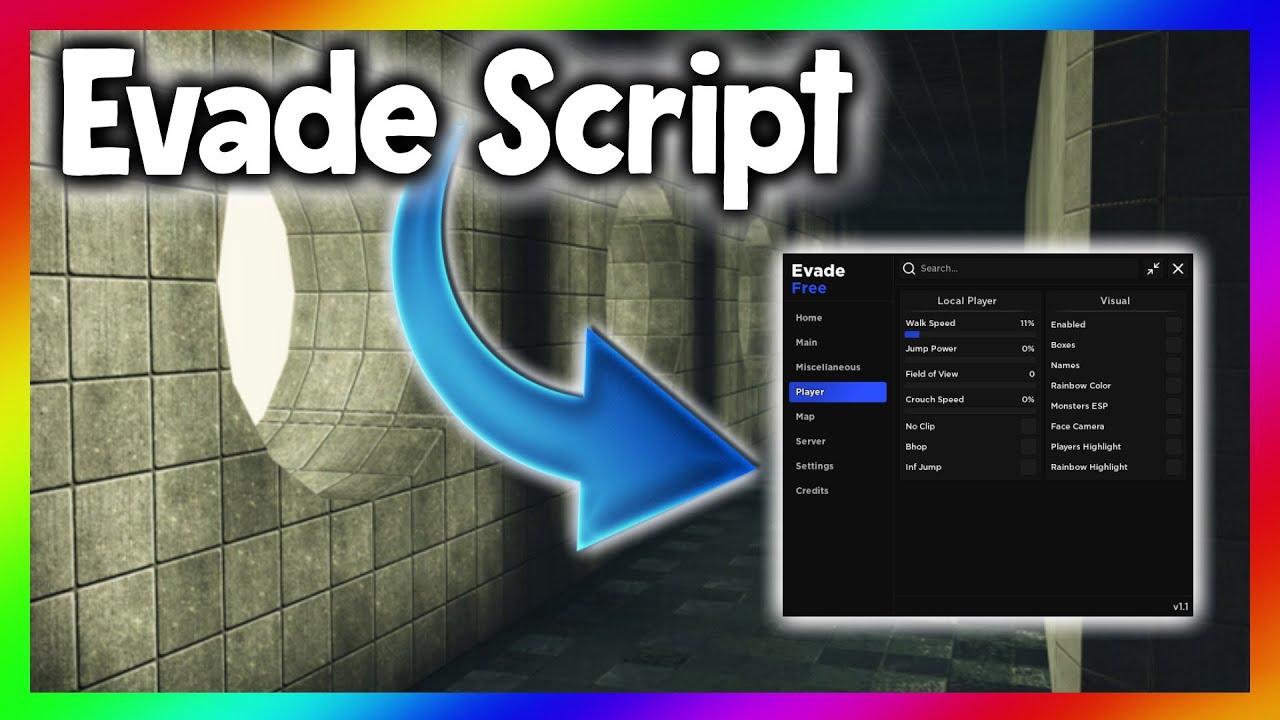 New Script: 💠 Roblox Evade Script : r/Zaptosis19 março 2025
New Script: 💠 Roblox Evade Script : r/Zaptosis19 março 2025 -
![Evade [Auto Farm - Fast Revive & More!] Scripts](https://rbxscript.com/images/-nOtc6We36d-image.jpg) Evade [Auto Farm - Fast Revive & More!] Scripts19 março 2025
Evade [Auto Farm - Fast Revive & More!] Scripts19 março 2025 -
![🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)](https://i.ytimg.com/vi/m_qS5tSnnts/maxresdefault.jpg) 🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)19 março 2025
🔥NOVO] Evade Script ROBLOX!! (Funcionando 2022)19 março 2025 -
 Script for EVADE Made by 9Strew - WRD Community19 março 2025
Script for EVADE Made by 9Strew - WRD Community19 março 2025 -
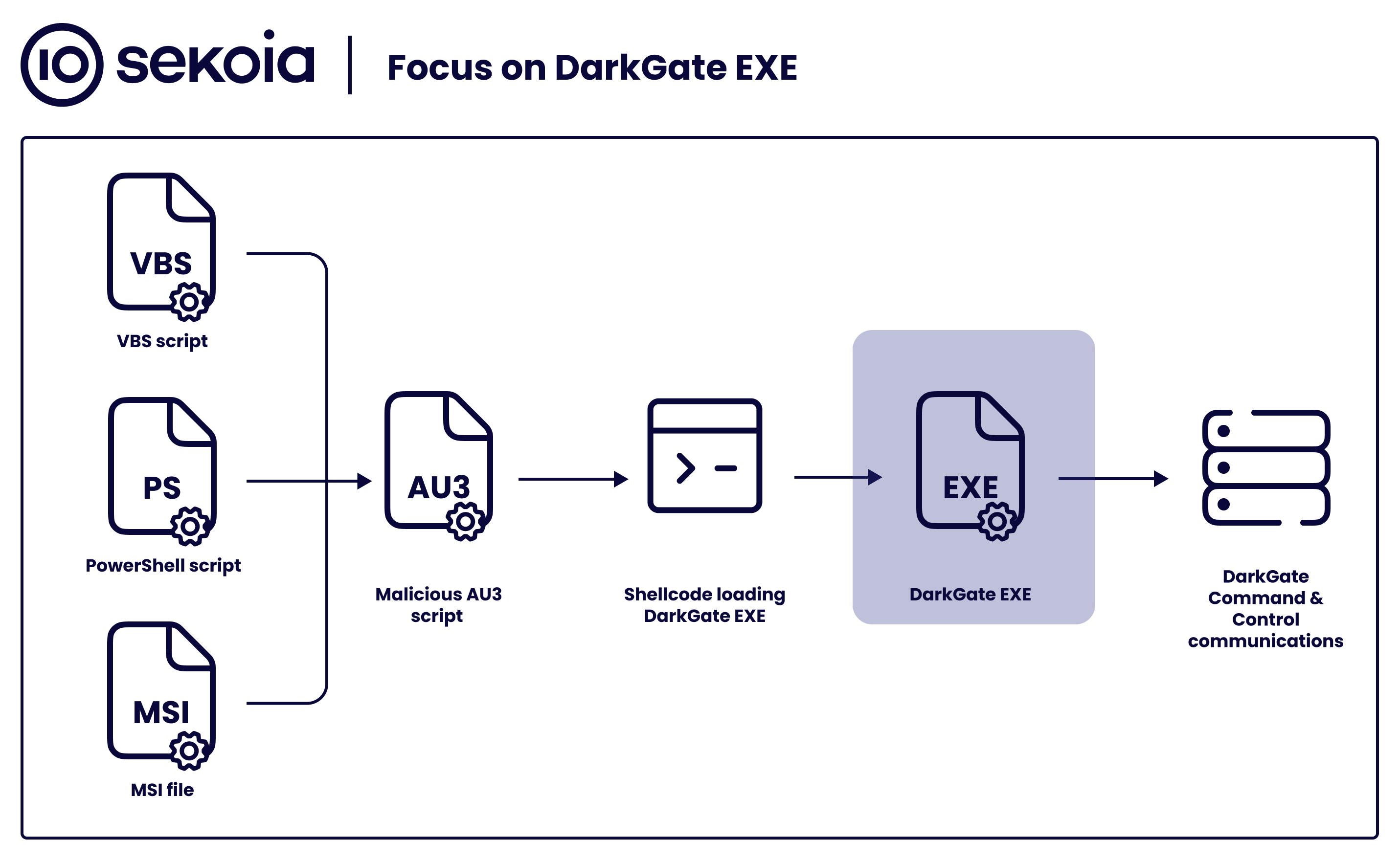
Sekoia.io on X: #DarkGate gained popularity among threat actors19 março 2025
-
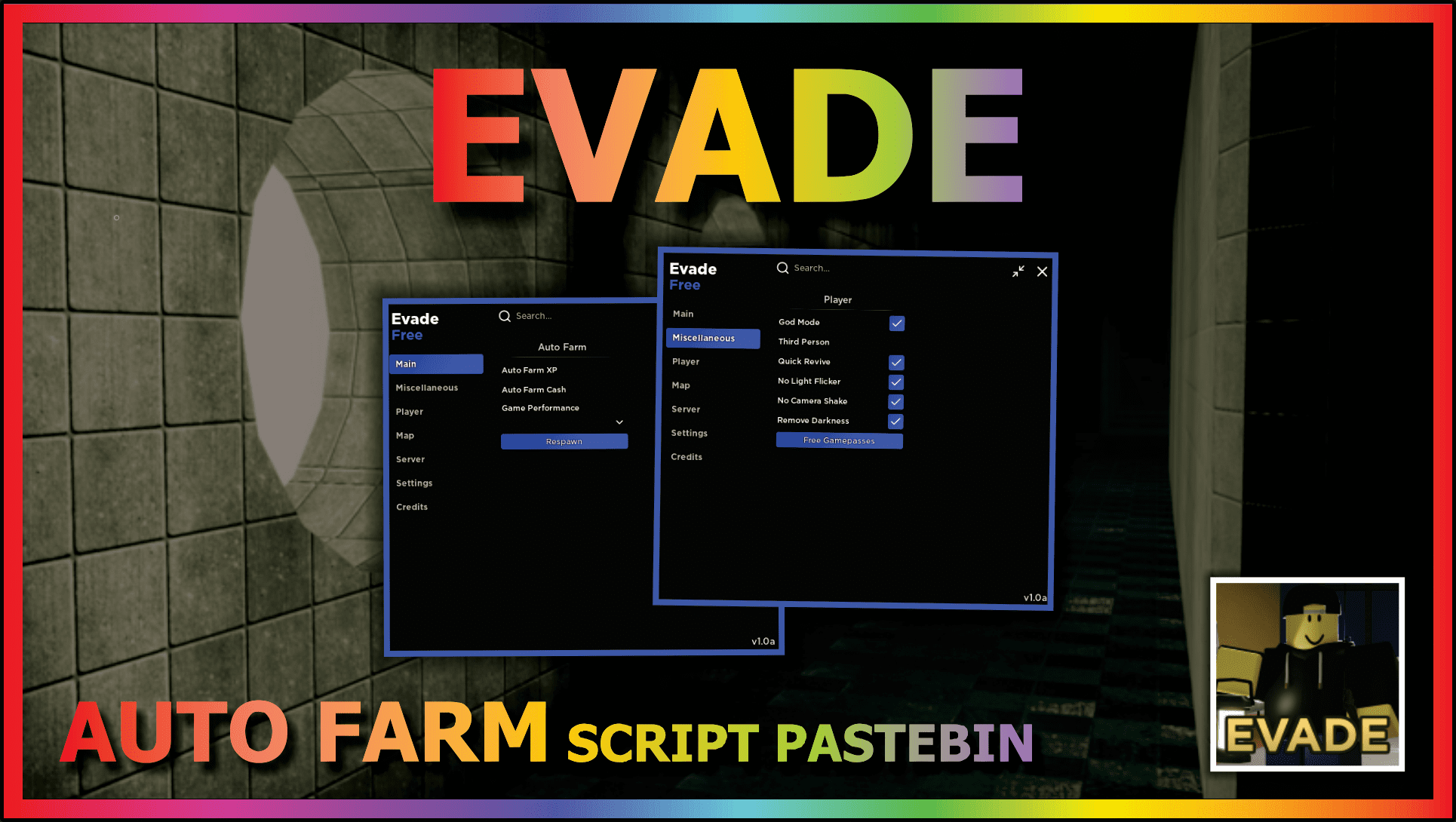 EVADE (AUTO REVIVE) – DailyPastebin19 março 2025
EVADE (AUTO REVIVE) – DailyPastebin19 março 2025 -
 Obsidian Giant, Evolution Evade Wiki19 março 2025
Obsidian Giant, Evolution Evade Wiki19 março 2025 -
 evade fly script|TikTok Search19 março 2025
evade fly script|TikTok Search19 março 2025
você pode gostar
-
 Crítica Jogos Mortais - Plano Crítico19 março 2025
Crítica Jogos Mortais - Plano Crítico19 março 2025 -
 EA SPORTS FC on X: Updates to the Companion App for #FIFA23 continue to roll out to more and more markets 📱🙌 Check your iOS or Android App Stores or download here19 março 2025
EA SPORTS FC on X: Updates to the Companion App for #FIFA23 continue to roll out to more and more markets 📱🙌 Check your iOS or Android App Stores or download here19 março 2025 -
 Teemu Eskola - Teemu Eskola19 março 2025
Teemu Eskola - Teemu Eskola19 março 2025 -
 Pet Simulator 99 News on X: 📰PET SIMULATOR X LEAKS📰 Here is what the Trading Plaza will look like! (From Preston in Discord) / X19 março 2025
Pet Simulator 99 News on X: 📰PET SIMULATOR X LEAKS📰 Here is what the Trading Plaza will look like! (From Preston in Discord) / X19 março 2025 -
 Assistir Anime Mahoutsukai no Yome: Nishi no Shounen to Seiran no19 março 2025
Assistir Anime Mahoutsukai no Yome: Nishi no Shounen to Seiran no19 março 2025 -
 Deep Rock Galactic - Wikipedia19 março 2025
Deep Rock Galactic - Wikipedia19 março 2025 -
 GTA SAN ANDREAS PPSSPP PARA CELULAR ANDROID E PSP CONSOLE ! ✓ SA19 março 2025
GTA SAN ANDREAS PPSSPP PARA CELULAR ANDROID E PSP CONSOLE ! ✓ SA19 março 2025 -
 Fix feature unavailable facebook login is currently unavailable19 março 2025
Fix feature unavailable facebook login is currently unavailable19 março 2025 -
 Casa Bauducco abre nova loja no Shopping Eldorado19 março 2025
Casa Bauducco abre nova loja no Shopping Eldorado19 março 2025 -
 Rajendra Singh e Martin Winiecki na Represa de Guarapiranga - IAS19 março 2025
Rajendra Singh e Martin Winiecki na Represa de Guarapiranga - IAS19 março 2025