SSH Passwd, PDF, Cyberwarfare
Por um escritor misterioso
Last updated 12 março 2025


PDF] A Study of Passwords and Methods Used in Brute-Force SSH Attacks

SSH Passwd, PDF, Cyberwarfare

macOS Incident Response Part 3: System Manipulation - SentinelLabs

PDF) Educational Scenario for Teaching Cyber Security Using low-cost Equipment and Open Source Software

KmsdBot, a new evasive bot for cryptomining and DDoS attacks

PDF) Teaching pentesting to social sciences students using experiential learning techniques to improve attitudes towards possible cybersecurity careers

COVID-19 Cybersecurity Alerts, Coronavirus Phishing Scam, Covid 19 Malware, Cyware

Xiologix Security overview - Tualatin, Oregon, United States of America
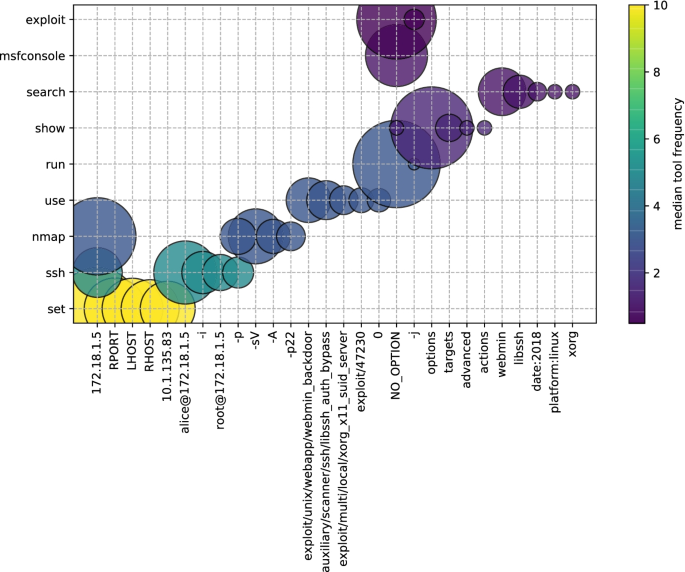
Student assessment in cybersecurity training automated by pattern mining and clustering

network security, Breaking Cybersecurity News

Access Management - bank information security
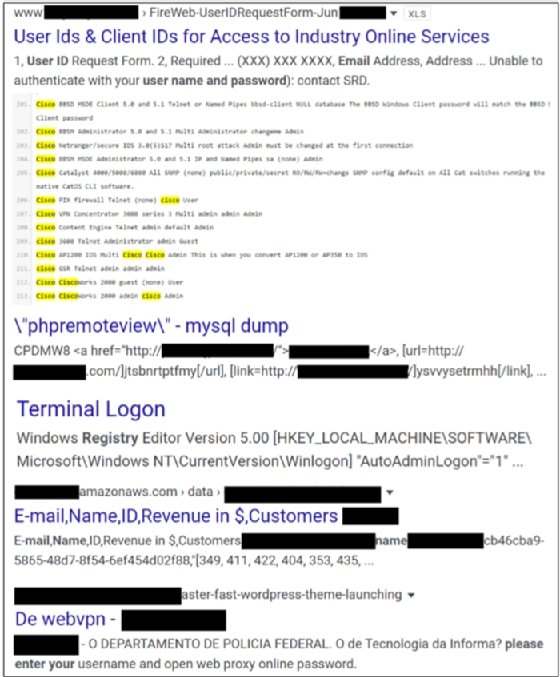
How cyber warfare laws limit risk on a digital battleground
Recomendado para você
-
 The chess games of Luis Paulo Supi12 março 2025
The chess games of Luis Paulo Supi12 março 2025 -
 Enxadrista mirassolense é vice-campeã em Catanduva, Notícias12 março 2025
Enxadrista mirassolense é vice-campeã em Catanduva, Notícias12 março 2025 -
 O CASAL SE ENFRENTA NO TABULEIRO! Julia Alboredo vs Luis Paulo Supi.12 março 2025
O CASAL SE ENFRENTA NO TABULEIRO! Julia Alboredo vs Luis Paulo Supi.12 março 2025 -
Luis Paulo Supi Melhores Jogadores de Xadrez12 março 2025
-
Unitel - Parabéns ! Estes são os seguintes Vencedores do12 março 2025
-
 🔥 Mikhail Tal Ficaria com INVEJA! 🤣 Partidinhas de Blitz 🏁♟️12 março 2025
🔥 Mikhail Tal Ficaria com INVEJA! 🤣 Partidinhas de Blitz 🏁♟️12 março 2025 -
brute-dict/pass.100000 at master · santatic/brute-dict · GitHub12 março 2025
-
 PDF) Memórias Virtuais: Representações Digitais da Guerra Colonial12 março 2025
PDF) Memórias Virtuais: Representações Digitais da Guerra Colonial12 março 2025 -
 Calaméo - Regional 83912 março 2025
Calaméo - Regional 83912 março 2025 -
 Clelia Luro - Wikipedia12 março 2025
Clelia Luro - Wikipedia12 março 2025
você pode gostar
-
 Rift Herald (Malphite) - Custom Skin Spotlight12 março 2025
Rift Herald (Malphite) - Custom Skin Spotlight12 março 2025 -
 Arisu sakayanagi HD wallpapers12 março 2025
Arisu sakayanagi HD wallpapers12 março 2025 -
 How to Train Your Dragon 2 Race Paint Tutorial12 março 2025
How to Train Your Dragon 2 Race Paint Tutorial12 março 2025 -
 Thomas Twins Harukana Receive12 março 2025
Thomas Twins Harukana Receive12 março 2025 -
 Toca Life World APK Mod (Tudo Desbloqueado) 1.78 Download 202312 março 2025
Toca Life World APK Mod (Tudo Desbloqueado) 1.78 Download 202312 março 2025 -
 Shadow Warrior 2 (XBO) Review –12 março 2025
Shadow Warrior 2 (XBO) Review –12 março 2025 -
 Tomo-chan wa Onnanoko! - Dublado – Episódio 6 Online - Hinata Soul12 março 2025
Tomo-chan wa Onnanoko! - Dublado – Episódio 6 Online - Hinata Soul12 março 2025 -
 Review: Notebook 2 A.M. E55012 março 2025
Review: Notebook 2 A.M. E55012 março 2025 -
 Disney Pixar Toy Story Forky Sounds Figure Bonnie Fork +Cowgirl Jessie Doll Lot12 março 2025
Disney Pixar Toy Story Forky Sounds Figure Bonnie Fork +Cowgirl Jessie Doll Lot12 março 2025 -
 Modern Chess Openings, Vol. 1: Open Games - Chess Opening Software on CD12 março 2025
Modern Chess Openings, Vol. 1: Open Games - Chess Opening Software on CD12 março 2025
