Shellshock Vulnerability Exploitation and Mitigation: A Demonstration
Por um escritor misterioso
Last updated 23 abril 2025
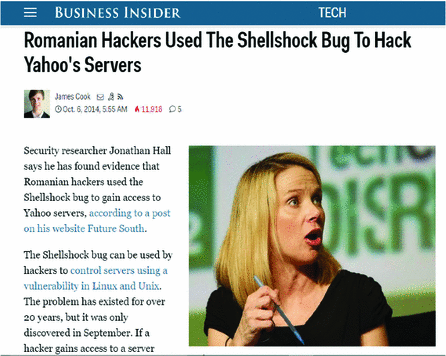

Inside Shellshock: How hackers are using it to exploit systems
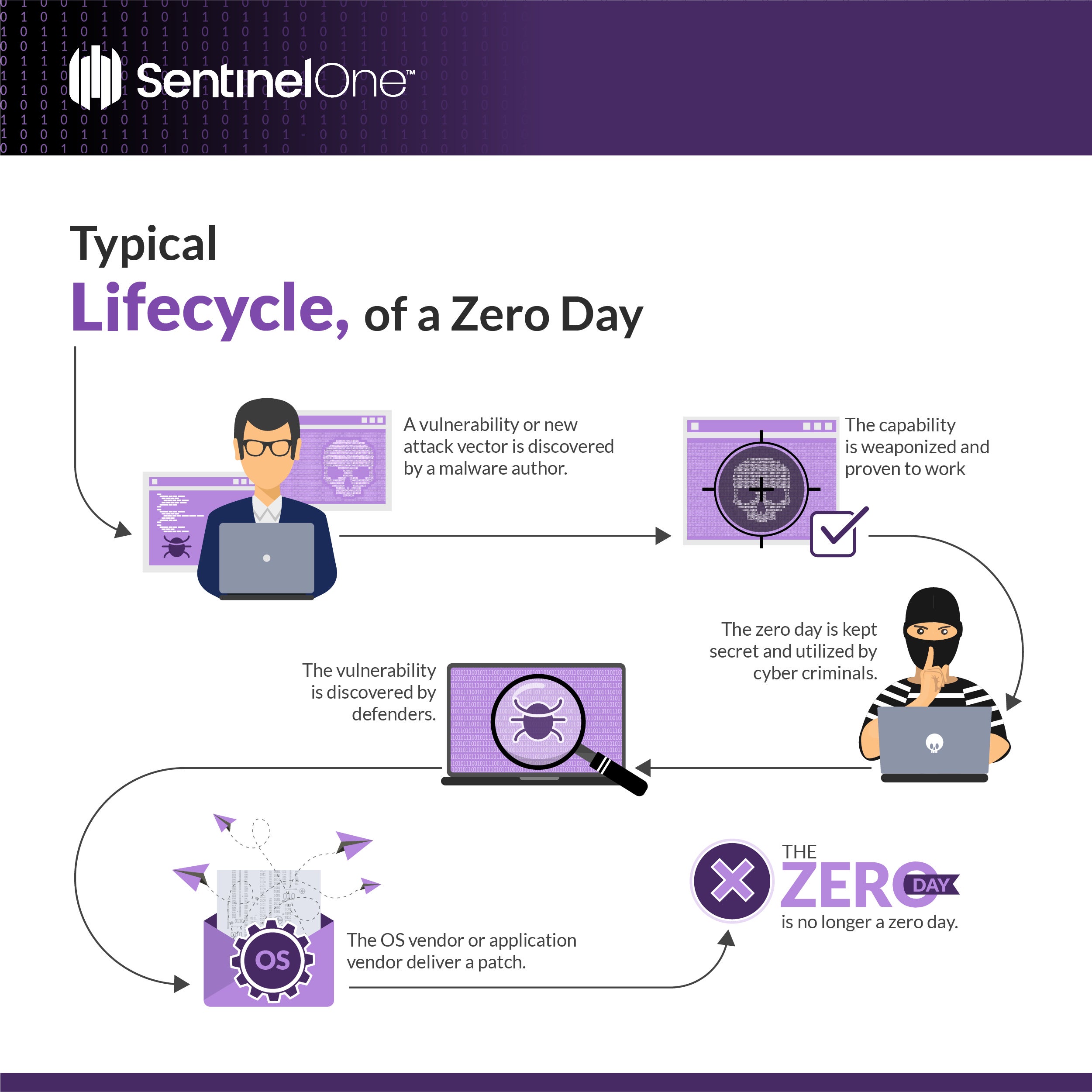
What is a Security Vulnerability? - SentinelOne

Malicious virtual machine configured as a router on a network whose
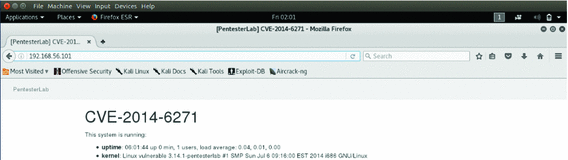
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

Exploiting and verifying shellshock: CVE-2014-6271
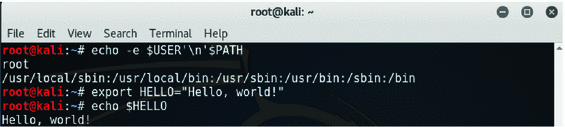
Shellshock Vulnerability Exploitation and Mitigation: A Demonstration

About the Shellshock Vulnerability: The Basics of the “Bash Bug” - Security News

Shellshock - A Software Bug
Mlytics helps protect against Log4Shell vulnerability
Recomendado para você
-
 Shellshock: Nam '67 - Wikipedia23 abril 2025
Shellshock: Nam '67 - Wikipedia23 abril 2025 -
 Shell Shocked! The Visual Studio Hack You Should Know23 abril 2025
Shell Shocked! The Visual Studio Hack You Should Know23 abril 2025 -
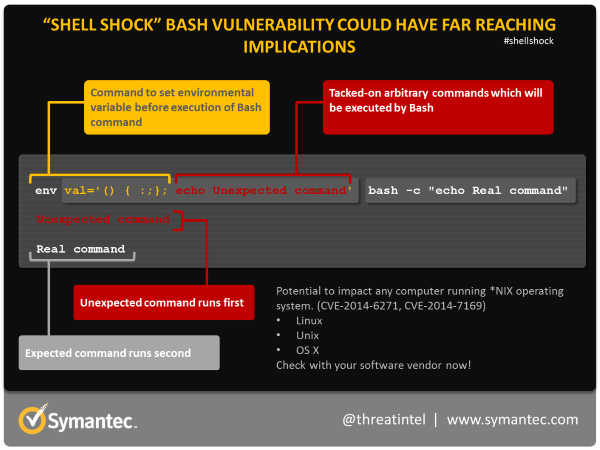 Threat Intelligence on X: Shellshock: All you need to know about the Bash Bug vulnerability #Shellshock #BashBug / X23 abril 2025
Threat Intelligence on X: Shellshock: All you need to know about the Bash Bug vulnerability #Shellshock #BashBug / X23 abril 2025 -
 Yahoo confirms servers infected — but not by Shellshock23 abril 2025
Yahoo confirms servers infected — but not by Shellshock23 abril 2025 -
 Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks23 abril 2025
Hackers Using 'Shellshock' Bash Vulnerability to Launch Botnet Attacks23 abril 2025 -
Shellshock: Bash software bug leaves up to 500 million computers at risk of hacking - ABC News23 abril 2025
-
 BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek23 abril 2025
BASHLITE Malware Uses ShellShock to Hijack Devices Running BusyBox - SecurityWeek23 abril 2025 -
 Hackers 'already using Shellshock bug to attack victims23 abril 2025
Hackers 'already using Shellshock bug to attack victims23 abril 2025 -
![Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats](https://i.imgur.com/EZKbChh.png) Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats23 abril 2025
Outdated] Con's Shell Shock Live Aimbot [Source Code] - MPGH - MultiPlayer Game Hacking & Cheats23 abril 2025 -
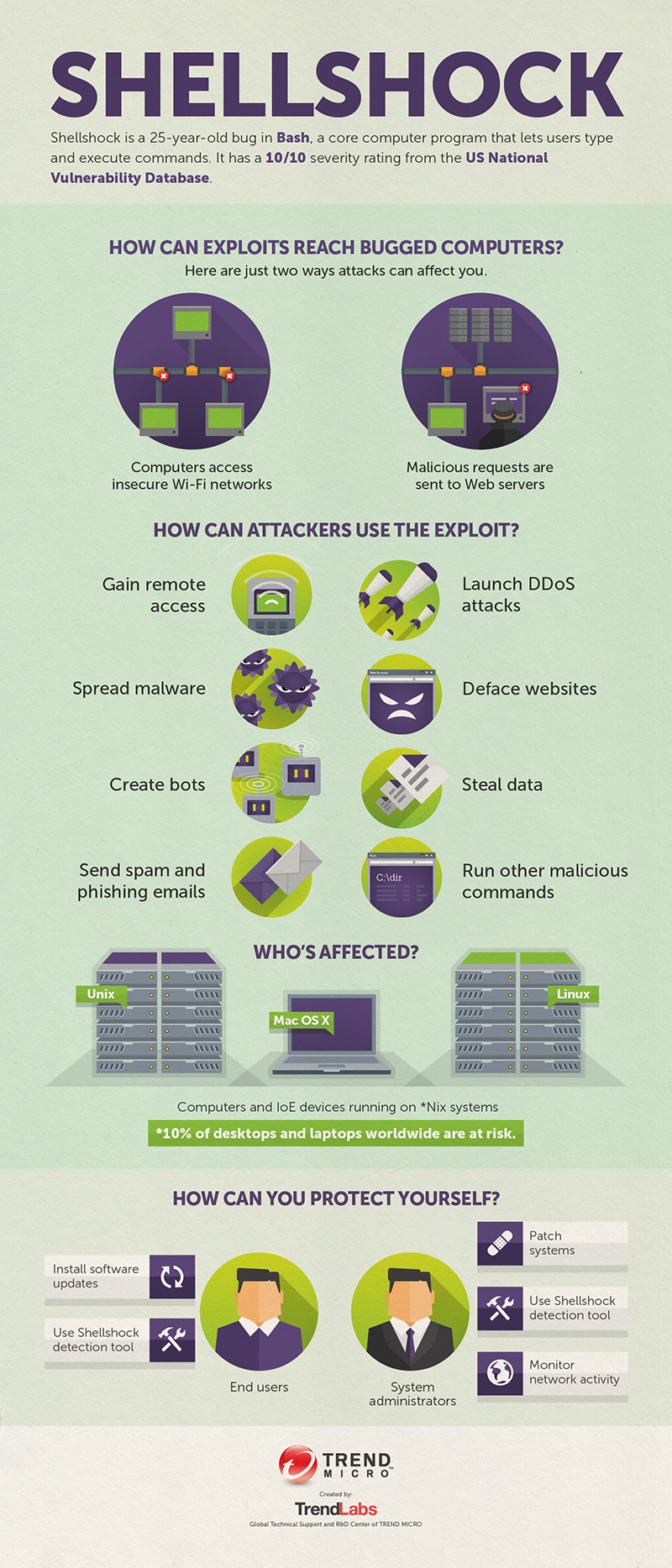 About the Shellshock Vulnerability: The Basics of the “Bash Bug23 abril 2025
About the Shellshock Vulnerability: The Basics of the “Bash Bug23 abril 2025
você pode gostar
-
 Sachi Komine (Grisaia no Kajitsu) - Pictures23 abril 2025
Sachi Komine (Grisaia no Kajitsu) - Pictures23 abril 2025 -
 Dingo Australia Royalty-Free Images, Stock Photos & Pictures23 abril 2025
Dingo Australia Royalty-Free Images, Stock Photos & Pictures23 abril 2025 -
 Simu Liu at the photocall for Barbie, at the London Eye. Picture date: Wednesday July 12, 2023 Stock Photo - Alamy23 abril 2025
Simu Liu at the photocall for Barbie, at the London Eye. Picture date: Wednesday July 12, 2023 Stock Photo - Alamy23 abril 2025 -
 124 WPM monkeytype.com23 abril 2025
124 WPM monkeytype.com23 abril 2025 -
 Madimbu, Wiki23 abril 2025
Madimbu, Wiki23 abril 2025 -
 Haganezuka Hotaru Anime demon, Dragon slayer, Slayer anime23 abril 2025
Haganezuka Hotaru Anime demon, Dragon slayer, Slayer anime23 abril 2025 -
 Cristiano Ronaldo throws reporter's microphone into lake on Make a GIF23 abril 2025
Cristiano Ronaldo throws reporter's microphone into lake on Make a GIF23 abril 2025 -
 Isekai Shoukan wa Nidome desu ep 01 (PART 1)23 abril 2025
Isekai Shoukan wa Nidome desu ep 01 (PART 1)23 abril 2025 -
 Battlefield 5 - PS4 vs PS5 - Graphics Comparison & FPS Test23 abril 2025
Battlefield 5 - PS4 vs PS5 - Graphics Comparison & FPS Test23 abril 2025 -
 Inscrições abertas para o Brasileiro de Luta Livre Esportiva 202023 abril 2025
Inscrições abertas para o Brasileiro de Luta Livre Esportiva 202023 abril 2025