11 Types of Spoofing Attacks Every Security Professional Should
Por um escritor misterioso
Last updated 12 março 2025

The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. The goal is to feign trust, gain a foothold in a system, get hold of data, pilfer money, or distribute predatory software. What can black hats try to . . .
The term “spoofing” might have a comic implication in some contexts, but it’s no joke when it comes to information security. In fact, this is a subject matter of a whole separate chapter in a seasoned cybercriminal’s handbook. It comprises a multitude of techniques aimed at camouflaging a malicious actor or device as somebody or something else. Out of all the nefarious scenarios that fit the mold of a spoofing attack, the following 11 types are growingly impactful for the enterprise these days.
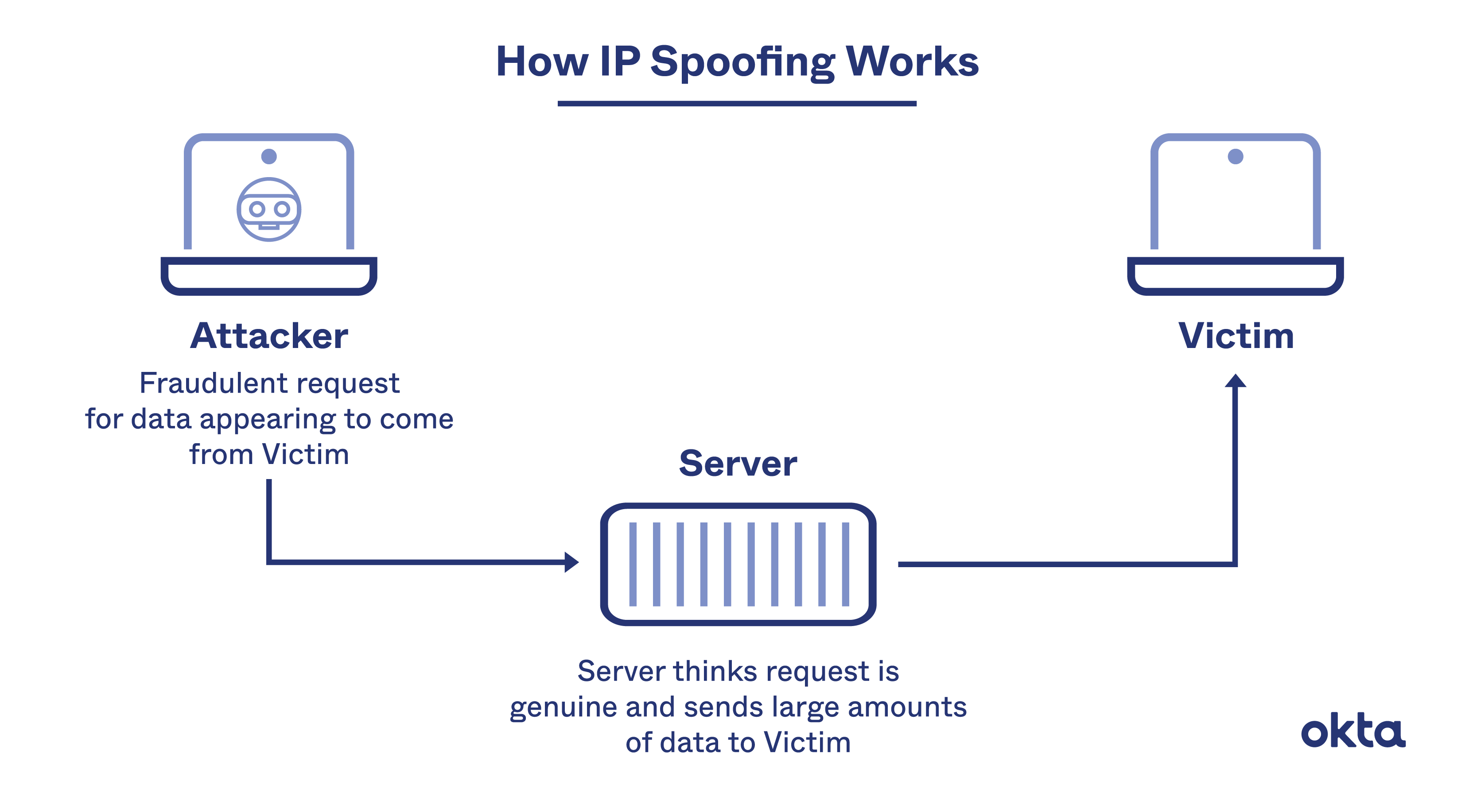
IP Spoofing Unraveled: What It Is & How to Prevent It
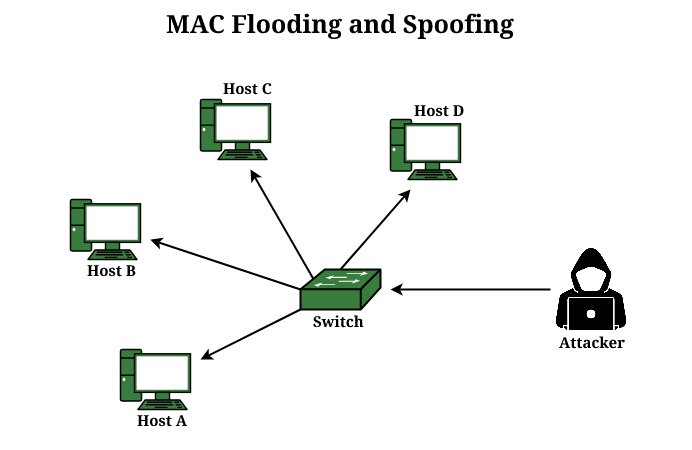
What is MAC Spoofing Attack? - GeeksforGeeks

From cookie theft to BEC: Attackers use AiTM phishing sites as

What is ARP Spoofing Attack? - GeeksforGeeks
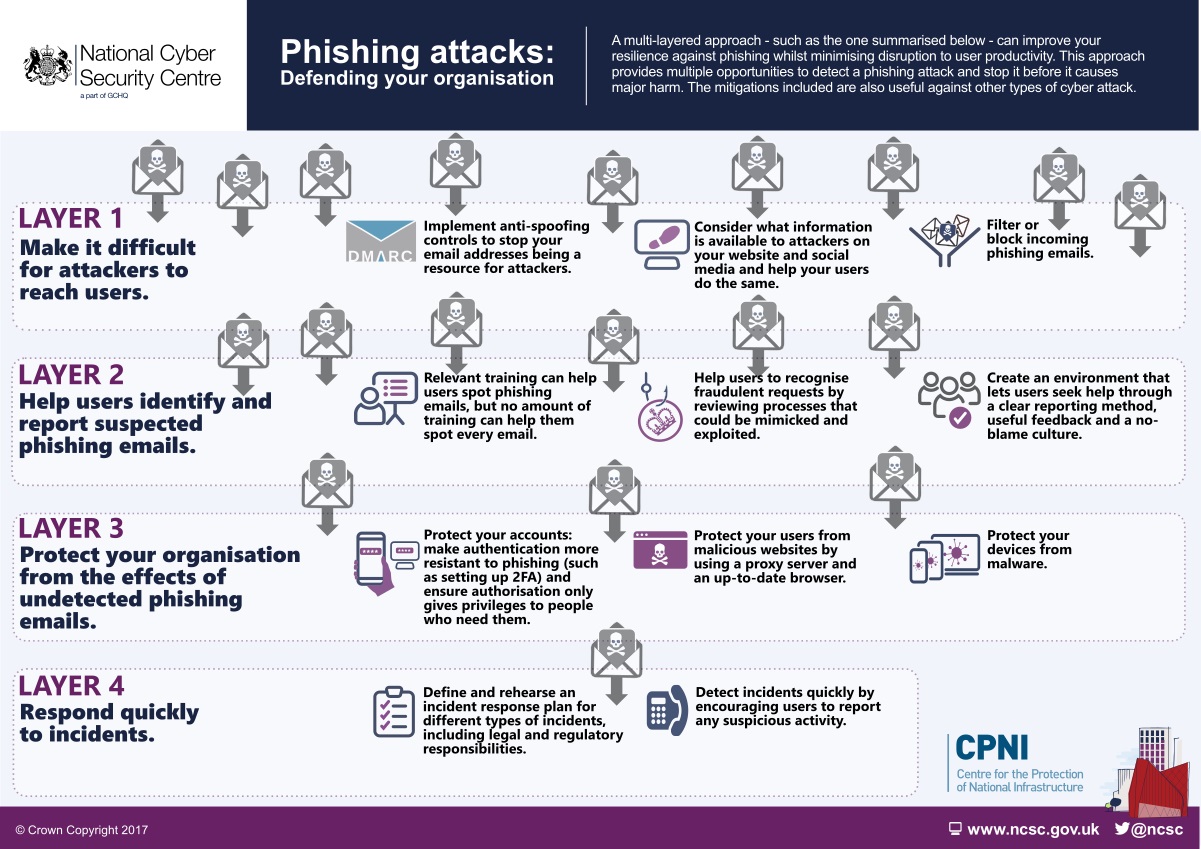
How to Defend your Organisation from Phishing Attacks - News - NCS IT

How do Phishing and Spoofing Attacks Impact Businesses?
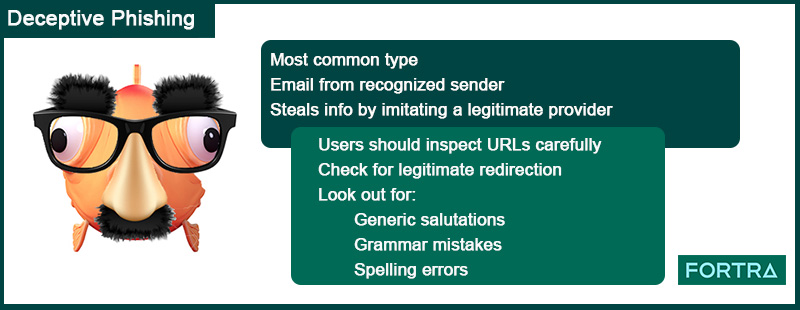
6 Common Phishing Attacks and How to Protect Against Them

What is IP Spoofing? Definition, Types & Protection

6 Common Phishing Attacks and How to Protect Against Them

Must Know Phishing Statistics In 2023 - Attacks And Breaches
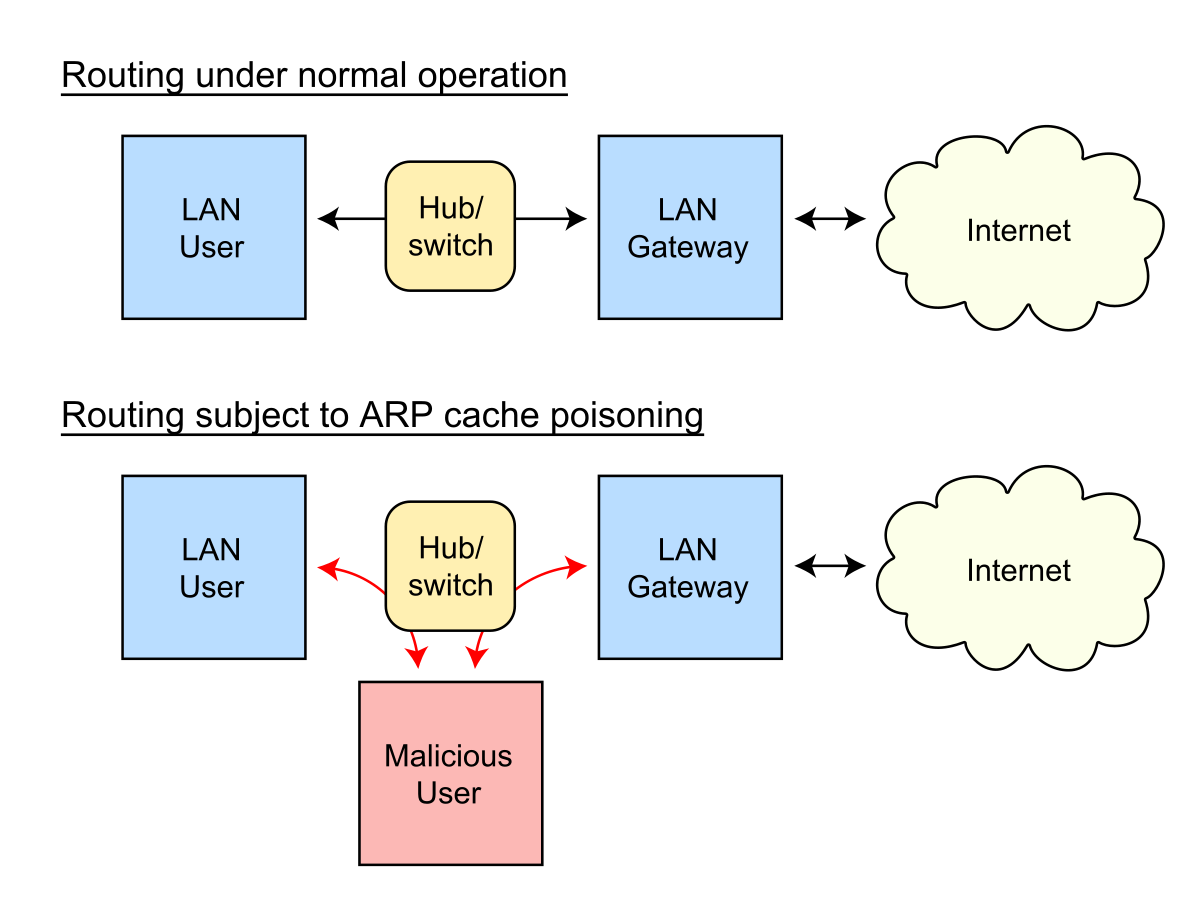
ARP spoofing - Wikipedia

19 Examples of Common Phishing Emails

Cyber Security Terms Everyone Should Know- ThriveDX

What Is Spoofing? - Cisco
Recomendado para você
-
GitHub - SonsoFsERpent/redEngine-Spoofer: With the redENGINE12 março 2025
-
 YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub12 março 2025
YoLink LoRa Smart Outdoor Contact Sensor & SpeakerHub12 março 2025 -
 What is Spoofing? - FFCCU Blog12 março 2025
What is Spoofing? - FFCCU Blog12 março 2025 -
 A comprehensive survey on radio frequency (RF) fingerprinting12 março 2025
A comprehensive survey on radio frequency (RF) fingerprinting12 março 2025 -
 Nobody's Fool: Spoofing Detection in a High-Precision Receiver12 março 2025
Nobody's Fool: Spoofing Detection in a High-Precision Receiver12 março 2025 -
 GootBot - Gootloader's new approach to post-exploitation12 março 2025
GootBot - Gootloader's new approach to post-exploitation12 março 2025 -
 Simply Click to Change Your Location in Pokémon GO12 março 2025
Simply Click to Change Your Location in Pokémon GO12 março 2025 -
HookSpoofer: The Modified Open Source Stealer Bundlers Making the12 março 2025
-
 Testing a Receiver's Galileo OS-NMA Capability Using Skydel12 março 2025
Testing a Receiver's Galileo OS-NMA Capability Using Skydel12 março 2025 -
 Telnet Networks - Managing Network Performance - Telnet Network News - The Inside Scoop on GPS Spoofing12 março 2025
Telnet Networks - Managing Network Performance - Telnet Network News - The Inside Scoop on GPS Spoofing12 março 2025
você pode gostar
-
/i.s3.glbimg.com/v1/AUTH_08fbf48bc0524877943fe86e43087e7a/internal_photos/bs/2021/X/0/k4022hTS2XzV8dmQfJug/marca-d-agua-1-.png) Apps de controle remoto: conheça cinco opções para Android e iPhone12 março 2025
Apps de controle remoto: conheça cinco opções para Android e iPhone12 março 2025 -
 Camp Half-Blood Camp Shirt Essential T-Shirt for Sale by Rachael Raymer12 março 2025
Camp Half-Blood Camp Shirt Essential T-Shirt for Sale by Rachael Raymer12 março 2025 -
:no_upscale()/cdn.vox-cdn.com/uploads/chorus_asset/file/24852709/hoon_lee_1.jpg) Warrior season 4, release, cast plans, and what we know so far12 março 2025
Warrior season 4, release, cast plans, and what we know so far12 março 2025 -
Cenário do Jogo dos Pontinhos no Programa Silvio Santos, versão12 março 2025
-
Zugzwang12 março 2025
-
 The Wertzone: A Song of Facts and Figures: A Clash of Kings12 março 2025
The Wertzone: A Song of Facts and Figures: A Clash of Kings12 março 2025 -
 The Last Of Us Episode 6: Joel and Tommy Reunion Explained and12 março 2025
The Last Of Us Episode 6: Joel and Tommy Reunion Explained and12 março 2025 -
 Things We Wish We Knew Before Starting Vengeful Guardian: Moonrider12 março 2025
Things We Wish We Knew Before Starting Vengeful Guardian: Moonrider12 março 2025 -
Santa Maria Grill 48x3012 março 2025
-
I have snake aids :) on Tumblr12 março 2025



