Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's Red Team Tools
Por um escritor misterioso
Last updated 12 março 2025

We analyzed tactics, techniques, and procedures utilized by threat actors of the FireEye’s stolen Red Team Tools. Attackers heavily used various defense evasion techniques.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.
In 2013, Picus Security pioneered Breach and Attack Simulation (BAS) technology and has helped companies improve their cyber resilience since then. Established by cybersecurity veterans with academic backgrounds and extensive hands-on experience, Picus Security developed a transformative Security Validation solution for end-to-end attack readiness visibility and effortless mitigation to pre-empt cyber attacks across all cyber defense layers.

Try Hack Me Red Team Threat Intel
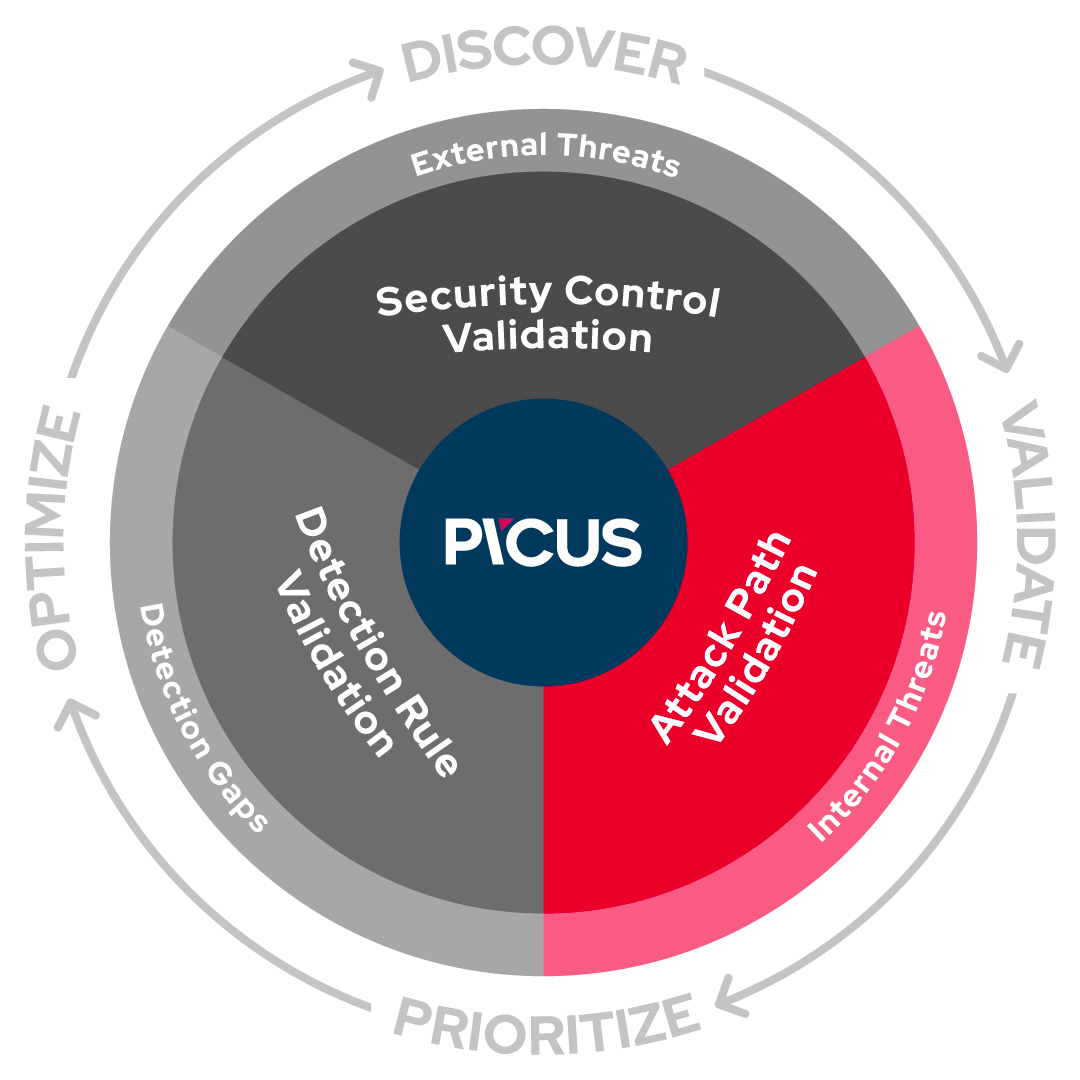
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's
Redteam-Hardware-Toolkit - Red Team Hardware Toolkit

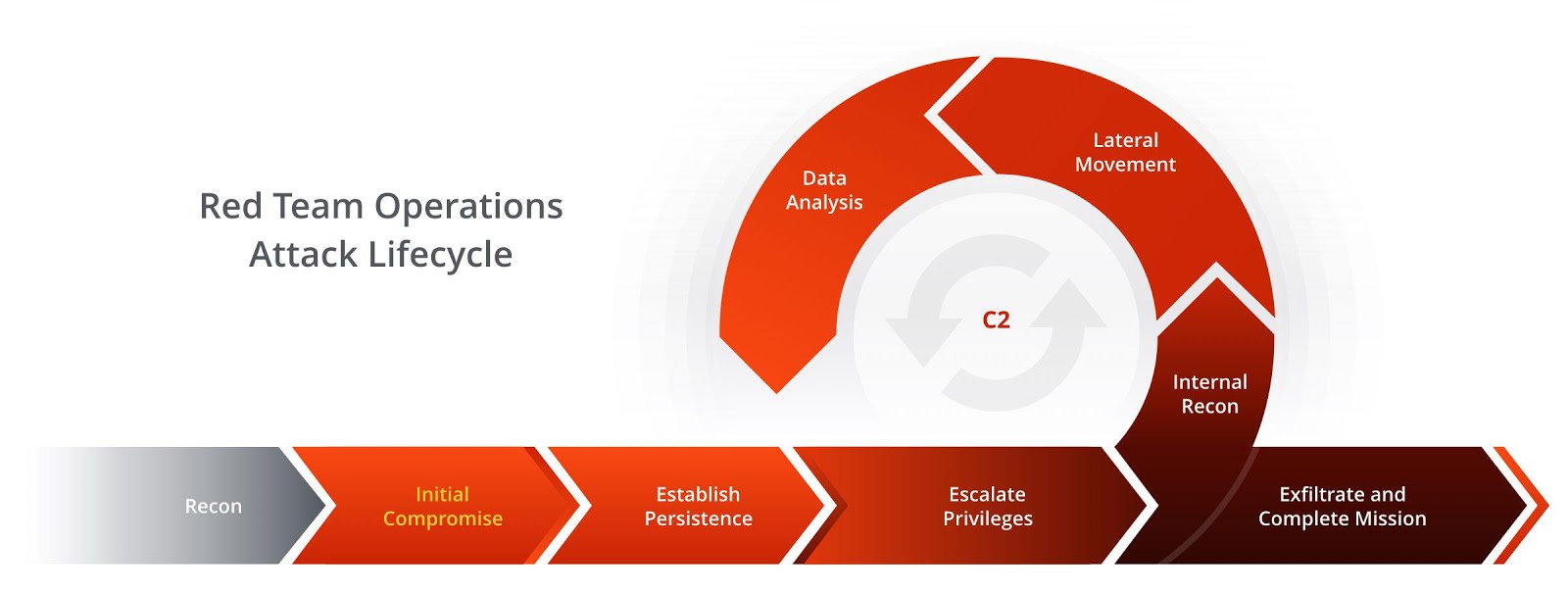
Understanding Tactics, Techniques, and Procedures (TTP)

It is Time to Take Action - How to Defend Against FireEye's Red

Tactics, Techniques and Procedures of FireEye Red Team Tools

Red Team vs Blue Team: An In-depth Analysis of Cybersecurity
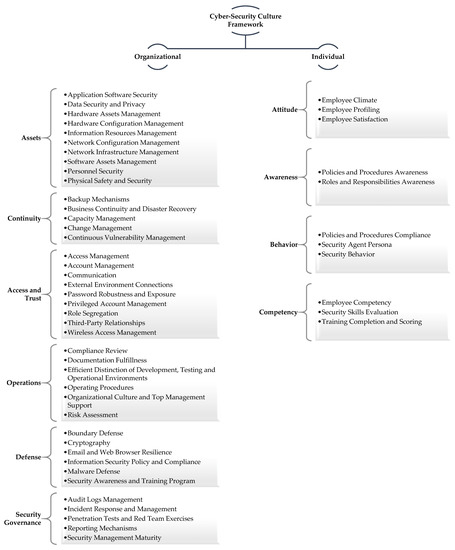
Sensors, Free Full-Text

Tactics, Techniques and Procedures of FireEye Red Team Tools
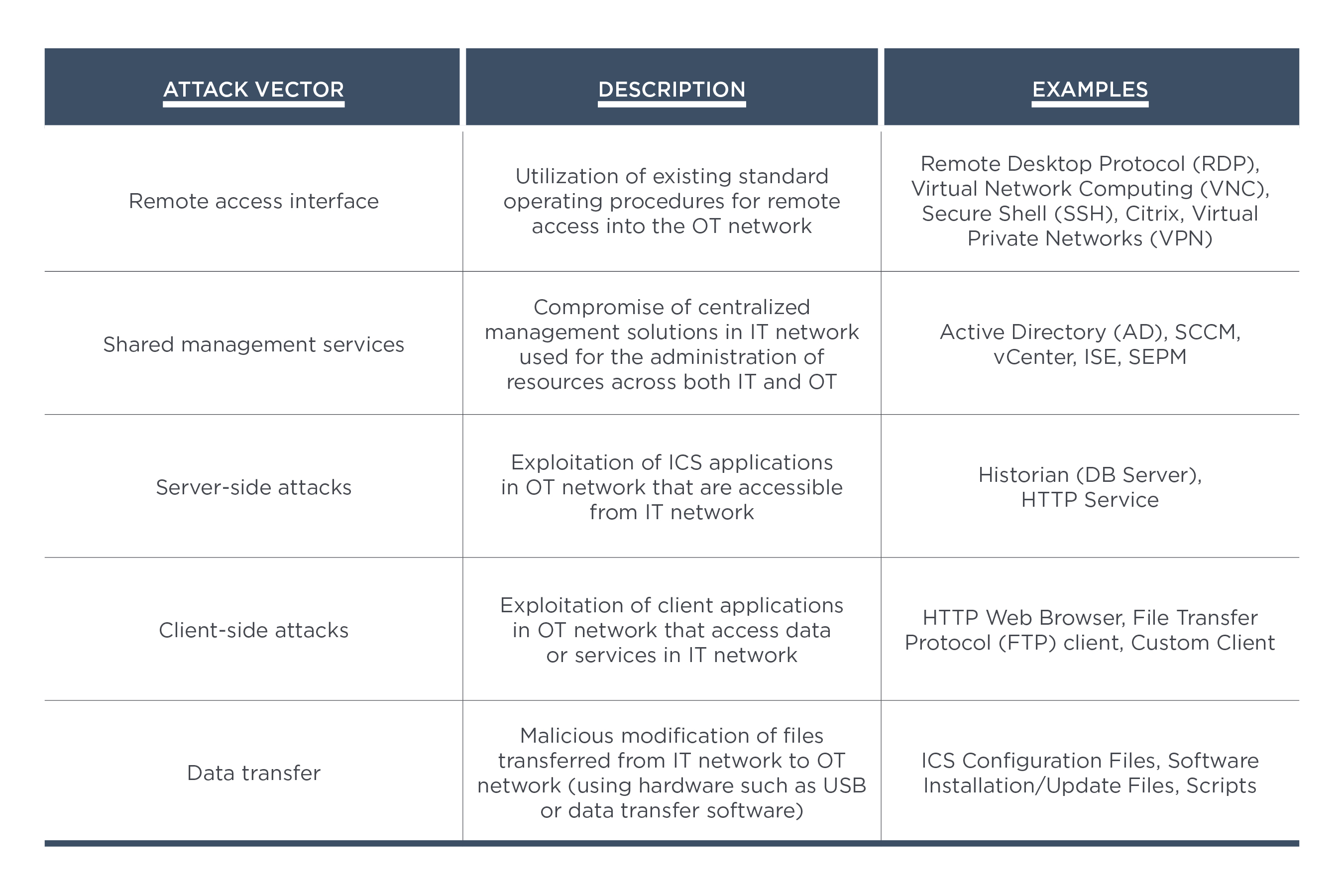
Hacking Operational Technology for Defense
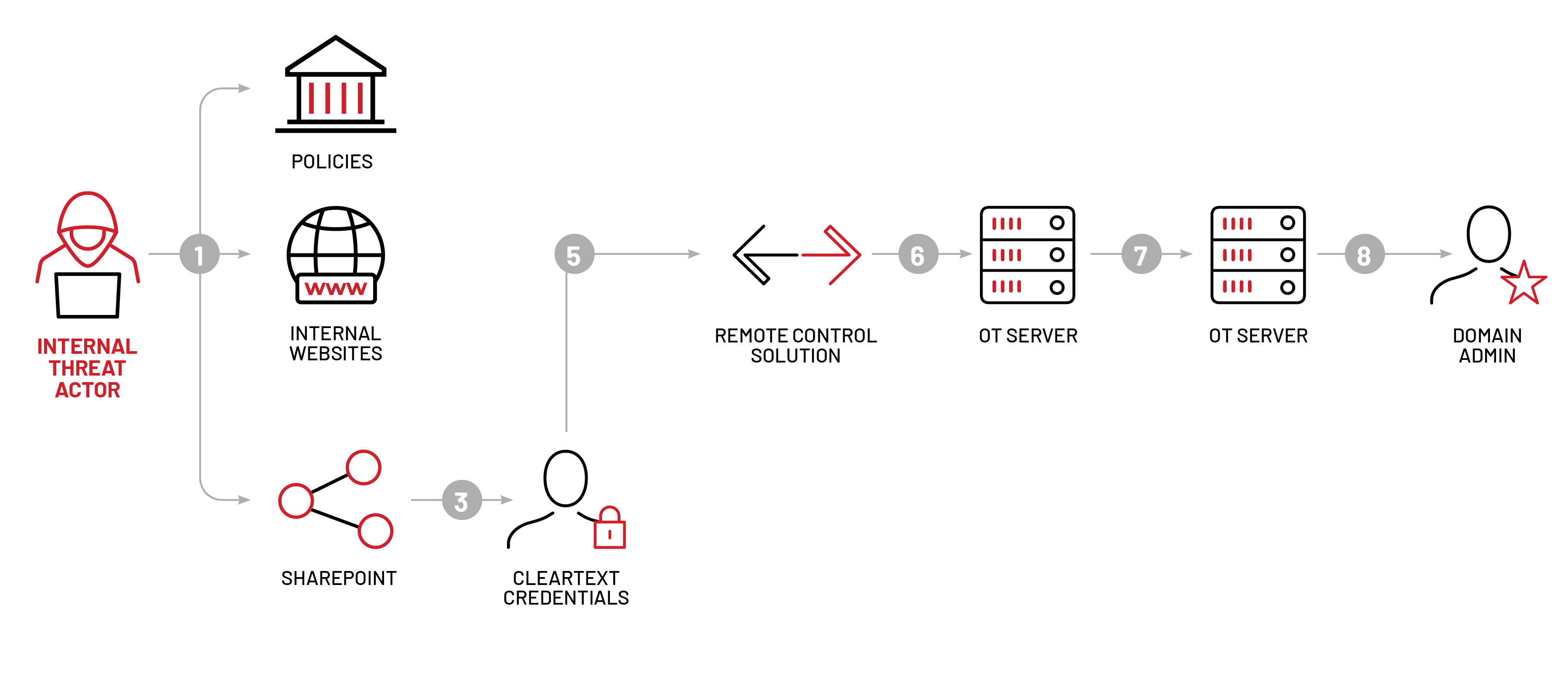
Mandiant Red Team Emulates FIN11 Tactics To Control Operational
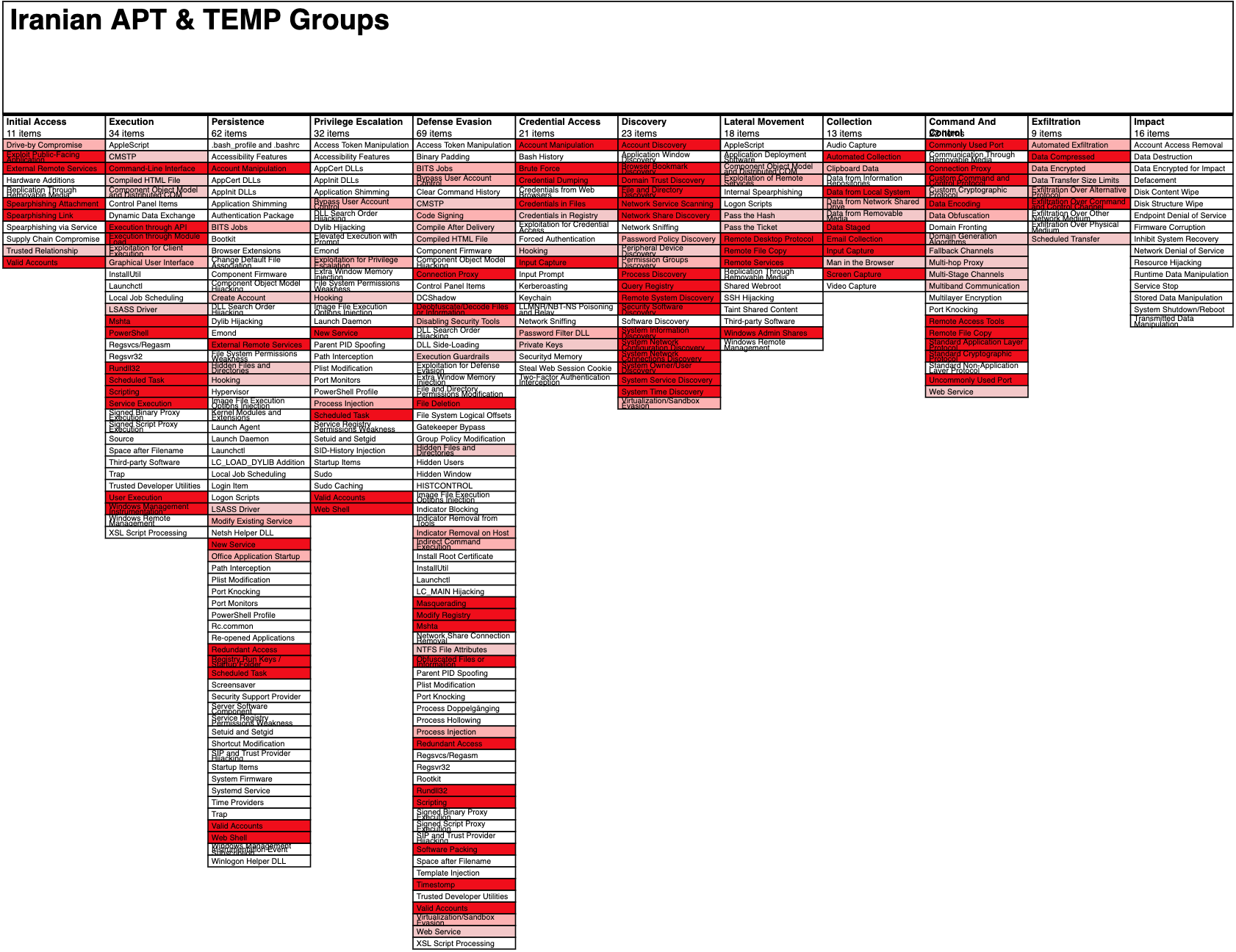
Operationalizing CTI: Using MITRE ATT&CK to Hunt for and Defend
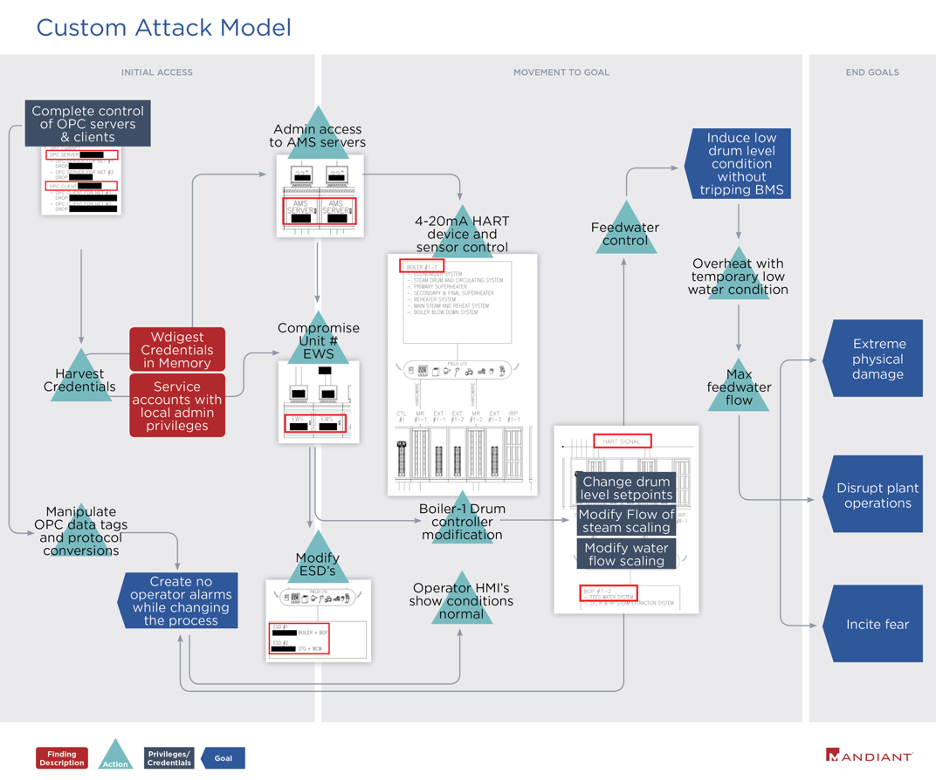
OT Red Teaming Mandiant's Approach for OT Red Teaming
Recomendado para você
-
 Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG12 março 2025
Redengine Lifetime - Melhor Modmenu Para Fivem - Gta - DFG12 março 2025 -
 HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!12 março 2025
HOW TO REDEEM YOUR REDENGINE KEY AND DOWNLOAD REDENGINE!12 março 2025 -
 Spoofers Revealed12 março 2025
Spoofers Revealed12 março 2025 -
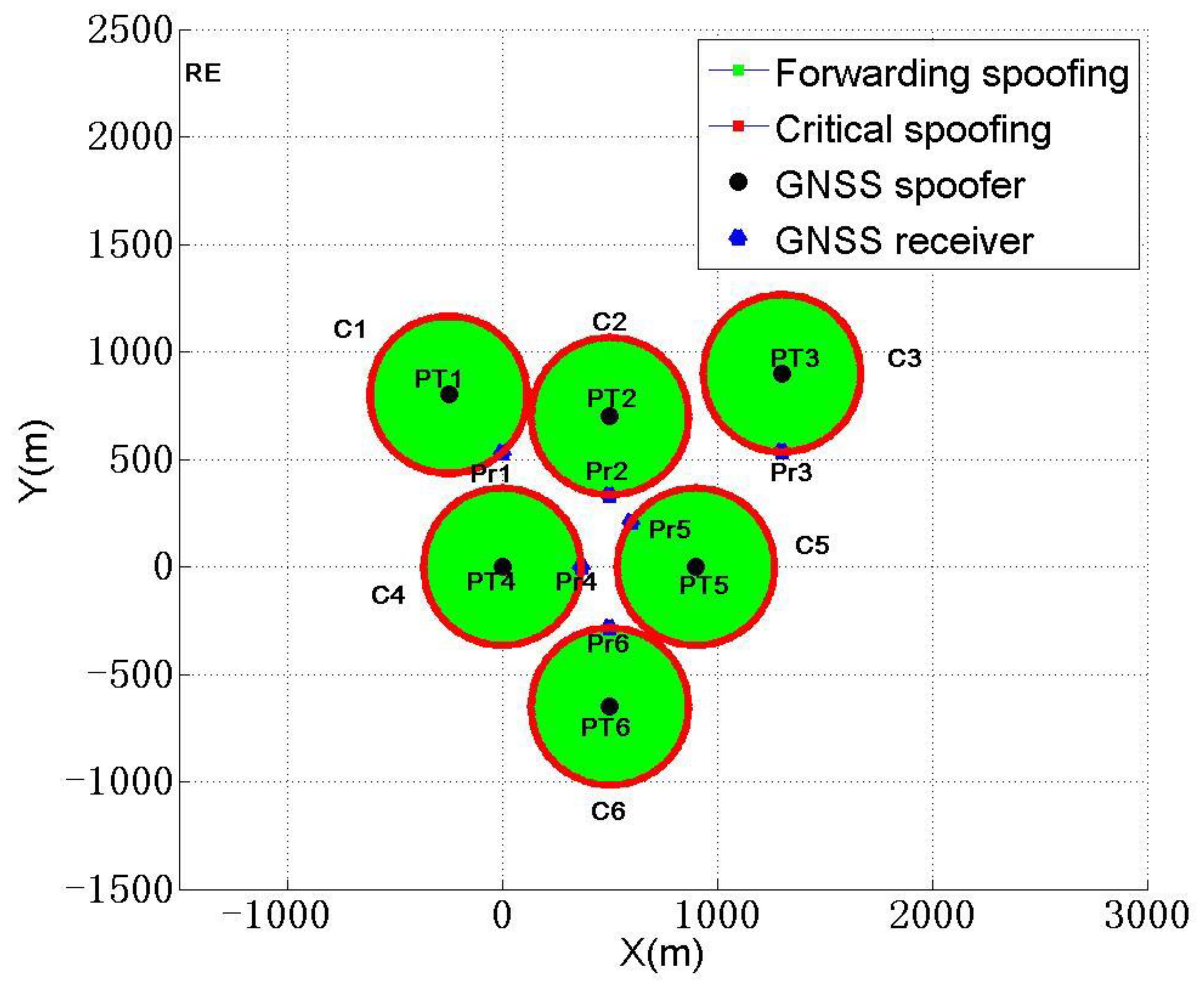 Sensors, Free Full-Text12 março 2025
Sensors, Free Full-Text12 março 2025 -
 Autonomous aerial robotics for package delivery: A technical12 março 2025
Autonomous aerial robotics for package delivery: A technical12 março 2025 -
 Spoofing SaaS Vanity URLs for Social Engineering Attacks12 março 2025
Spoofing SaaS Vanity URLs for Social Engineering Attacks12 março 2025 -
Eulen or redengine? #cheating #eulen #fivem #jus2rich #gaming12 março 2025
-
 Fortune India: Business News, Strategy, Finance and Corporate Insight12 março 2025
Fortune India: Business News, Strategy, Finance and Corporate Insight12 março 2025 -
 Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's12 março 2025
Tactics, Techniques and Procedures (TTPs) Utilized by FireEye's12 março 2025 -
 Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum12 março 2025
Protecting GPS From Spoofers Is Critical to the Future of Navigation - IEEE Spectrum12 março 2025
você pode gostar
-
 Close up of road map detail of Tavira city in Algarve, Portugal12 março 2025
Close up of road map detail of Tavira city in Algarve, Portugal12 março 2025 -
 Gráfico de Pokémon Lizard elétrico · Creative Fabrica12 março 2025
Gráfico de Pokémon Lizard elétrico · Creative Fabrica12 março 2025 -
Reply to @xjiemomostan the music of this song is by the same12 março 2025
-
 Tottenham Hotspur FC. - Chess Club12 março 2025
Tottenham Hotspur FC. - Chess Club12 março 2025 -
 Jogo de trilha: Patrulha Canina12 março 2025
Jogo de trilha: Patrulha Canina12 março 2025 -
 Max Payne Mobile Coming to iOS Devices on April 12th and Android Devices on April 26th - Rockstar Games12 março 2025
Max Payne Mobile Coming to iOS Devices on April 12th and Android Devices on April 26th - Rockstar Games12 março 2025 -
 Call of Duty 2 - PC CD-Rom Computer game + case 503091703188512 março 2025
Call of Duty 2 - PC CD-Rom Computer game + case 503091703188512 março 2025 -
 Listen to Do You Love Rasqueado? podcast12 março 2025
Listen to Do You Love Rasqueado? podcast12 março 2025 -
 Nikke Codes (CD Keys) - December 202312 março 2025
Nikke Codes (CD Keys) - December 202312 março 2025 -
 Inglaterra x França, Quartas de final, Copa do Mundo FIFA de 2022, no Qatar, Jogo completo12 março 2025
Inglaterra x França, Quartas de final, Copa do Mundo FIFA de 2022, no Qatar, Jogo completo12 março 2025

