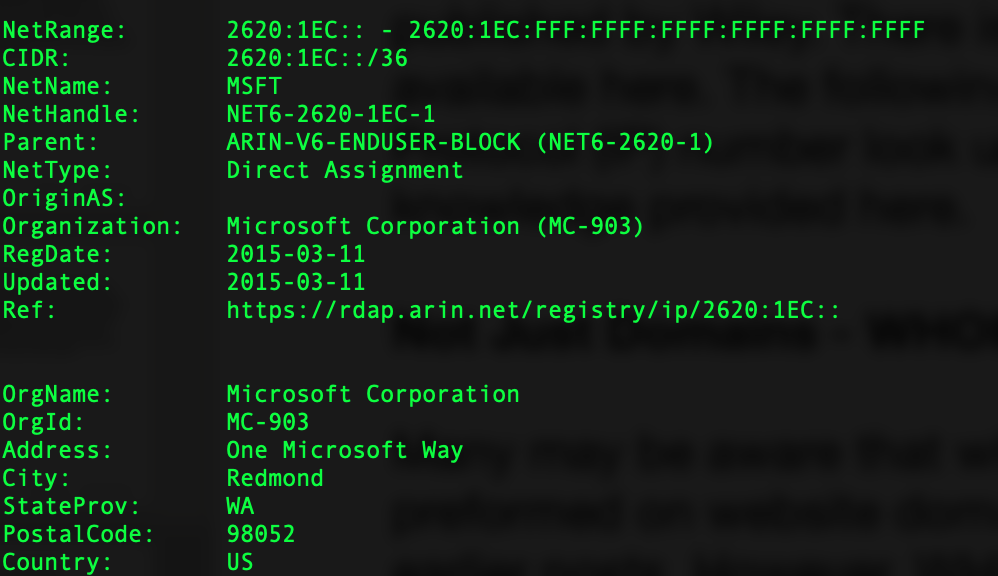
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
Por um escritor misterioso
Last updated 23 fevereiro 2025
Did you know that the Secure Shell protocol, better known as SSH, is not as secure as its name suggests? In this post I show you different ways to attack this protocol. %

Killnet Claim They've Stolen Employee Data from Lockheed Martin

Hackbun

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)

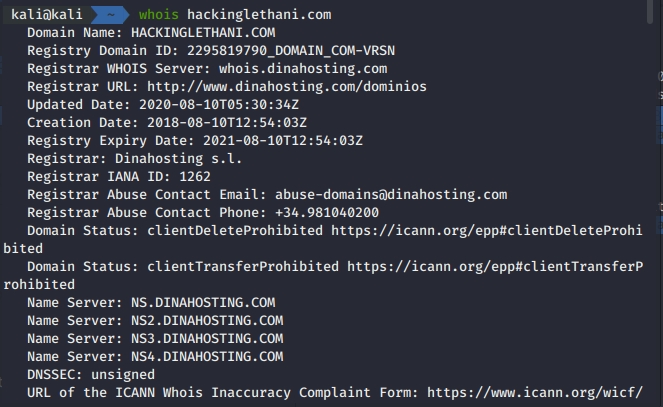
Infrastructure Hacking: WHOIS Protocol » Hacking Lethani
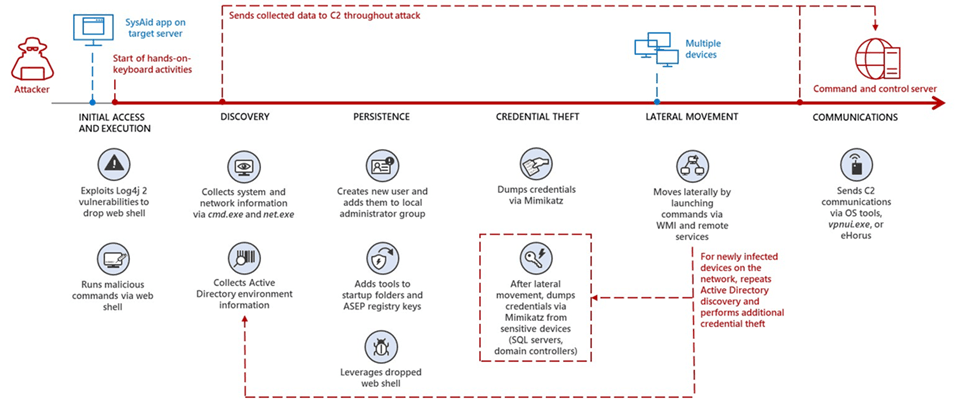
Microsoft: Nation-state Iranian hackers exploit Log4Shell against Israel

Hacking Tutorial - Ethical Hacking Tutorial - Wikitechy

Tips for Investigating Cybercrime Infrastructure
Is Foundational Knowledge (Networking, Coding, Linux) Really That Important When Learning to Hack?

Ethical Hacking Learning Path — A Complete Roadmap, by crawsecurity

Cyber Security & Ethical Hacking - Whois ( “who owns a domain?”)
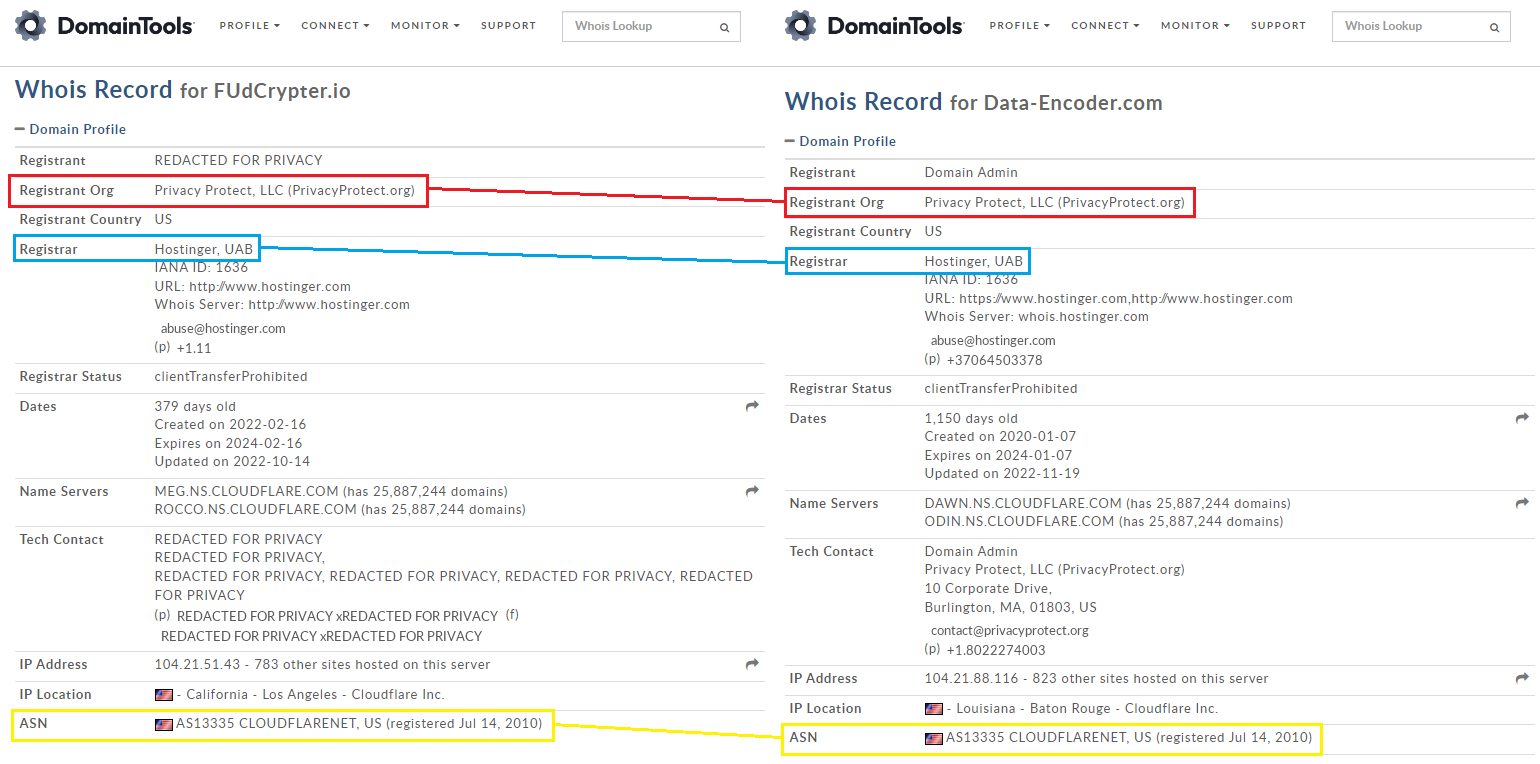
Tips for Investigating Cybercrime Infrastructure

Understanding Linux Privilege Escalation: Tips to Improve Cy

Tips for Investigating Cybercrime Infrastructure
Recomendado para você
-
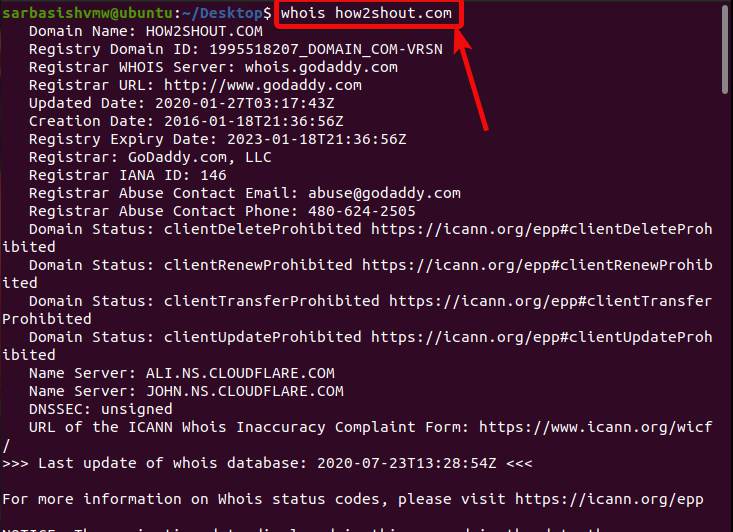 How to use the Whois command on Linux to see domain information on23 fevereiro 2025
How to use the Whois command on Linux to see domain information on23 fevereiro 2025 -
 What Is Whois Lookup And How Can It Help You? - Monsterhost23 fevereiro 2025
What Is Whois Lookup And How Can It Help You? - Monsterhost23 fevereiro 2025 -
Internet Protocol(IP) WHOIS23 fevereiro 2025
-
 What is WHOIS and How Does it Work? (+ Tips on Free Domain Privacy)23 fevereiro 2025
What is WHOIS and How Does it Work? (+ Tips on Free Domain Privacy)23 fevereiro 2025 -
 How To Use WHOIS From The Windows Command Prompt23 fevereiro 2025
How To Use WHOIS From The Windows Command Prompt23 fevereiro 2025 -
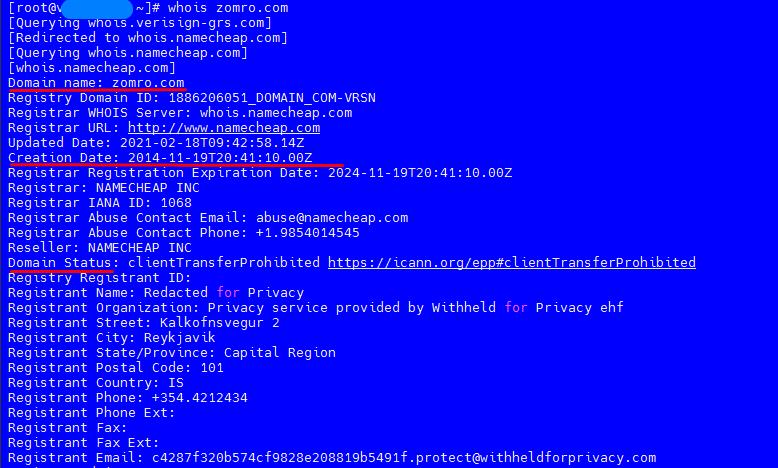 How to see whois of a domain23 fevereiro 2025
How to see whois of a domain23 fevereiro 2025 -
 Whois IP Lookup – free online whois tool23 fevereiro 2025
Whois IP Lookup – free online whois tool23 fevereiro 2025 -
 Try the new IANA WHOIS server23 fevereiro 2025
Try the new IANA WHOIS server23 fevereiro 2025 -
 Whois Hosting - Free Whois Domain Lookup Tool23 fevereiro 2025
Whois Hosting - Free Whois Domain Lookup Tool23 fevereiro 2025 -
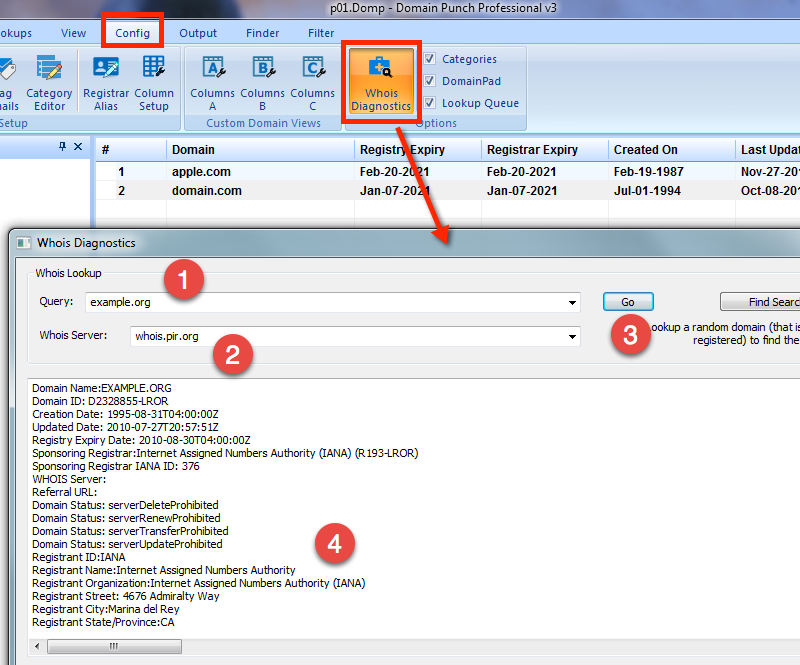 Using the Diagnostic Port 43 Whois Tool23 fevereiro 2025
Using the Diagnostic Port 43 Whois Tool23 fevereiro 2025
você pode gostar
-
meme fino señores significado| TikTok23 fevereiro 2025
-
Gaming Wallpapers HD & 4K - Apps on Google Play23 fevereiro 2025
-
 Melanie Martinez - 'SOAP' (ft. Jiafei, cupcaKKe, Noseporque111) (Color Coded Lyrics), Real-Time Video View Count23 fevereiro 2025
Melanie Martinez - 'SOAP' (ft. Jiafei, cupcaKKe, Noseporque111) (Color Coded Lyrics), Real-Time Video View Count23 fevereiro 2025 -
 Purgatory Onigiri One Piece23 fevereiro 2025
Purgatory Onigiri One Piece23 fevereiro 2025 -
 Telha Metálica Ondulada AT 17/98023 fevereiro 2025
Telha Metálica Ondulada AT 17/98023 fevereiro 2025 -
 Depois Estacionar Carro Vermelho Lugar Estacionamento Automated Guided Vehicle Agv fotos, imagens de © chesky_w #18012835023 fevereiro 2025
Depois Estacionar Carro Vermelho Lugar Estacionamento Automated Guided Vehicle Agv fotos, imagens de © chesky_w #18012835023 fevereiro 2025 -
 Mequinho - Superinteressante - Vini Capiotti - Portfolio23 fevereiro 2025
Mequinho - Superinteressante - Vini Capiotti - Portfolio23 fevereiro 2025 -
What did Eren Yeager tell Grisha Yeager with his Titan ability to communicate through future memories in Attack on Titan? - Quora23 fevereiro 2025
-
 Pin on camisas para roblox23 fevereiro 2025
Pin on camisas para roblox23 fevereiro 2025 -
 Minas tirith hi-res stock photography and images - Alamy23 fevereiro 2025
Minas tirith hi-res stock photography and images - Alamy23 fevereiro 2025