PDF] Power Consumption-based Detection of Sabotage Attacks in
Por um escritor misterioso
Last updated 12 março 2025
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/4-Figure1-1.png)
This work proposes a novel approach for detecting sabotage attacks in additive Manufacturing, based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. Additive Manufacturing (AM), a.k.a. 3D Printing, is increasingly used to manufacture functional parts of safety-critical systems. AM's dependence on computerization raises the concern that the AM process can be tampered with, and a part's mechanical properties sabotaged. This can lead to the destruction of a system employing the sabotaged part, causing loss of life, financial damage, and reputation loss. To address this threat, we propose a novel approach for detecting sabotage attacks. Our approach is based on continuous monitoring of the current delivered to all actuators during the manufacturing process and detection of deviations from a provable benign process. The proposed approach has numerous advantages: (i) it is non-invasive in a time-critical process, (ii) it can be retrofitted in legacy systems, and (iii) it is airgapped from the computerized components of the AM process, preventing simultaneous compromise. Evaluation on a desktop 3D Printer detects all attacks involving a modification of X or Y motor movement, with false positives at 0%.
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://miro.medium.com/v2/resize:fit:1400/1*QRr8b1klMwCgYlkuCObyYg.png)
How to attack Machine Learning ( Evasion, Poisoning, Inference, Trojans, Backdoors), by Alex Polyakov
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.licdn.com/dms/image/D5622AQGDAgD1PaMQkA/feedshare-shrink_2048_1536/0/1692244400400?e=1704931200&v=beta&t=kcHoyCYqrFLbp4CuTkFuI4T-Me1TpQ5_vAdkG23noZ4)
Rashedul Islam on LinkedIn: #cybercrime #cybersecurity #mitm #cyberarmy #networksecurity
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/9-Figure3-1.png)
PDF] Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://image.slidesharecdn.com/fy16q1symantecfullwstr-150623202549-lva1-app6891/85/technical-white-paper-symantec-website-security-threat-report-1-320.jpg?cb=1668658630)
TECHNICAL WHITE PAPER▷ Symantec Website Security Threat Report
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.springernature.com/m685/springer-static/image/art%3A10.1186%2Fs42400-020-00050-w/MediaObjects/42400_2020_50_Fig1_HTML.png)
Review and insight on the behavioral aspects of cybersecurity, Cybersecurity
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://ik.imagekit.io/po8th4g4eqj/prod/tr:w-1168/power-lines-1168-440.jpg)
Preparing for Greyzone Threats to the Energy Sector
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.tandfonline.com/cms/asset/df6e38b5-c80d-4264-8c5d-ee36045dbe67/tsma_a_1972914_uf0001_oc.jpg)
Full article: IoT-Based Intrusion Detection Systems: A Review
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.springernature.com/m685/springer-static/image/art%3A10.1038%2Fs41598-022-12181-w/MediaObjects/41598_2022_12181_Fig1_HTML.png)
An energy-aware and Q-learning-based area coverage for oil pipeline monitoring systems using sensors and Internet of Things
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://www.frontiersin.org/files/Articles/591999/fenrg-08-591999-HTML-r1/image_m/fenrg-08-591999-g001.jpg)
Frontiers Using Design Thinking to Understand Cyber Attack Surfaces of Future Smart Grids
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://media.springernature.com/m685/springer-static/image/art%3A10.1186%2Fs42400-019-0038-7/MediaObjects/42400_2019_38_Fig2_HTML.png)
Survey of intrusion detection systems: techniques, datasets and challenges, Cybersecurity
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://d3i71xaburhd42.cloudfront.net/d81c8d2816032b4abc1798383f88d5a376d17a75/9-Table1-1.png)
PDF] Power Consumption-based Detection of Sabotage Attacks in Additive Manufacturing
![PDF] Power Consumption-based Detection of Sabotage Attacks in](https://pubs.acs.org/cms/10.1021/acsnano.1c10635/asset/images/acsnano.1c10635.social.jpeg_v03)
Nanotechnology Tools Enabling Biological Discovery
Recomendado para você
-
![New Cura [4.2.1]: Extruder start g-code executed on start · Issue](https://user-images.githubusercontent.com/1018316/64303189-97a2be00-cf4c-11e9-8815-1ebbf52f86ac.png) New Cura [4.2.1]: Extruder start g-code executed on start · Issue12 março 2025
New Cura [4.2.1]: Extruder start g-code executed on start · Issue12 março 2025 -
 gcode experts - Software - LulzBot12 março 2025
gcode experts - Software - LulzBot12 março 2025 -
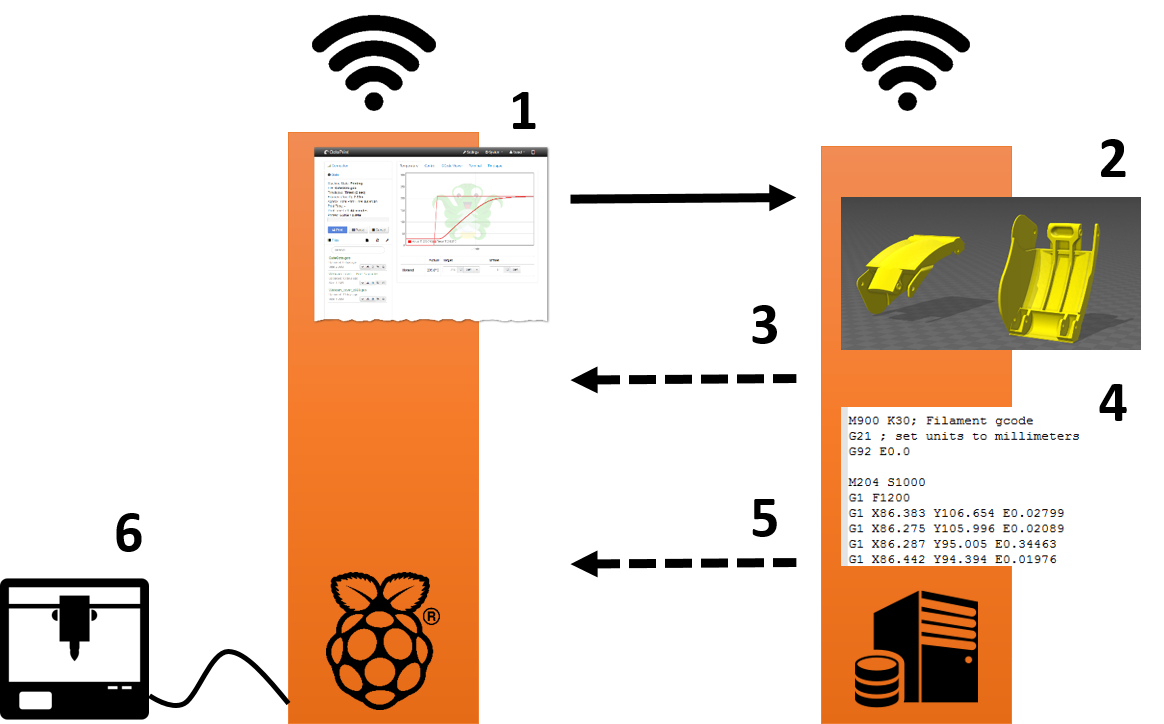 OctoPrint-PrePrintService12 março 2025
OctoPrint-PrePrintService12 março 2025 -
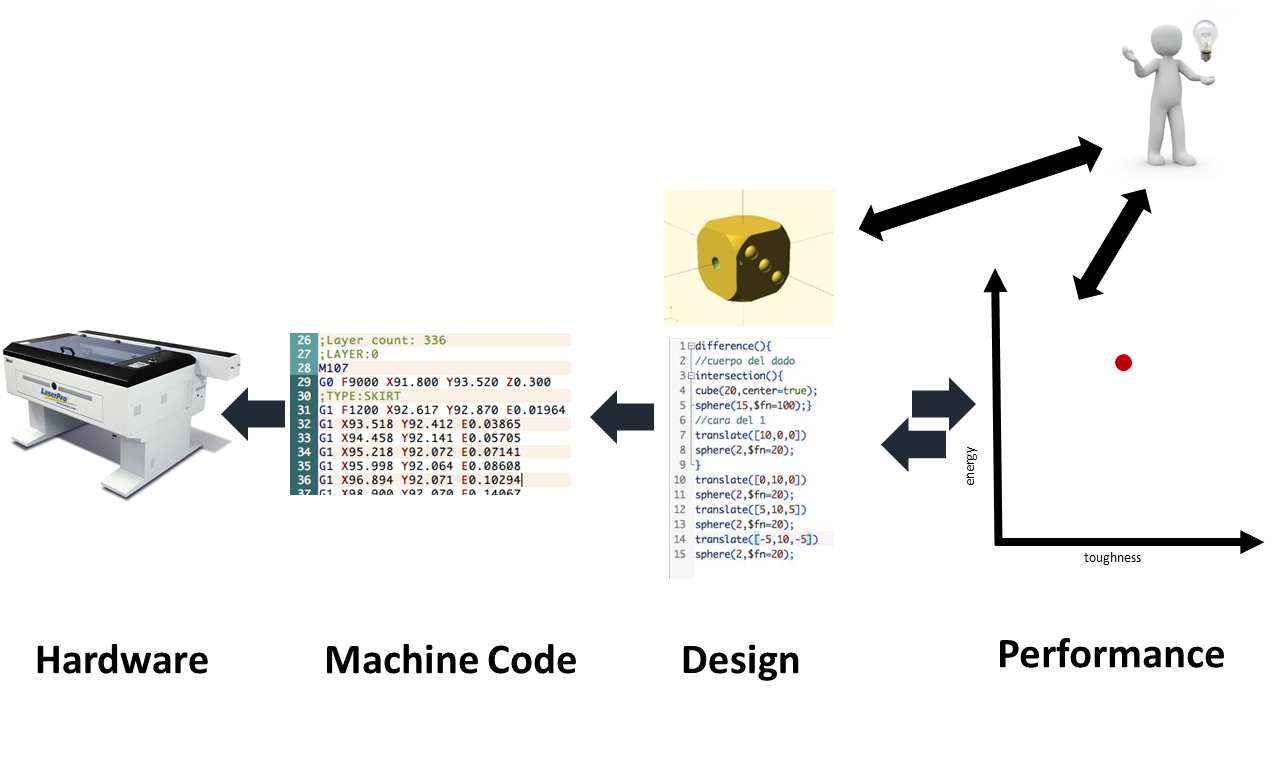 Computational Fabrication12 março 2025
Computational Fabrication12 março 2025 -
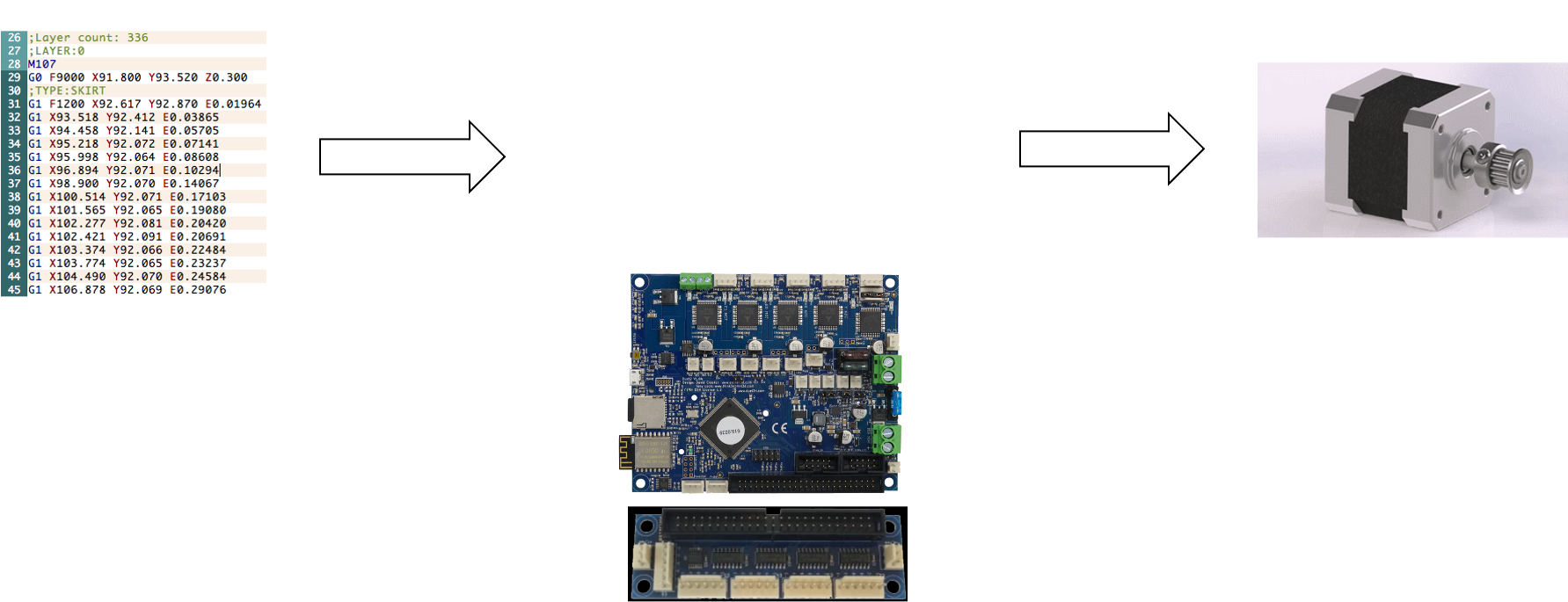 Noa Samarelli12 março 2025
Noa Samarelli12 março 2025 -
 3D Printing Relief : 4 Steps - Instructables12 março 2025
3D Printing Relief : 4 Steps - Instructables12 março 2025 -
 ultimaker cura - How center the nozzle before start printing - 3D12 março 2025
ultimaker cura - How center the nozzle before start printing - 3D12 março 2025 -
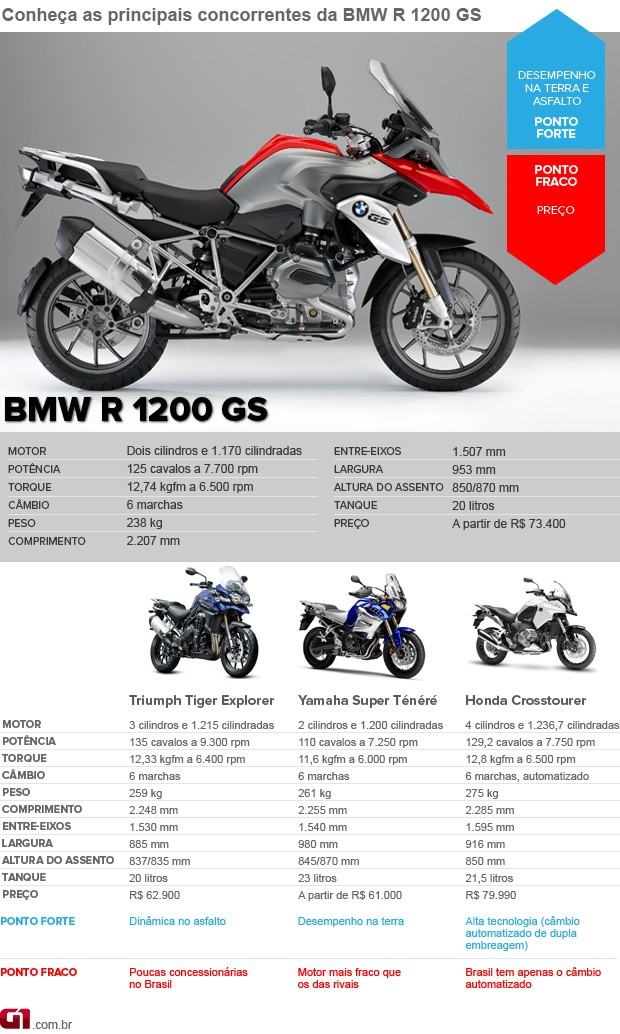 G1 - Primeiras impressões: nova geração da BMW R 1200 GS12 março 2025
G1 - Primeiras impressões: nova geração da BMW R 1200 GS12 março 2025 -
 ultimaker cura - How center the nozzle before start printing - 3D Printing Stack Exchange12 março 2025
ultimaker cura - How center the nozzle before start printing - 3D Printing Stack Exchange12 março 2025 -
4.5.0] Layer height Z-move change applied after Z-Hop When Retracted move · Issue #7320 · Ultimaker/Cura · GitHub12 março 2025
você pode gostar
-
 Pokéarth - Kanto - Route 112 março 2025
Pokéarth - Kanto - Route 112 março 2025 -
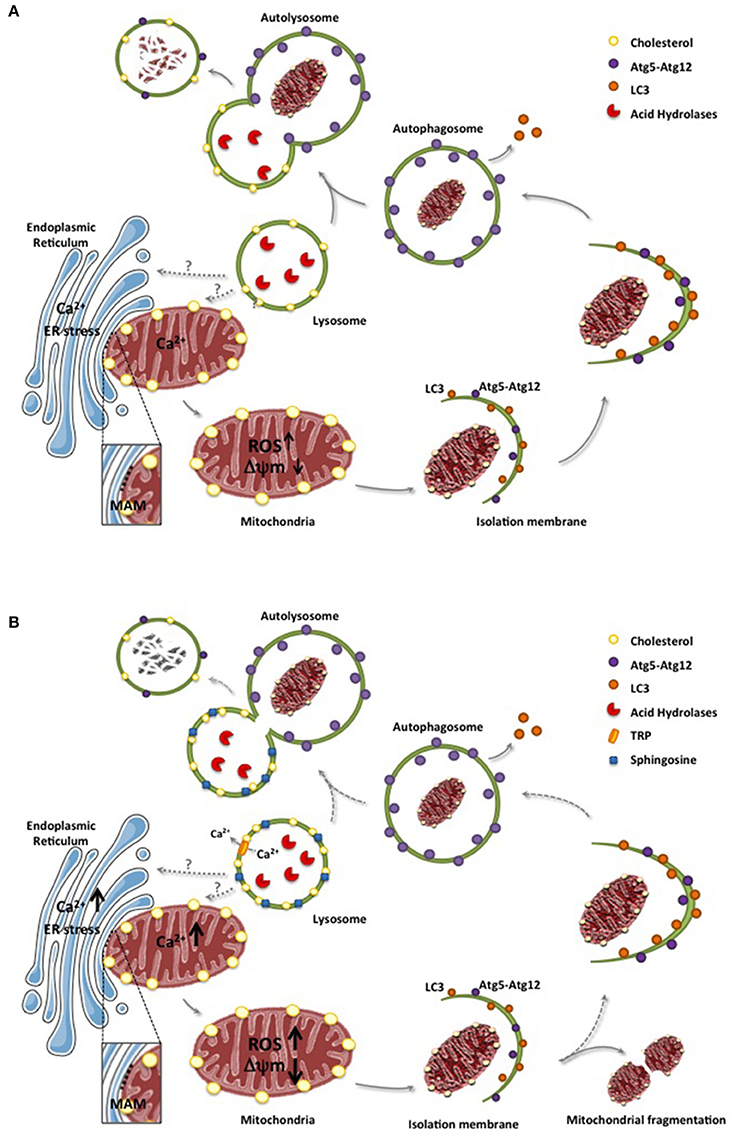 Frontiers Lysosomal and Mitochondrial Liaisons in Niemann-Pick12 março 2025
Frontiers Lysosomal and Mitochondrial Liaisons in Niemann-Pick12 março 2025 -
 Como instalar/jogar FNaF Doom no Android12 março 2025
Como instalar/jogar FNaF Doom no Android12 março 2025 -
 Speed Hub Blox Fruits Script Download Now 100% Free12 março 2025
Speed Hub Blox Fruits Script Download Now 100% Free12 março 2025 -
 Dryy adlı kullanıcının Destaques Instagram panosundaki Pin12 março 2025
Dryy adlı kullanıcının Destaques Instagram panosundaki Pin12 março 2025 -
 Sold at Auction: GIANNINI 1900 SERIES MPB GCSM-31 TENOR UKULELE12 março 2025
Sold at Auction: GIANNINI 1900 SERIES MPB GCSM-31 TENOR UKULELE12 março 2025 -
Kauani Colpani - Estagiária - Renault Group12 março 2025
-
Quiz Time💪#foryou #quiztime #fypシ゚viral #generalknowledge #biologyqui12 março 2025
-
 Play Folclore Português by Grupo Norte Sul on Music12 março 2025
Play Folclore Português by Grupo Norte Sul on Music12 março 2025 -
 Scaredy Cat (2020) - Filmaffinity12 março 2025
Scaredy Cat (2020) - Filmaffinity12 março 2025

