Kung fu enumeration. Data collection in attacked systems – HackMag
Por um escritor misterioso
Last updated 22 abril 2025

HACKMAGEDDON – Information Security Timelines and Statistics
Kung fu enumeration. Data collection in attacked systems – HackMag

Xiangyu Qi - CatalyzeX
Kung fu enumeration. Data collection in attacked systems – HackMag

CTF Challenges TryHackMe CTF collection Vol.1 Part 3
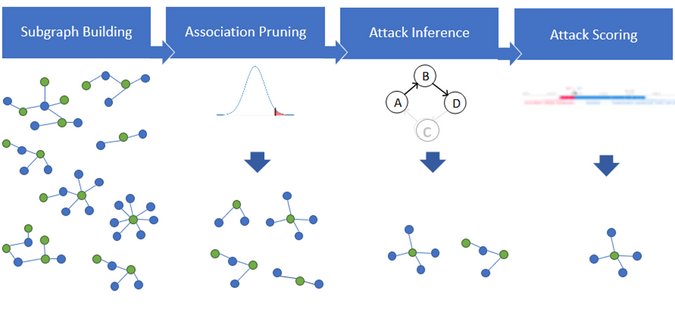
Behind the Scenes: The ML Approach for Detecting Advanced

Hakka Fist Snapping Claws - Technique and Applications - Kung Fu

HACKMAGEDDON – Information Security Timelines and Statistics

Machine Learning under Malware Attack
Find out if you have what it takes to keep the bad guys out of your network. This real-world resource contains 20+ hacking challenges for you to

Hacker's Challenge : Test Your Incident Response Skills Using 20 Scenarios

August 2022 Cyber Attacks Statistics – HACKMAGEDDON

Hammond - Unit 17 Homework - GoodSecurity Penetration Test
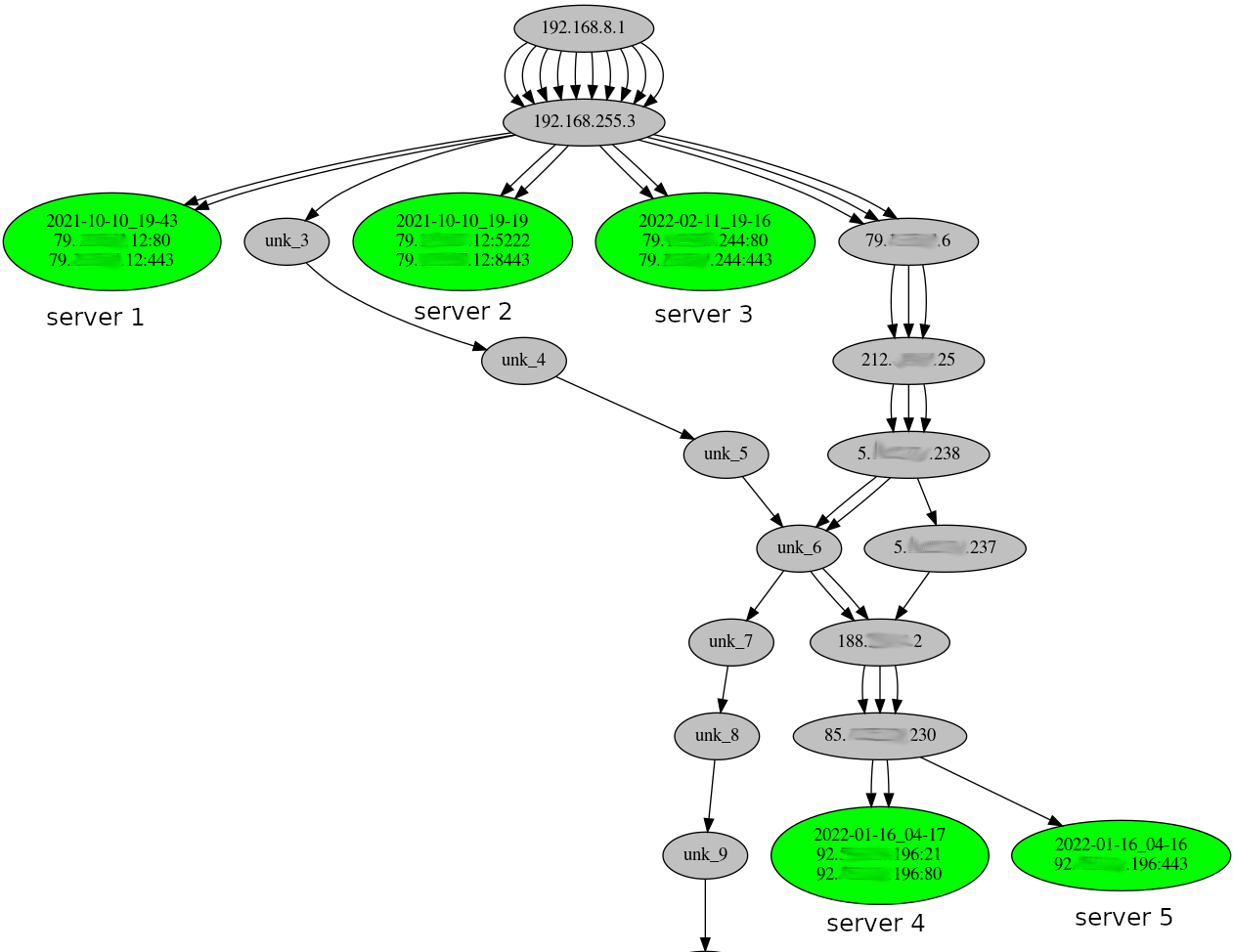
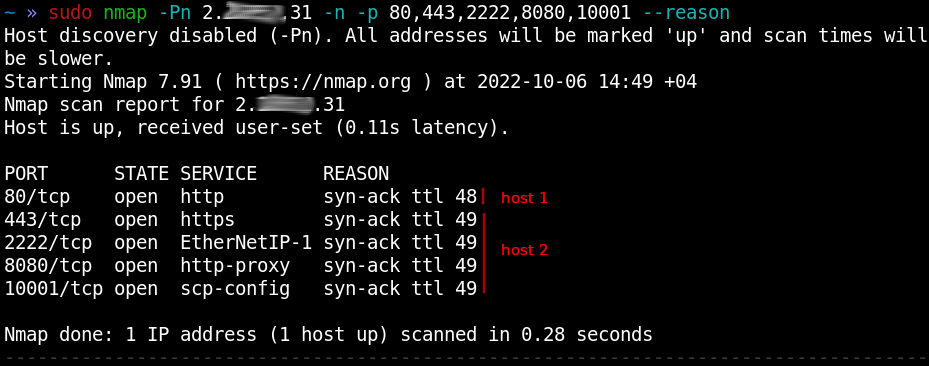
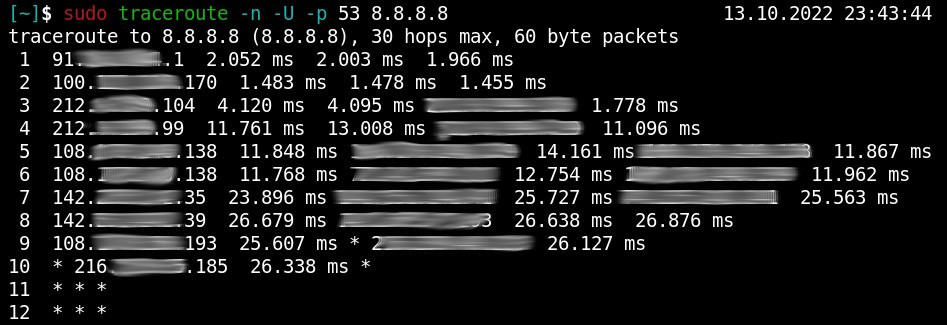
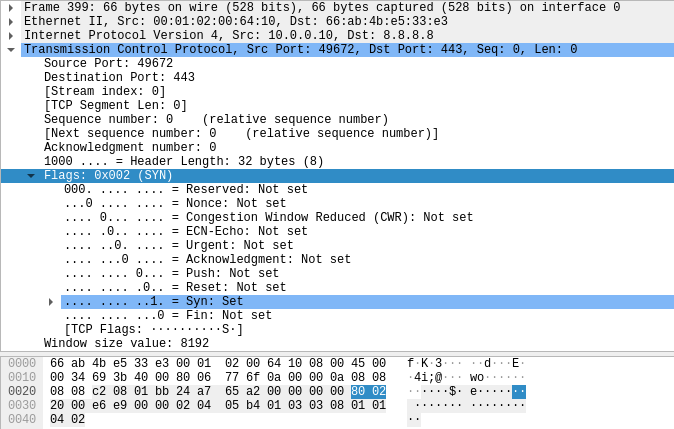
Kung fu enumeration. Data collection in attacked systems – HackMag
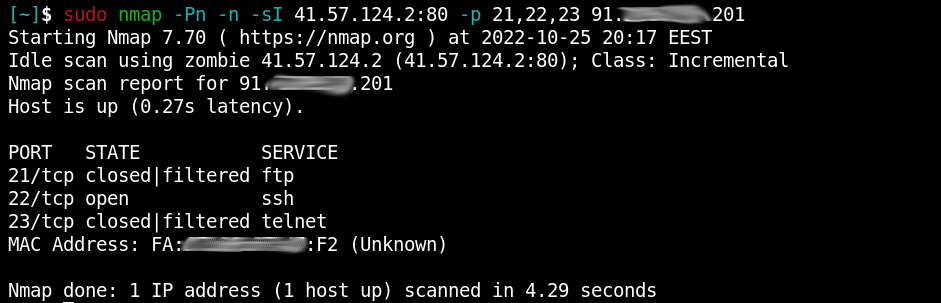
Kung fu enumeration. Data collection in attacked systems – HackMag
Recomendado para você
-
 SCP ref by Silverfang10001 on DeviantArt22 abril 2025
SCP ref by Silverfang10001 on DeviantArt22 abril 2025 -
 SCP-5772 - SCP Foundation22 abril 2025
SCP-5772 - SCP Foundation22 abril 2025 -
 Internal Chats of a Conti Ransomware Group Exposed22 abril 2025
Internal Chats of a Conti Ransomware Group Exposed22 abril 2025 -
 SCP--KARMA:. by XenomorphicDragon on DeviantArt22 abril 2025
SCP--KARMA:. by XenomorphicDragon on DeviantArt22 abril 2025 -
 10001% correct view of the AFSPECWAR career fields : r/Pararescue22 abril 2025
10001% correct view of the AFSPECWAR career fields : r/Pararescue22 abril 2025 -
The SCP Foundation22 abril 2025
-
 27/3 Seaguy Week! Captain Lotharius - Xanaduum22 abril 2025
27/3 Seaguy Week! Captain Lotharius - Xanaduum22 abril 2025 -
 Hailey Hyeseong – HAILEY YOON22 abril 2025
Hailey Hyeseong – HAILEY YOON22 abril 2025 -
 Pre-Pro #1 Boba Fett - Variant - Boba Fett Costume - Boba Fett22 abril 2025
Pre-Pro #1 Boba Fett - Variant - Boba Fett Costume - Boba Fett22 abril 2025 -
 Warrior Woman by Anastasia Kourou, dark Digital Art for sale22 abril 2025
Warrior Woman by Anastasia Kourou, dark Digital Art for sale22 abril 2025
você pode gostar
-
 dreamcore house sketch, Art or something {requests}22 abril 2025
dreamcore house sketch, Art or something {requests}22 abril 2025 -
 Blue Lock chapter 236 release date, time, spoilers, where to read online - The SportsGrail22 abril 2025
Blue Lock chapter 236 release date, time, spoilers, where to read online - The SportsGrail22 abril 2025 -
 Fantasy Premier League: Explaining 'the template' – and why you should back it - The Athletic22 abril 2025
Fantasy Premier League: Explaining 'the template' – and why you should back it - The Athletic22 abril 2025 -
 Pocket Monster Moncolle ML-31 Black Rayquaza Pokemon Takara Tomy Anime Figure JP22 abril 2025
Pocket Monster Moncolle ML-31 Black Rayquaza Pokemon Takara Tomy Anime Figure JP22 abril 2025 -
 Millwall 0-3 Leeds United: Joel Piroe nets twice as Whites register second victory - BBC Sport22 abril 2025
Millwall 0-3 Leeds United: Joel Piroe nets twice as Whites register second victory - BBC Sport22 abril 2025 -
Vi nos Filmes - Anya Taylor Joy. 😋22 abril 2025
-
 New high demand items value chart! : r/RoyaleHighTrading22 abril 2025
New high demand items value chart! : r/RoyaleHighTrading22 abril 2025 -
 Kono subarashii sekai ni shukufuku wo! Minimalist Poster22 abril 2025
Kono subarashii sekai ni shukufuku wo! Minimalist Poster22 abril 2025 -
Esqueça todos os jogos de vídeo bingo que você já jogou e conheça o inovador Champion II um dos jogos mais diferentes e divertidos da internet. Você vai, By Boom-Games22 abril 2025
-
![Rin Nohara [Naruto x Boruto: Ninja Voltage] by Itxchis on DeviantArt](https://images-wixmp-ed30a86b8c4ca887773594c2.wixmp.com/f/7777f2aa-d9e3-425b-820a-95ebbe9fde79/dfjdhrm-b3fa4b79-692e-45b6-aa75-be2203f06ebc.jpg?token=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJzdWIiOiJ1cm46YXBwOjdlMGQxODg5ODIyNjQzNzNhNWYwZDQxNWVhMGQyNmUwIiwiaXNzIjoidXJuOmFwcDo3ZTBkMTg4OTgyMjY0MzczYTVmMGQ0MTVlYTBkMjZlMCIsIm9iaiI6W1t7InBhdGgiOiJcL2ZcLzc3NzdmMmFhLWQ5ZTMtNDI1Yi04MjBhLTk1ZWJiZTlmZGU3OVwvZGZqZGhybS1iM2ZhNGI3OS02OTJlLTQ1YjYtYWE3NS1iZTIyMDNmMDZlYmMuanBnIn1dXSwiYXVkIjpbInVybjpzZXJ2aWNlOmZpbGUuZG93bmxvYWQiXX0.aiXehkQkKK075ckH-V46WcjVAUKvVIDiyZMa-2B-NU0) Rin Nohara [Naruto x Boruto: Ninja Voltage] by Itxchis on DeviantArt22 abril 2025
Rin Nohara [Naruto x Boruto: Ninja Voltage] by Itxchis on DeviantArt22 abril 2025


