Malware analysis generator-no-survey-no-human-verification-2022-01-12 Malicious activity
Por um escritor misterioso
Last updated 04 fevereiro 2025

A Review on Malware Analysis for IoT and Android System

Cycle‐Consistent Generative Adversarial Network and Crypto Hash Signature Token‐based Block chain Technology for Data Aggregation with Secured Routing in Wireless Sensor Networks - Janarthanan - International Journal of Communication Systems - Wiley
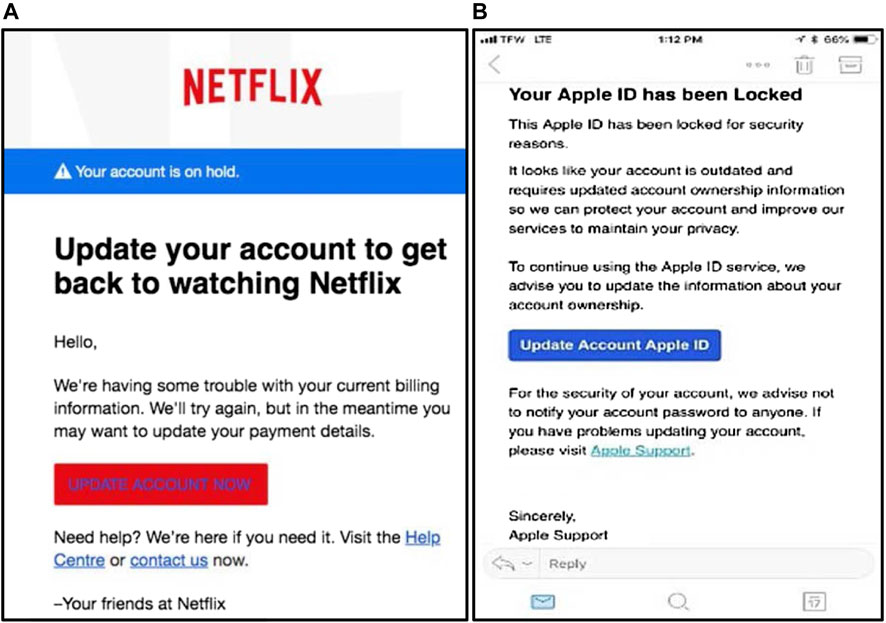
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

TryHackMe : AOC 2022 [Day 12] Malware Analysis Forensic McBlue to the REVscue!, by JAMS_
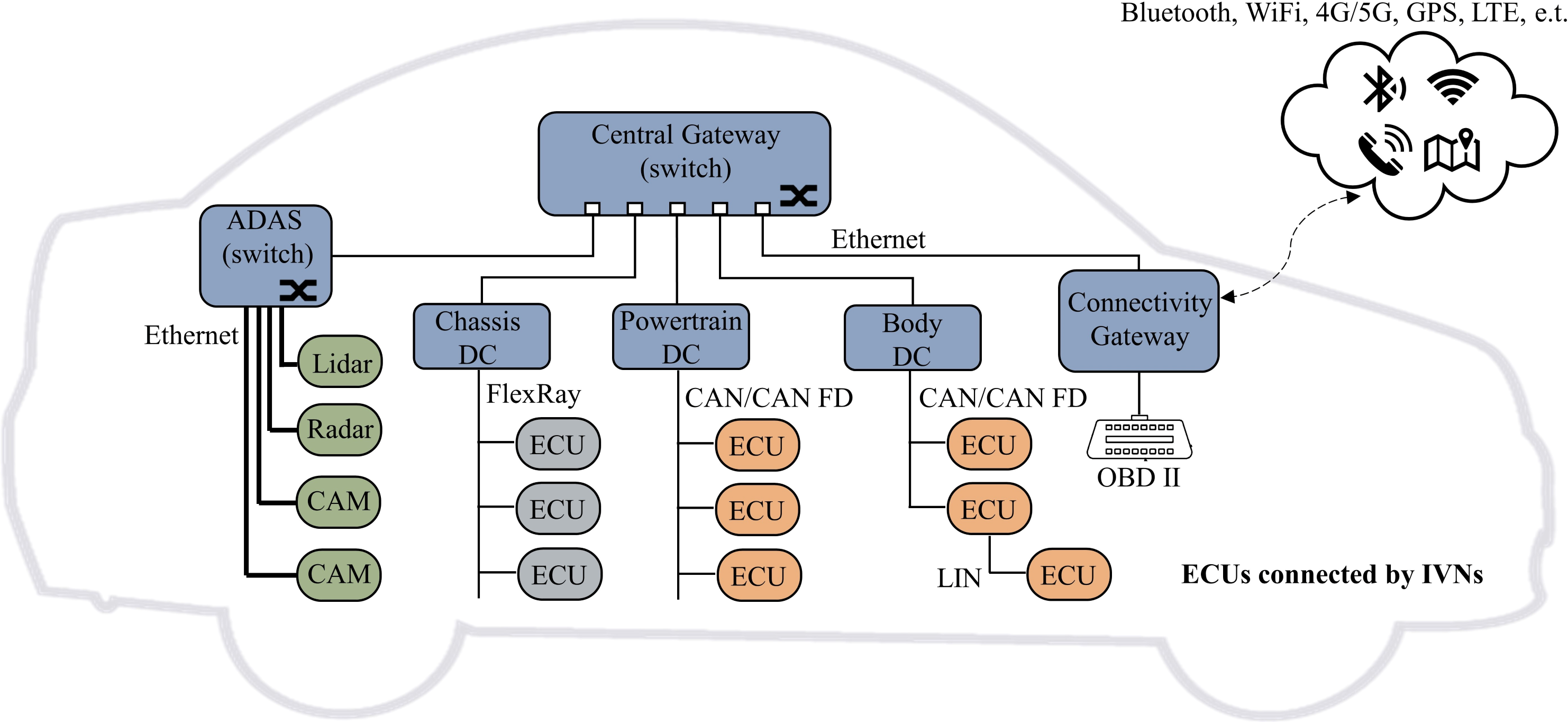
In-vehicle network intrusion detection systems: a systematic survey of deep learning-based approaches [PeerJ]
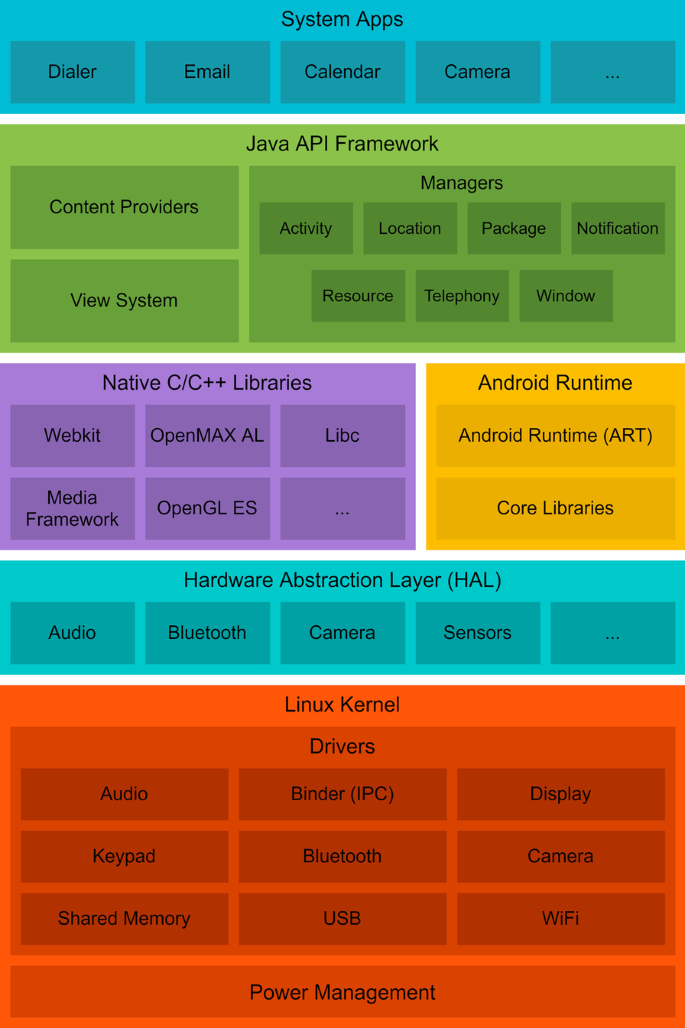
On building machine learning pipelines for Android malware detection: a procedural survey of practices, challenges and opportunities, Cybersecurity

Disarming visualization-based approaches in malware detection systems - ScienceDirect

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

Machine learning in cybersecurity: a comprehensive survey - Dipankar Dasgupta, Zahid Akhtar, Sajib Sen, 2022

Disarming visualization-based approaches in malware detection systems - ScienceDirect

PDF) Accurate and Robust Malware Analysis through Similarity of External Calls Dependency Graphs (ECDG)
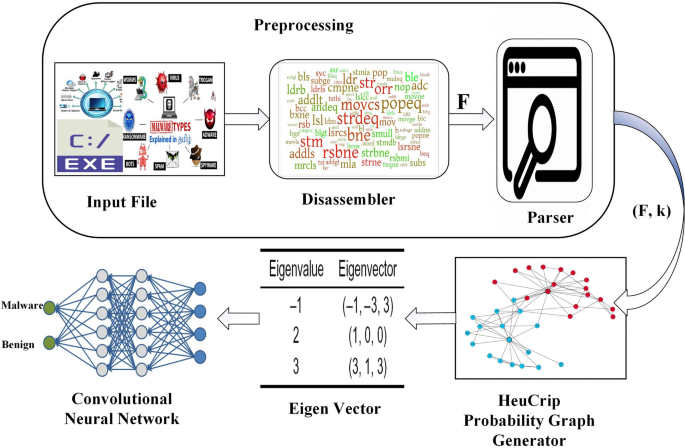
HeuCrip: a malware detection approach for internet of battlefield things

A Comprehensive Survey of Recent Internet Measurement Techniques for Cyber Security - ScienceDirect
CTO/CIO Archives • TechNotes Blog
Recomendado para você
-
How to get free Robux on Roblox 2021 without any survey or human verification - Quora04 fevereiro 2025
-
FREE=] Roblox Robux-Generator 202304 fevereiro 2025
-
![Roblox] Robux Generator No Survey - Get Unlimited Free Robux 2022](https://i.pinimg.com/736x/3e/b6/0a/3eb60a73eee79c3412388a3b049d58d0.jpg) Roblox] Robux Generator No Survey - Get Unlimited Free Robux 202204 fevereiro 2025
Roblox] Robux Generator No Survey - Get Unlimited Free Robux 202204 fevereiro 2025 -
how to get a free robux gift card code roblox codes no human04 fevereiro 2025
-
 how-to-score-match-gems-generator-2022-no-human-verification's NFT04 fevereiro 2025
how-to-score-match-gems-generator-2022-no-human-verification's NFT04 fevereiro 2025 -
ROBLOX FREE ROBUX GENERATOR NO VERIFIcaTION [ bHxFkp]04 fevereiro 2025
-
Free Robux Generator No Human Verification - Free Robux no human04 fevereiro 2025
-
 Robux Glitch No Human Verification 202204 fevereiro 2025
Robux Glitch No Human Verification 202204 fevereiro 2025 -
 redeem on temu roblox 2023 summer|TikTok Search04 fevereiro 2025
redeem on temu roblox 2023 summer|TikTok Search04 fevereiro 2025 -
 Getting Started with Docker: Docker Playground04 fevereiro 2025
Getting Started with Docker: Docker Playground04 fevereiro 2025
você pode gostar
-
 Trapt – Overloaded Lyrics04 fevereiro 2025
Trapt – Overloaded Lyrics04 fevereiro 2025 -
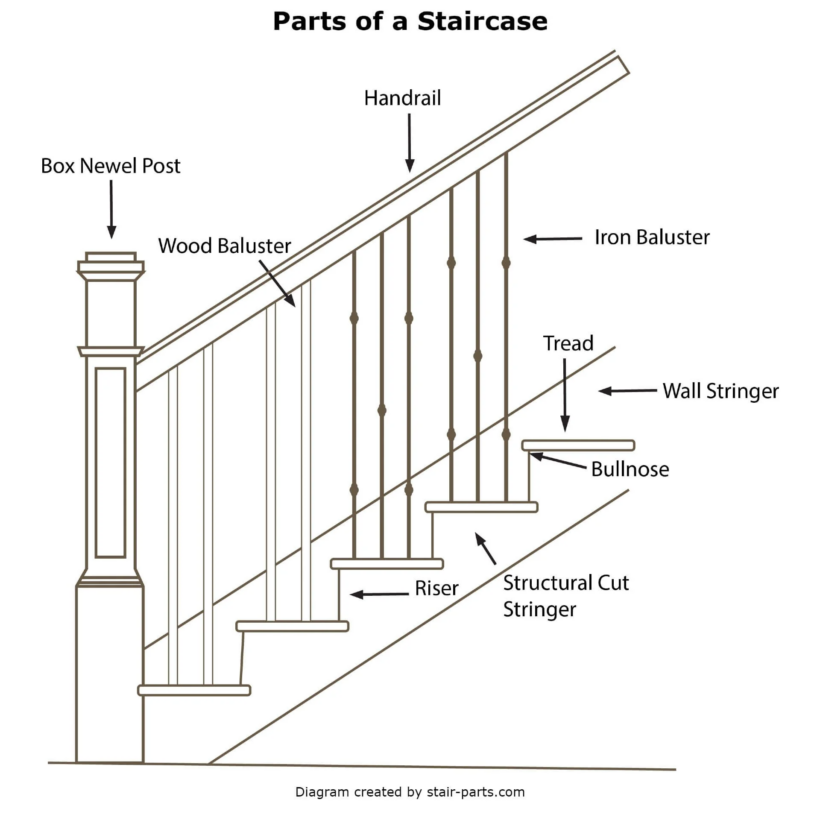 How to Replace Balusters to Update Your Stair Railing04 fevereiro 2025
How to Replace Balusters to Update Your Stair Railing04 fevereiro 2025 -
 Run, Gregory! : r/fivenightsatfreddys04 fevereiro 2025
Run, Gregory! : r/fivenightsatfreddys04 fevereiro 2025 -
Minecraft Dungeons: Seasonal Adventures (Original Game Soundtrack04 fevereiro 2025
-
 Interbens Imóveis, , , SP04 fevereiro 2025
Interbens Imóveis, , , SP04 fevereiro 2025 -
 GTA V: New iFruit App for iOS Overview04 fevereiro 2025
GTA V: New iFruit App for iOS Overview04 fevereiro 2025 -
Iolanda Santos - Analista de Relacionamento - Geekie04 fevereiro 2025
-
 Sonic Adventure 2 HD : Sonic vs Shadow Scene 104 fevereiro 2025
Sonic Adventure 2 HD : Sonic vs Shadow Scene 104 fevereiro 2025 -
 ♟️♟️The Myers Gambit♟️♟️ #chess04 fevereiro 2025
♟️♟️The Myers Gambit♟️♟️ #chess04 fevereiro 2025 -
Tsuki ga michibiku isekai douchuu, #tsukigamichibikuisekaidouchuu #du04 fevereiro 2025
![FREE=] Roblox Robux-Generator 2023](https://media.licdn.com/dms/image/D4E0BAQGM9S-G1M1S_g/company-logo_200_200/0/1700496295619?e=2147483647&v=beta&t=Kw8NEvnFIPLlODByMa15MrR-IqPHuk0_lXdtYYZm18c)




