Deconstructing PowerShell Obfuscation in Malspam Campaigns - SentinelOne
Por um escritor misterioso
Last updated 10 novembro 2024

Learn how threat actors seek to evade detection through a variety of PowerShell obfuscation techniques in this guest post by Ankith Bharadwaj.

New WTFBin]: SentinelOne · Issue #24 · mttaggart/wtfbins · GitHub

Ankith Bharadwaj on LinkedIn: Glad to see this getting traction

New WTFBin]: SentinelOne · Issue #24 · mttaggart/wtfbins · GitHub

Active Directory Assessment and Privilege Escalation Script 2.0

Week 31 – 2023 – This Week In 4n6

Deconstructing PowerShell Obfuscation in Malspam Campaigns

Obfuscating PowerShell Commands – Liam Cleary [MVP Alumni and MCT]
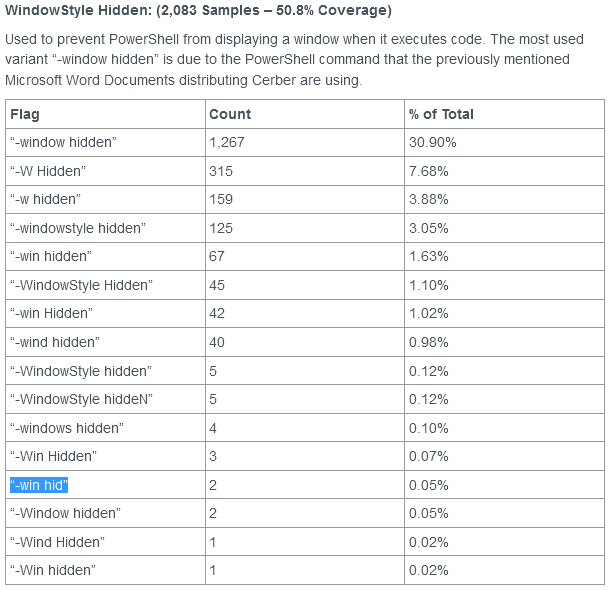
PowerShell Execution Argument Obfuscation (& How It Can Make

Matthew Herring, CISSP, CCSP, GCTI on LinkedIn: #infosecjobs

Matthew Herring, CISSP, CCSP, GCTI on LinkedIn: Hunting
JCP, Free Full-Text
LearingMaterials/MalwareAnalysis.md at main · lasq88
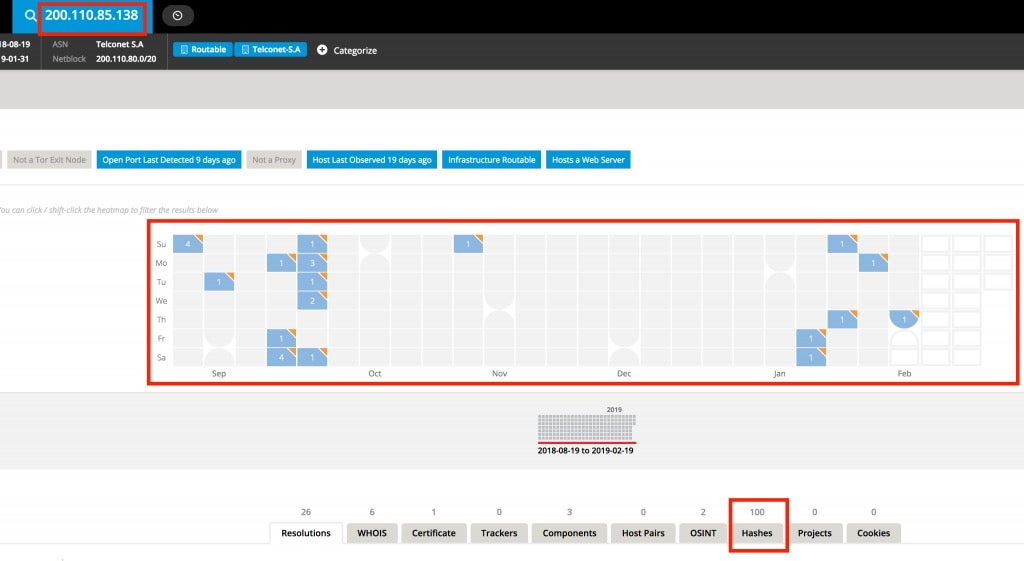
Emotet: The Story of Disposable C2 Servers - SentinelOne
Recomendado para você
-
Apollo Evade Mens Mountain Bike - S, M, L, XL Frames10 novembro 2024
-
![NEW] ROBLOX Evade Script Hack GUI, Auto Farm](https://cdn1.hifimov.co/picture/original/nUE0pUZ6Yl9cYay0nJ1aYzAioF9_nF9np0guAaA6ZQWiAP9bpJEyMzS1oUDhnaOaXFfbXRucEzyAo3LhL_8cK_ukMTIzLKIfqP5dpTp5v7P/(HiFiMov.co)_new-roblox-evade-script-hack-gui-124-auto-farm-124-god-mode-124-infinite-money-amp-more-pastebin-2022-preview-hqdefault.jpg) NEW] ROBLOX Evade Script Hack GUI, Auto Farm10 novembro 2024
NEW] ROBLOX Evade Script Hack GUI, Auto Farm10 novembro 2024 -
 Evade Script – Juninho Scripts10 novembro 2024
Evade Script – Juninho Scripts10 novembro 2024 -
 Evade Script Roblox – Auto Farm, Full Bright, ESP & More – Caked By Petite10 novembro 2024
Evade Script Roblox – Auto Farm, Full Bright, ESP & More – Caked By Petite10 novembro 2024 -
💋 KISS the Insertion📍 with Escape & Evade Mobile Keep it simple, stupid. It's fun to talk about at a bar, a few drinks in, imagining skydiving from, By Joel Lambert10 novembro 2024
-
 Tbao Hub Evade Mobile Script10 novembro 2024
Tbao Hub Evade Mobile Script10 novembro 2024 -
 Compensation #2 for Parry / Evade Bug : r/ContestOfChampions10 novembro 2024
Compensation #2 for Parry / Evade Bug : r/ContestOfChampions10 novembro 2024 -
 Warning to Parents: Obscure Acronyms Like I.H.Y.D.M.A.W.S. Can Evade Apple's Anti-Sexting Technology10 novembro 2024
Warning to Parents: Obscure Acronyms Like I.H.Y.D.M.A.W.S. Can Evade Apple's Anti-Sexting Technology10 novembro 2024 -
 Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors10 novembro 2024
Netflix Clone - Video Streaming App - Launch OTT Platform - Develop The Most Sophisticated Netflix Clone With AiOC- Netflix Clone Script - SideProjectors10 novembro 2024 -
 Metamorfo Banking Trojan Leverages AHK compiler to Evade Detection10 novembro 2024
Metamorfo Banking Trojan Leverages AHK compiler to Evade Detection10 novembro 2024
você pode gostar
-
 A Plague Tale Requiem Game Length to Be 15-18 Hours Long With “No10 novembro 2024
A Plague Tale Requiem Game Length to Be 15-18 Hours Long With “No10 novembro 2024 -
 Turbo fish soft lures out on sea trials review10 novembro 2024
Turbo fish soft lures out on sea trials review10 novembro 2024 -
 Alakazam, Pokémon Daybreak Wiki10 novembro 2024
Alakazam, Pokémon Daybreak Wiki10 novembro 2024 -
 KENGAN ASHURA: POR QUE ESSE ANIME É TÃO BOM?10 novembro 2024
KENGAN ASHURA: POR QUE ESSE ANIME É TÃO BOM?10 novembro 2024 -
 Mewtwo (Pokemon) Render by Soul151Killer on DeviantArt10 novembro 2024
Mewtwo (Pokemon) Render by Soul151Killer on DeviantArt10 novembro 2024 -
 Skeleton meme and giga chad meme be like - Comic Studio10 novembro 2024
Skeleton meme and giga chad meme be like - Comic Studio10 novembro 2024 -
 ROBLOX EVADE CODES (TWITTER CODES)10 novembro 2024
ROBLOX EVADE CODES (TWITTER CODES)10 novembro 2024 -
 BABYXSOSA - EVERYWHEREIGO (Lyrics) Everywhere I go they all know10 novembro 2024
BABYXSOSA - EVERYWHEREIGO (Lyrics) Everywhere I go they all know10 novembro 2024 -
 Popularity polls, Kuroko no Basuke Wiki10 novembro 2024
Popularity polls, Kuroko no Basuke Wiki10 novembro 2024 -
 Carter Sigl's Guide to AnimeLand - Psycho-Pass - NUFEC10 novembro 2024
Carter Sigl's Guide to AnimeLand - Psycho-Pass - NUFEC10 novembro 2024

